An Indian developer is playing around with an open source ransomware builder, which in the long run may end up causing serious problems for innocent users.
This developer, who goes by the nickname of Empinel and claims to be based in Mumbai, has forked the open source code of the EDA2 project, and with the help of another user, has removed the backdoor hidden in EDA2’s original code.
His work started back in May 2016, when he tinkered with EDA2’s source code and renamed the project to Stolich, modifying certain aspects of EDA2’s encryption.
He received help in September 2016 when another “friendly” developer pushed a pull request to the Stolich repo that removed the EDA2 backdoor code.
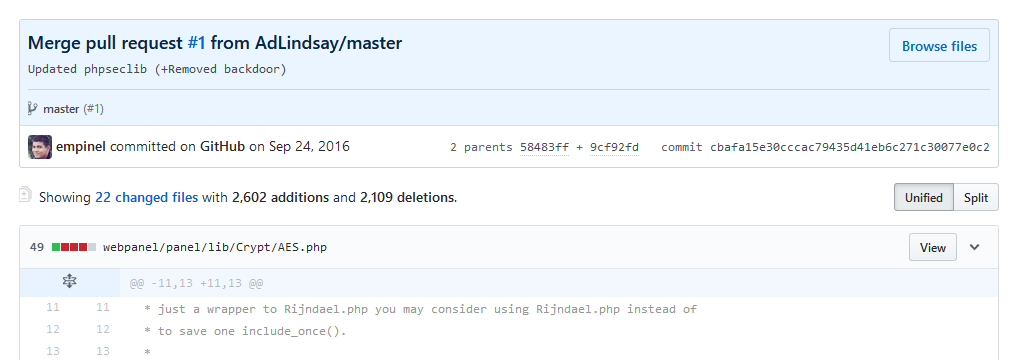
While people work on malware code on GitHub all the time, a fully-functional version of the EDA2-based Stolich ransomware popped up on VirusTotal two days ago.
Stolich used in “production”
Seeing Stolich on VirusTotal wasn’t a surprise in the beginning since many developers upload their code on VirusTotal for a quick detection test.
The surprise came when researchers realized that the version that reached VirusTotal had its code obfuscated with an evaluation version of the CryptoObfuscator code obfuscation utility, according to MalwareHunter.
No developer bothers hiding open source ransomware code — that’s also readily available on GitHub — behind a code obfuscator unless they mean to get down to business and distribute a weaponized version.
This first weaponized version of Stolich that was uploaded on VirusTotal, outside the code obfuscation, was a near carbon copy of the original Stolich version still present on GitHub. This meant the same backend code, ransom note, ransom wallpaper, and placeholder Bitcoin address (the one seized by the FBI in the SilkRoad case).

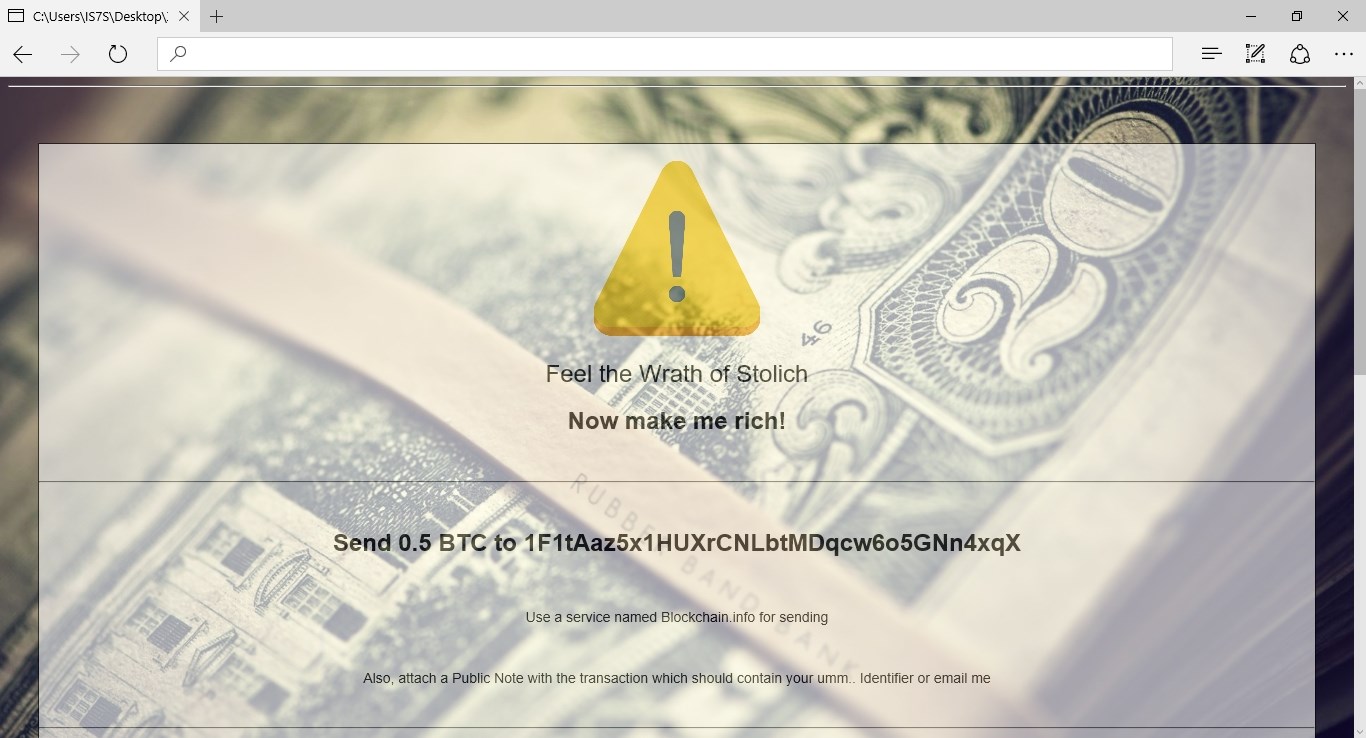
At this point, everyone hoped this was just a random test. A kid playing with ransomware he found on GitHub. Unfortunately, this was not the case.
New in-dev LMAOxUS ransomware discovered
A day later, security researcher Jack from MalwareForMe discovered an improved Stolich-based ransomware, now rebranded as LMAOxUS ransomware.
The changes in LMAOxUS were many, and included new ransom graphics for the backend portal, the ransom note, the ransom wallpaper, and a unique Bitcoin and email address for handling ransom payments.
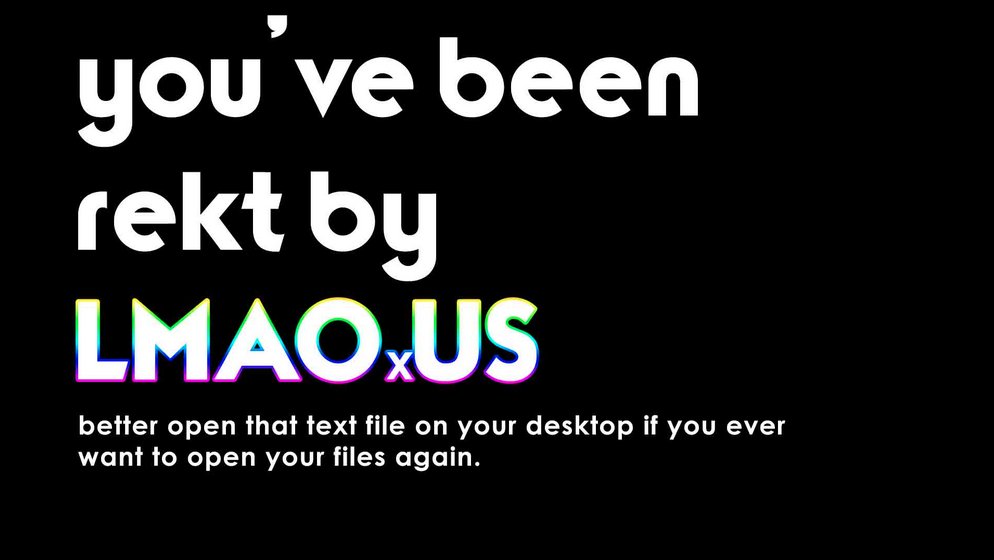
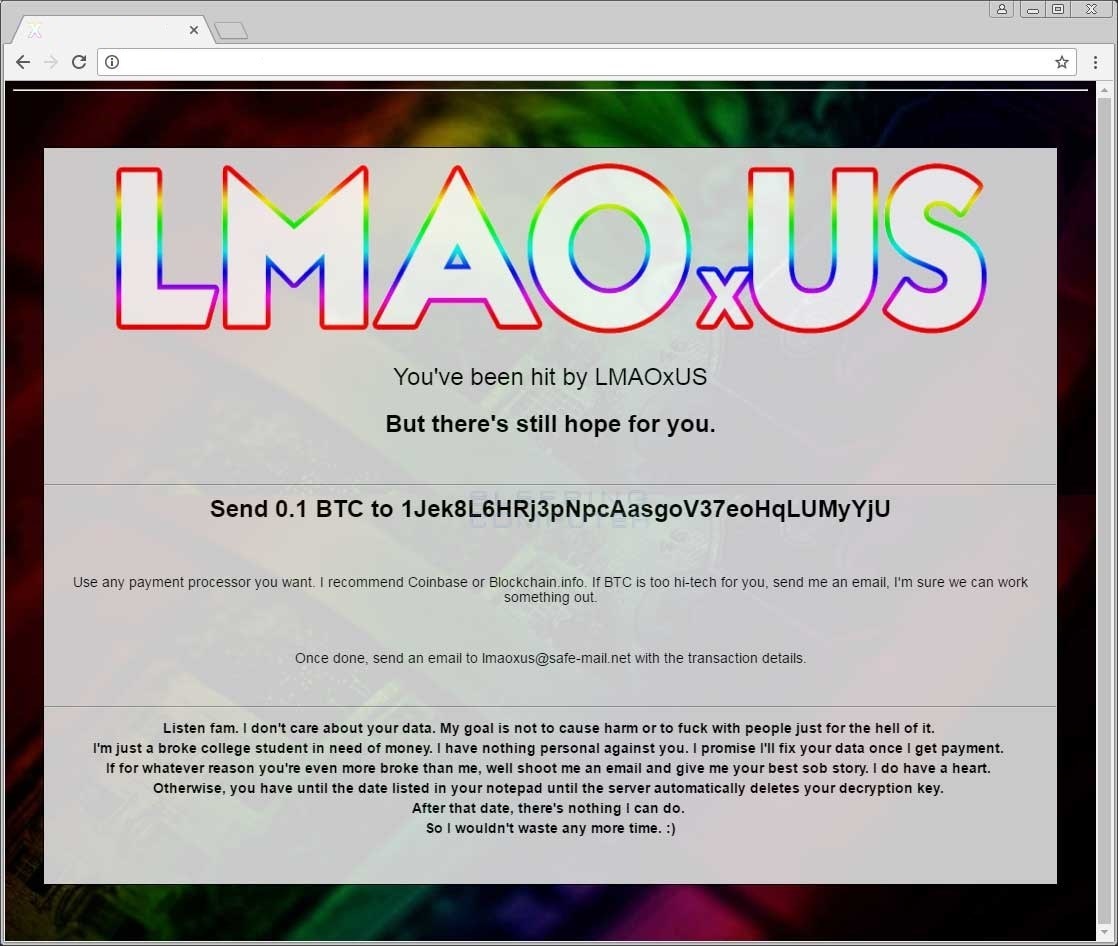
Just like Stolich, the LMAOxUS ransomware wasn’t a casual detection test. The LMAOxUS version was hidden inside a Minecraft launcher, meaning someone was testing a fully-weaponized binary in an attempt to see if VirusTotal would still detect his hidden payload (thankfully, it did, and pretty well: 38 AVs out of 62).
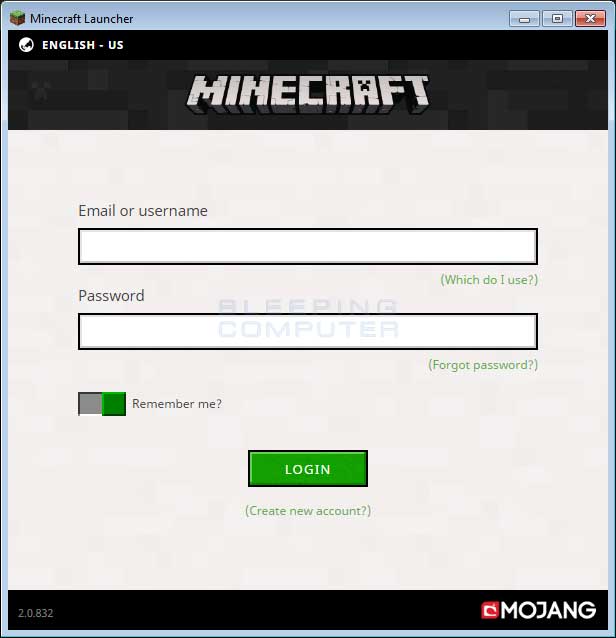
Right now, LMAOxUS looks like another in-testing ransomware created on top of the EDA2 project. Nevertheless, the person behind it has already registered a special domain to host his backend.
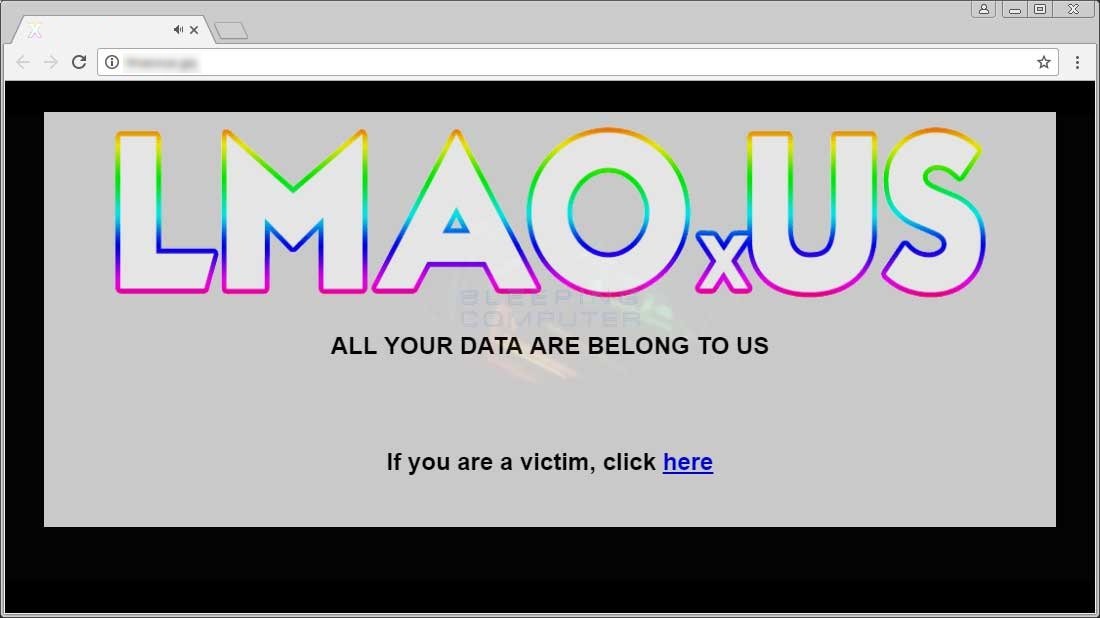
Empinel the author of LMAOxUS? Probably not!
We don’t have any evidence to sustain a claim that Empinel is behind the LMAOxUS ransomware. From the clues we found online, Empinel appears to have been more interested in showing off his coding skills.
Three days after he forked the EDA2 project and on the same day he finished tuning it up, he went on the BitcoinTalk forum to brag about his creation and ask others to review his project.

Similarly, Empinel took the time to customize the EDA2 default ransom note and add a braggadocio message at the end, addressed personally to Utku Sen, EDA2’s creator.
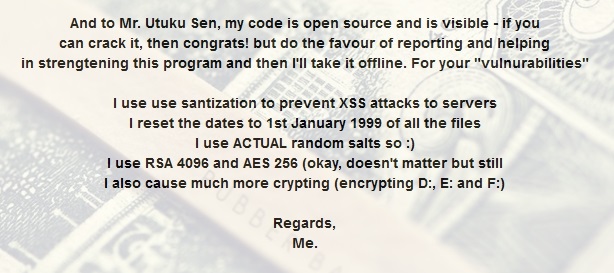
For all we can tell, Empinel didn’t even know about the EDA2 backend panel backdoor until September 2016, when another user pushed modifications to his code.
We don’t know if this second individual is the same man who’s behind the LMAOxUS ransomware, but the presence of the EDA2 backdoor has been known to the public since early 2016, which speaks to Empinel’s (lack of) knowledge of the ransomware scene.
When open source ransomware goes terribly wrong
The story of EDA2 is why open source ransomware is a terrible idea. Launched in late 2015, EDA2 is the work of Turkish developer Utku Sen, the same man who created the Hidden Tear open source ransomware building kit.
Both EDA2 and Hidden Tear were one of the first open source ransomware kits on the market, and according to this ransomware index put together by security researcher Nyxbone, have been used as the base for many of today’s ransomware threats.
Despite doing his best to hide it, crooks quickly discovered Utku Sen’s backdoors left in Hidden Tear’s encryption routine and in EDA2’s backend panel. Most of the weaponized EDA2 and Hidden Tear variants don’t feature those flaws. We only know of one case where the EDA2 backdoor was ever used.
After getting blackmailed by a ransomware developer on the Bleeping Computer forums, Utku Sen eventually removed both projects from GitHub, but by that time, they had been forked tens of times.
The impact of these tools is still relevant today via Empinel’s actions. Without having any previous expertise with ransomware development, this Indian developer was able to put together a modified and fully functional ransomware in three days, all thanks to the pre-existing EDA2 codebase.
Imagine what a more skilled actor would be capable of doing with this code, which was initially released “for educational use only.”
Whatever Utku’s intentions for EDA2 and Hidden Tear, the fact remains that he only managed to make the job of ransomware operators much easier, not tougher.
The only “education” the infosec community, and especially ransomware victims, got is that: Open source ransomware is bad, mkay!
So stop creating more of it!
IOCs
Binary for first Stolich:
d3a00a1101f2fa37b0b01bbee1b3c7f683ccf27fa224611721a863573d6e99daBinary for LMAUxUS binary:
d0d16bb28ed263038358db5c1ae784c43d6ea7993118cf390cb2e7a7466969c2Email address used in LMAOxUS ransom note:
lmfaoxus@safe-mail.netLMAOxUS extension added at the end of files:
.lmaoText-based ransom note:
LMAO_READ_ME.txtYou've been rekt by LMAOxUS. your Personal Identifier is 1111111111. Keep it handy if you want your data.
Visit .... for more info.
Your expiration date is: 4/6/2017 10:08:41 AM

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











