It starts with a phishing attack over SMS, continues with a bad app and ends with your stolen bank account.
Android-targeting banking Trojan Marcher is on the rise, infecting devices via a phishing attack using SMS/MMS, gaining extensive privileges, displaying an overlay window to your banking app and collecting all your data, all the while successfully avoiding your antivirus apps.
According to experts over at Securify, it all starts with a phishing attack using SMS or MMS, with the messages including a link leading to a fake version of a popular app, such as WhatsApp, Runtastic or Netflix, to name a few. The link, however, doesn’t lead you to the good old Google Play Store, which is safe for the most part, but to a third-party app store. Of course, this doesn’t work if you don’t have the option selected from your phone’s security settings. So, as a first step to take care of your data is to not allow downloads from other app stores than the official one.
Then, if the app does get downloaded and installed, it will start requesting Android privileges that are uncommon for regular apps, including Device admin. Combined with SMS read/write and Internet permission, this app becomes dangerous, and it’s not what the regular, official app would do. Even if you don’t originally accept all those privileges, the app will nag you until you just say yes to silence it.
“Once accepted Marcher runs in the background as a service and fully controls the device as admin (permission screen attached). Obviously, a fairly significant list of permissions of which many are suspicious, especially when combined,” Han Sahin, co-founder of Securify told Softpedia.
Let the damage commence
Once the permissions have been granted, the Marcher banking malware has two goals. The first one is to compromise the out of band authentication for online banks that rely on SMS using SMS forwarding. The second is to create an overlay, showing a customized phishing window whenever a targeted app is started on the device. These overlays look pretty much identical with what you’d expect from your banking app, so it’s likely not going to raise any suspicions. This means that the people behind the attack will get your banking credentials, credit card numbers and so on, which they can use to siphon money either directly or by selling the data to others on the dark web.
So, what kind of permissions does the fake app need? Well, it can change your network connectivity state, send texts, lock the device, start malware when the device boots, view info about the status of your WiFi, edit and delete texts, call phone numbers, intercept texts, and so on. We’ve seen a few of them combined before, in genuine apps, but not all of them at once because that gives the app great control over your device.
Lots of targeted banking apps
The list of targeted banking apps is extremely long and includes, but is not limited to: BAWAG, ErsteBank, Volksbank, Bank Austria, ING DiBA Banking + Brokerage, Raiffeisen, DKB Banking, Santander MobileBanking, Barclays, Bank of Scotland, Lloyds Bank, Halifax, HSBC, Banco de Brasil, ING Direct Australia Banking, Citi Mobile, PayPal, Garanti, and more, with some banks making multiple appearances on the list due to having different apps for different locations. In total, 117 banking apps have a bullseye for Marcher.
Other targeted apps for the credit card overlay are Instagram, Play Store, Facebook, Skype, Viber, WhatsApp Messenger, Gmail and Amazon Shopping.
Bypassing the antivirus
The worst part about this is that even if you have an antivirus app on your device, it’s likely that it won’t even matter. The malware uses a simple technique by looking for any such apps on your device and if it’s running. If it does, the malware forces the phone back to the home screen. Therefore, even if the app does notice the malware infection, it can’t remove it until you give it permission. With you finding it impossible to actually see your AV interface, you can’t give the go-ahead.
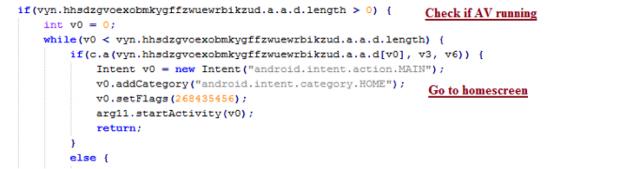
The list of antivirus apps that can be bypassed is quite long and includes well-known names such as Norton, BitDefender, Kaspersky, AVG, Avast, and Avira, as well as other well-known tools such as CCleaner, Dr.Web Light, CM Security AppLock Antivirus and more. Softpedia has reached out to BitDefender and Kaspersky for commentary, and we will update when we hear back.
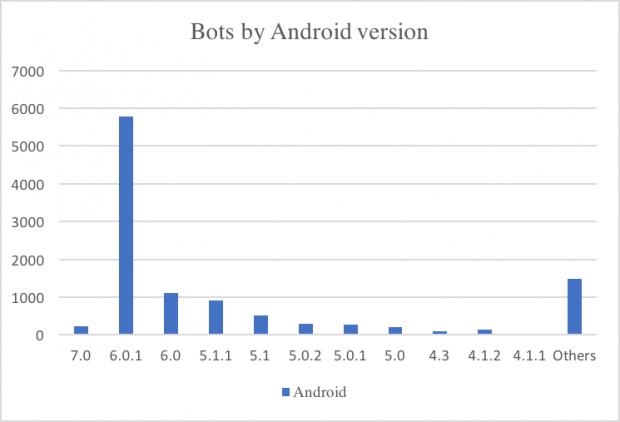
Since the app gets permission to send texts, you are quite likely to unknowingly invite your friends to download the spoofed apps as well and to help infect them too. Based on stats from Securify, nearly 5,700 German and nearly 2,200 French mobile devices have been infected, out of the total 11,000. Most of the infected devices are running Android 6.0.1.
Protect your data
So, what to do if you figure out, somehow, that your device is infected? Uninstalling the service is impossible since that has been disabled beforehand. The only way to get your device back is to perform a factory reset, as Han Sahin confirmed for Softpedia.
The best, however, is to not tap on all links you receive via text, even if they come from the friends you trust. Even if you click on that link don’t just install apps from unknown sources.
“Be vigilant when installing new applications on your device that does not match with the permissions that it needs. Obviously, a fairly significant list of permissions of which many are suspicious, especially when combined. For example, Device Admin, SMS read/write and internet permissions are not what WhatsApp or a simple Runtastic app would require. More importantly, disable “Unknown Sources” setting,” stressed Han Sahin.
Source:https://news.softpedia.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











