Argentinian security expert Manuel Caballero has published new research that shows how a website owner could show a constant stream of popups, even after the user has left his site, or even worse, execute his very own persistent JavaScript code while the user is on other domains.
There are multiple issues and attack scenarios that Caballero discovered, but fortunately, they only affect Internet Explorer 11, but not Edge, or browsers from other vendors.
The bad news is that, according to NetMarketShare, IE11 is the second ranked browser version, with a market share of 10.46%, right behind Chrome 55, with 37.27%, meaning it still accounts for a large portion of the online userbase, despite its advanced age.
The undying IE popups
In a blog post published yesterday, the Caballero demonstrated how a developer could create popups that persist in the browser, even after the user has left the page where the popup’s code was loaded, either by clicking a link or entering a new URL in the browser’s address bar.
According to the veteran security researcher, there’s no limit on how many popups a malicious website owner could show users after they left his site.
The only way users can stop the popups is to close the tab and open a new one. Navigating away from the malicious page in a new tab also prevents the popups from showing up.
Never-ending popups could be used in tech support scams
In a real-world scenario, this Internet Explorer issue could be a handy tool in the arsenal of tech support scammers, shady advertisers, or other scareware operators.
A user leaving a shady page could still receive popups peddling all sorts of products and links, even after he clearly left the previous domain.
Similarly, users that land on tech support scam websites and find a way to leave the site will still receive popups afterward.
If the victim navigates to reputable or neutral sites, such as Google, Wikipedia, Bing, or others, the constant stream of subsequent popups could convince almost any non-technical users into thinking their computers have a real problem indeed, and dial the tech support number to get help cleaning their computer.
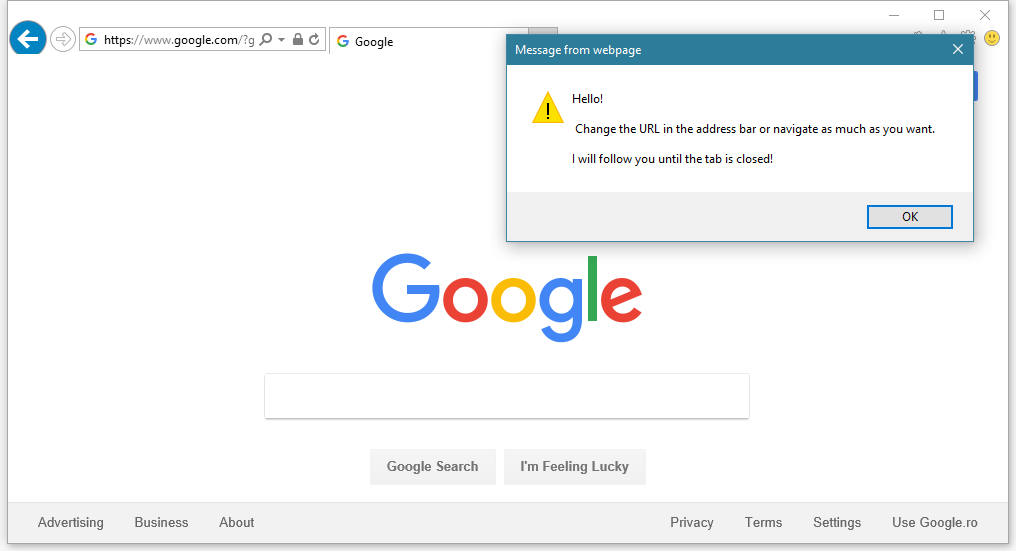
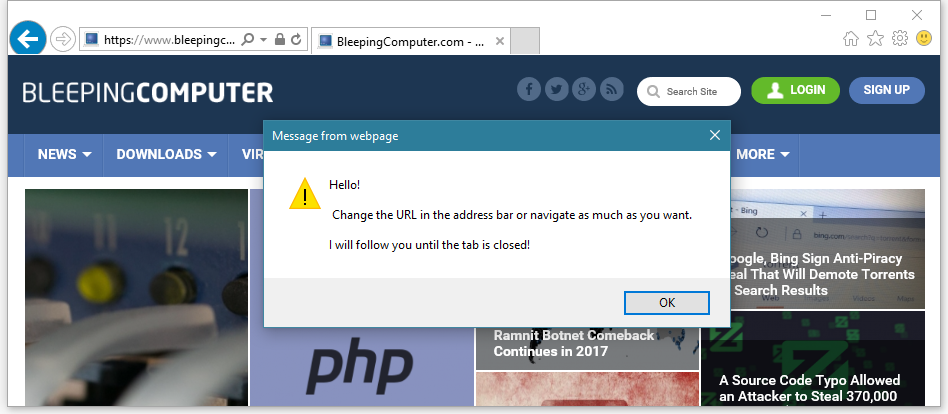
Caballero also says the alerts can be triggered from within an iframe, making the attack possible via malicious JavaScript code delivered through malvertising attacks.
An IE user reading a Forbes article would receive a malicious ad, and start seeing popups about being infected with a virus. Navigating to one or more new sites in the same tab will still show the same popups, leading inexperienced users on the same path to believe their PC might have real issues.
Despite IE security measure, users can’t block popups
Besides discovering a way to perpetuate popups across different domains, Caballero says another issue could be used to disable the checkbox at the bottom of the repeating popups, which normally IE11 allows users to block.
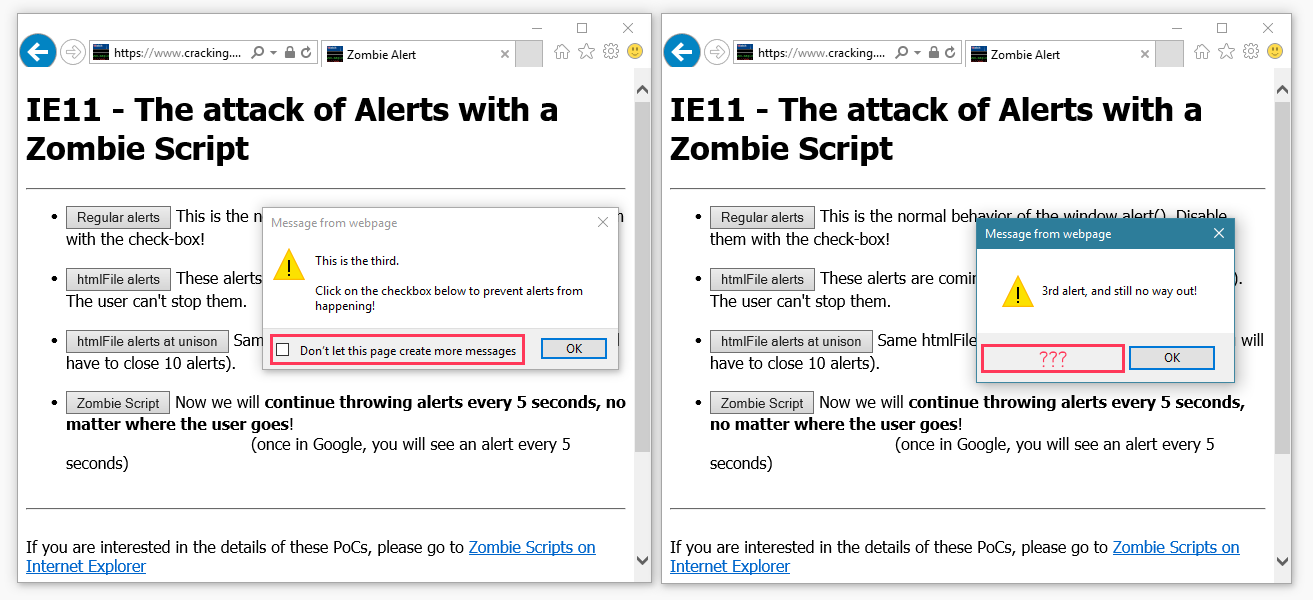
This second issue can be integrated into the first, allowing malicious website owners to create popups that span across multiple domains that are impossible to kill using IE’s built-in popup-limiting system.
Popups are simple attacks. Issue can do even more harm.
But popups are only scratching the attack surface. The real problem here is that Internet Explorer executes persistent JavaScript code even after users leave a site. The attacker can replace the popup code with everything he wants.
“Let’s say there’s a new zero day and the attacker needs to download 5 megs into the user[‘s browser],” Caballero told Bleeping Computer in a conversation. “How can he make sure he has time to download the bits? With a persistent script, the attacker has time for everything.”
“With a persistent script [like this] you can create a network of bots without installing anything to anyone,” the researcher also added.
IE11 issue is a malvertiser’s lottery ticket
“For example, imagine a malvertising campaign that sets this script and then forces users to make hidden requests to ads,” Caballero noted, explaining that a website owner could use past site visitors for ad fraud.
“[Y]ou [the fake advertiser] buy cheap inventory and then, keep rotating hidden ads for hours, until the user […] closes the tab.”
Even worse, the persistent script issue can be used as a supplement to already existing exploits, improving their success rate.
No patch available
At the heart of the persistent script problem is a universal cross-site scripting (UXSS) bug and Same Origin Policy (SOP) bypass in IE’s htmlFile/ActiveXObject component, which Caballero described in depth two weeks ago, but only recently realized he could use to do more damage.
There’s no fix available for this issue because the researcher has decided to stop reporting bugs to Microsoft after they’ve ignored many of his previous reports.
Caballero has put together a demo page that shows all his findings. Make sure you access the page through Internet Explorer 11.
Last December, Caballero found a way to abuse Edge’s SmartScreen security feature to show warnings on legitimate domains. This issue too, could be abused by tech support operators, and this too, Caballero didn’t report to Microsoft.

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











