After almost an almost non-existent presence in 2017 and a few weeks off, Locky is back with a fresh wave of SPAM emails containing malicious docs. While it is not known what caused Locky’s hiatus, if they plan on pushing the ransomware like they previously did, then we all need to pay close attention.
Locky Distributed Through Malicious PDFs and Word Documents
This current wave of SPAM comes in the form of emails that pretend to be payment receipts with various subjects. According to an article by My Online Security, the email subjects include Receipt 435, Payment Receipt 2724, Payment-2677, Payment Receipt_739, and Payment#229, where the numbers change.
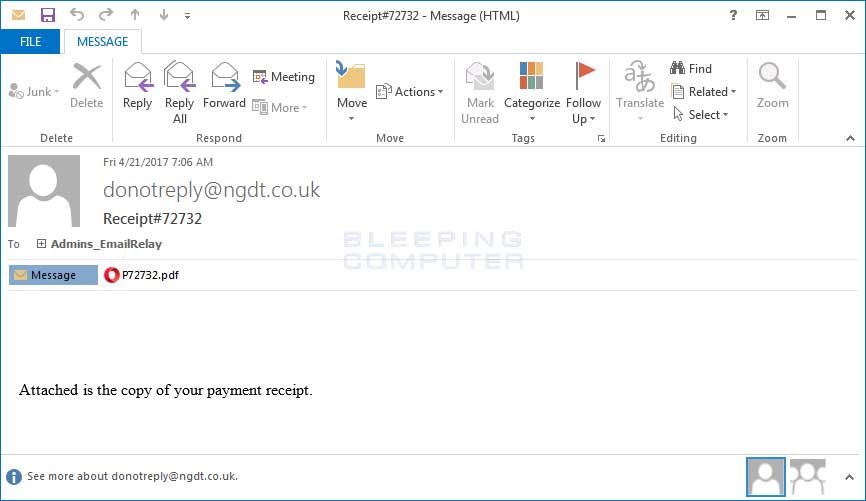
These emails include a PDF attachment with a name like P72732.pdf. When these PDFs are opened, the target will be prompted to open an embedded Word document as shown below.
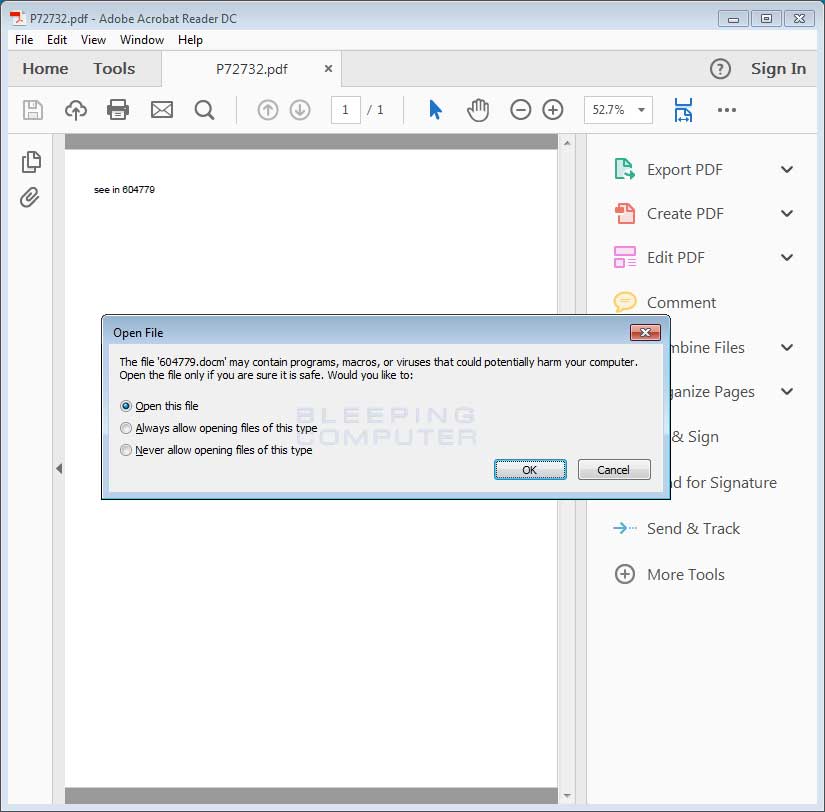
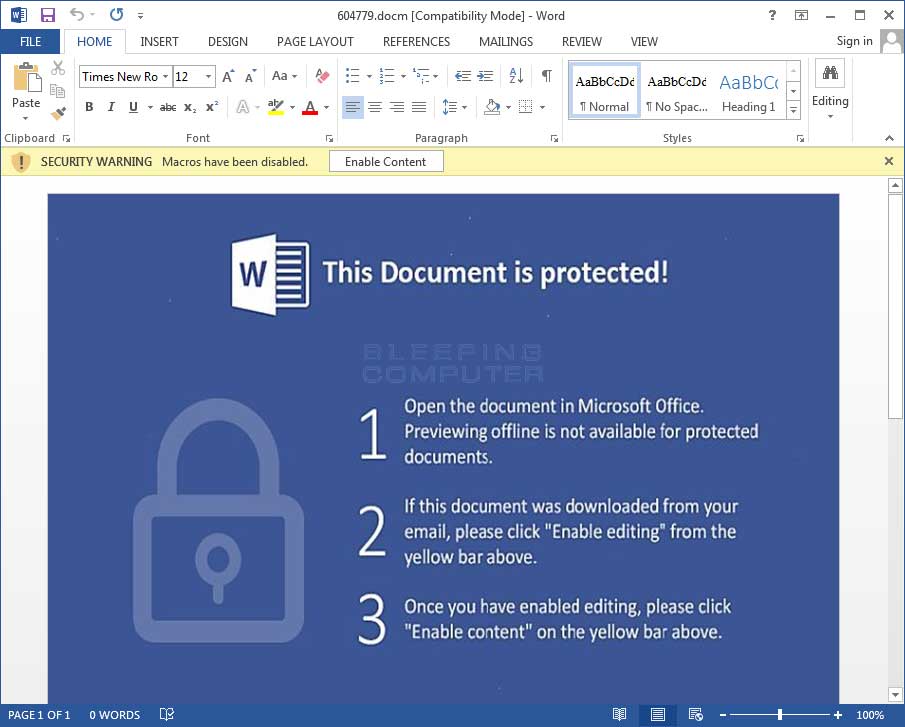
If a user opens the file, the Word document will open and the target will be greeted with the typical Malicious word document prompt. That is the prompting to enable the macros by clicking on Enable Content in order to properly see the document.
When the macros are enabled, the macros are currently downloading an encrypted Locky binary from https://uwdesign.com.br/9yg65, decrypting the file, saving it to %Temp%\redchip2.exe, and then executing the file to begin the encryption process. Redchip2.exe currently has a 7/55 detection on VirusTotal.
Just like previous variants, Locky deletes Shadow Volume Copies using a Scheduled Task and appends the .OSIRIS extension to encrypted files. You can see the task used below.
IgnoreNew
false
false
true
true
false
PT10M
PT1H
true
false
true
true
false
false
false
PT72H
7C:\Windows\system32\vssadmin.exe
Delete Shadows /Quiet /All
While encrypting files it will routinely send status updates to the Command & Control servers located at 188.120.239.230/checkupdate and 80.85.158.212/checkupdate. When done it will display the ransom note to let the victim know that they have been infected.
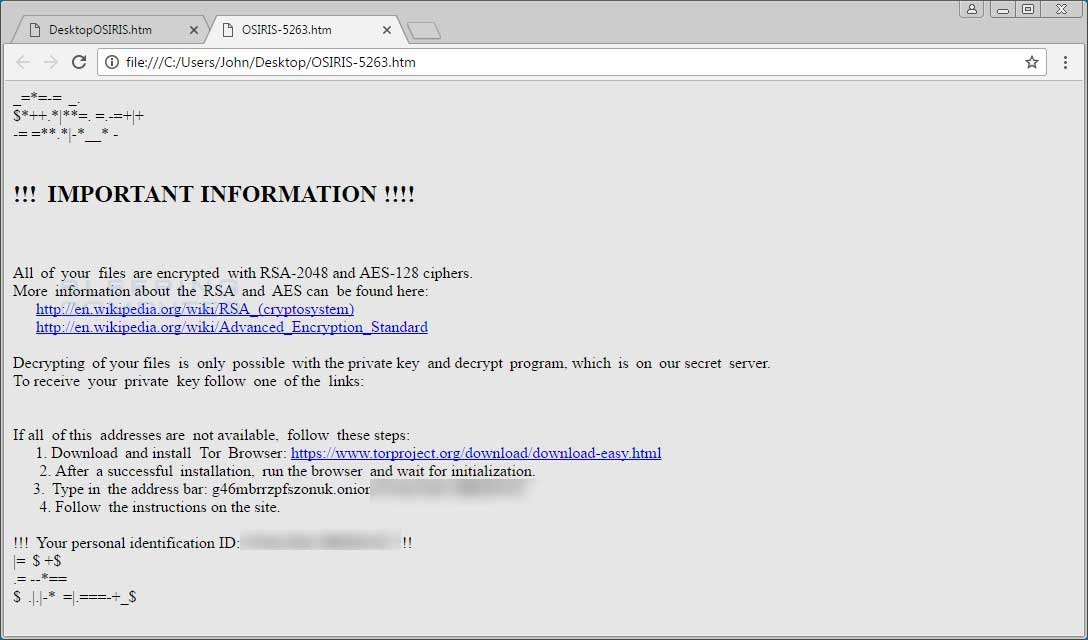
Unfortunately, at this time there is still no way to decrypt files encrypted by Locky.
Source:https://www.bleepingcomputer.com/news/security/the-locky-ransomware-is-back-and-still-adding-osiris-to-encrypted-files/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











