On Good Friday and ahead of the Easter holiday, the Shadow Brokers have dumped a new collection of files, containing what appears to be exploits and hacking tools targeting Microsoft’s Windows OS and evidence the Equation Group had gained access to servers and targeted the SWIFT banking system of several banks across the world.
The tools were dumped via the Shadow Brokers Twitter account and were accompanied by a blog post, as the group did in the past.
Called “Lost in Translation,” the blog post contains the usual indecipherable ramblings the Shadow Brokers have published in the past, and a link to a Yandex Disk file storage repo.
The password for these files is “Reeeeeeeeeeeeeee“, and they’ve already been unzipped and hosted on GitHub by security researchers.
A list of all the files contained in the dump is available here, and it reveals the presence of 23 new hacking tools named such as ODDJOB, EASYBEE, EDUCATEDSCHOLAR, ENGLISHMANSDENTIST, ESKIMOROLL, ECLIPSEDWING, EMPHASISMINE, EMERALDTHREAD, ETERNALROMANCE, ETERNALSYNERGY, EWOKFRENZY, EXPLODINGCAN, ERRATICGOPHER, ESTEEMAUDIT, DOUBLEPULSAR, MOFCONFIG, FUZZBUNCH, and others.
Last year, the Shadow Brokers claimed to have stolen these files from a cyber-espionage group known as the Equation Group, which many security firms claim is the NSA. They put up the tools up for auction, but nobody was interested in paying the hefty price of 1 million Bitcoin (around $570 million at the time).
Equation Group had backdoors inside many banks around the world
Last week, the Shadow Brokers dumped the password for the files they had put up for auction last summer. Missing from last week’s dump were the Windows files they put up for individual auctions over the winter.
This dump contains three folders named Windows, Swift, and OddJob. The Windows folder contains several Windows hacking tools, albeit these don’t look like the same tools that were put up for sale last December. The folder OddJob contains an eponymous implant that can be delivered to Windows operating systems. Details on this implant are scarce at the moment.
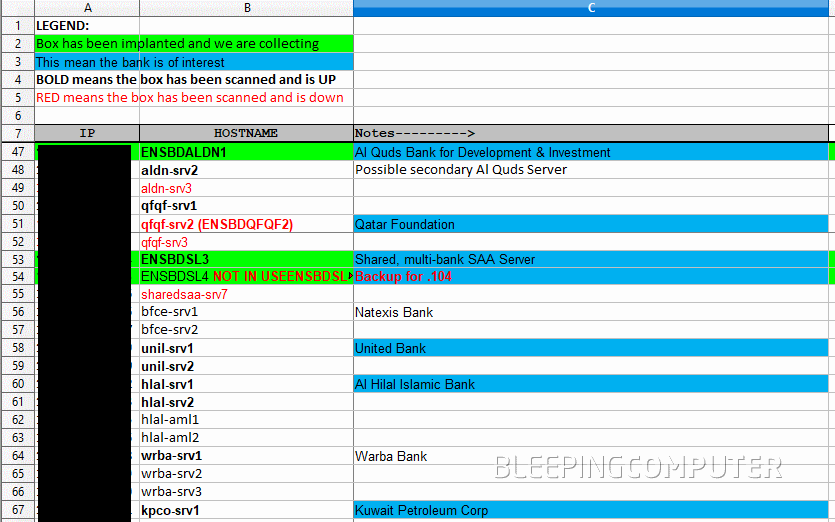
The folder claiming to hold SWIFT data contains SQL scripts that search for SWIFT-specific data, and text and Excel files that hint the Equation Group had hacked and gained access to several banks across the world, mainly in Middle Eastern countries such as Palestine, UAE, Kuwait, Qatar, and Yemen.
As the tools were dumped two hours before this article’s publication, we have very little information about their purpose, except a few tweets from security researchers that have managed to figure out the role of some of these hacking tools:
EASYPI is a Lotus Notes exploit , but which gets detected as Stuxnet
EWOKFRENZY is an exploit for Lotus Domino 6.5.4 to 7.0.2
EXPLODINGCAN is an IIS 6.0 exploit that creates a remote backdoor
ETERNALROMANCE is a SMB1 exploit over TCP port 445 which targets XP, 2003, Vista, 7, Windows 8, 2008, 2008 R2, and gives SYSTEM privileges
EDUCATEDSCHOLAR is a SMB exploit
EMERALDTHREAD is a SMB exploit for Windows XP and Server 2003
EMPHASISMINE is a remote IMAP exploit for IBM Lotus Domino
ENGLISHMANSDENTIST appears to set Outlook Exchange WebAccess rules remotely to trigger executable code on client, and then sends an email to user
ERRATICGOPHER is legacy SMB exploit targeting Windows XP and Server 2003
ETERNALSYNERGY is a SMBv3 remote code execution flaw for Windows 8 and Server 2012
ETERNALBLUE is a SMBv2 exploit
ETERNALCHAMPION is a SMBv1 exploit
ESKIMOROLL is a Kerberos exploit targeting 2000, 2003, 2008 and 2008 R2 domain controllers
ESTEEMAUDIT is an RDP exploit and backdoor for Windows Server 2003
ECLIPSEDWING is an RCE exploit for the Server service in Windows Server 2008 and later
ETRE is an exploit for IMail 8.10 to 8.22
FUZZBUNCH is an exploit framework, similar to MetaSploit
EquationGroup had scripts that could scrape Oracle databases for SWIFT data
ODDJOB is an implant for Windows
Metadata [possibly faked, possibly real] links NSA to Equation Group
NSA used TrueCrypt for storing operation notes
Some of the Windows exploits released today were undetectable on VirusTotal
Some EquationGroup humor in the oddjob instructions manual
JEEPFLEA_MARKET appears to be an operation for collecting data from several banks around the world , previously linked to the NSA by Snowden
The Equation Group targeted EastNets, a SWIFT connectivity provider

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











