Following an internal audit, Google engineers say they’d discovered a new massive ad-fraud botnet that was infecting users via Android apps hosted on the official Play Store.
Named Chamois, Google says this botnet bombarded users with popup ads, boosted app statistics by installing other applications behind the user’s back, and subscribed users to premium services by sending SMS messages without their knowledge.
All of these actions helped the Chamois gang increase their profits, at the expense of Android users from all over the world.
Google discovers Chamois during internal audit
According to a blog post published today, Google engineers said they discovered Chamois while performing a routine ad traffic quality evaluation.
Engineers unearthed suspicious ad traffic, which led them to investigate further. In the end, they uncovered a massive network of apps and developers that had tricked users into installed malware-laced apps on their phones.
Initially, the malware inside the apps was hard to detect, but Google says its engineers eventually cracked the its defenses. “Chamois tried to evade detection using obfuscation and anti-analysis techniques,” engineers said.
Google now detects Chamois before apps reach the Play Store
Following Chamois’ discovery, Google says it updated its app testing system, called Bouncer, which is now capable of detecing this new threat.
“We blocked the Chamois app family using Verify Apps and also kicked out bad actors who were trying to game our ad systems,” engineers said. “This is why Google’s Verify Apps is so valuable, as it helps users discover PHAs and delete them.”
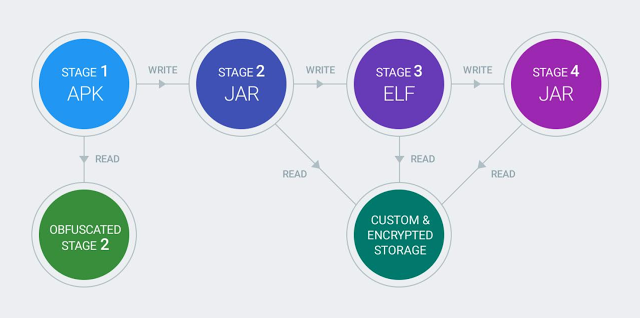
As for Chamois itself, Google says the malicious apps featured a few features not seen in previous Android malware.
The one that stood out the most was the usage of a custom encrypted file storage system. Chamois used this encrypted space to store information such as its configuration file and additional code and plugins.
Previously, only advanced, top-level desktop malware such as banking trojans used encryption to protect their configuration files. The most notable example is the Dridex family.
Chamois is one of the largest Android adware families
Overall, Google seems to be treating this new threat with a great deal of care. Acccording to the company’s engineers, Chamois is currently one of the largest PHA (Potentially Harmful Applications) families seen targeting the Android ecosystem to date.
Source:https://www.bleepingcomputer.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











