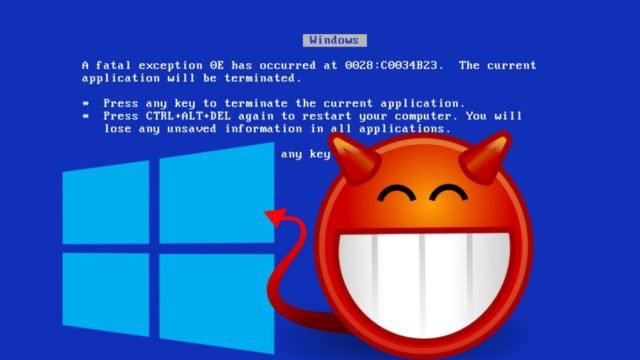
Short Bytes: A security researcher, who goes by the username lgandx, reported a severe vulnerability affecting Windows versions ranging from Windows XP to Windows 10. Due to the bug, an attacker can take control of the system over the internet and force it to the display the stop error after crashing the LSASS service. Microsoft is yet to release a patch for the bug.
Vrious versions of the Microsoft Windows operating system are prone to a memory corruption bug which can be used to crash the system remotely. In September last year, a security researcher named Laurent Gaffié informed Microsoft about the vulnerability. The attack, if possible, can compromise a Windows machine without the user knowing and initiate the stop error or the BSOD. A proof-of-concept of the attack is available on GitHub.
What is the attack?
According to Laurent’s blog post and security advisory released by the US-CERT, Windows is vulnerable towards a specifically-created server response having an excess amount of bytes in the form of SMB2 TREE_CONNECT Response structure. “By connecting to a malicious SMB server, a vulnerable Windows client system may crash (BSOD) in mrxsmb20.sys,” reads the advisory.
A target Windows system can be connected to an SMB server using various means. For instance, by hiding the link to the server in an email or a hyperlink, etc and making the user click it.
Once the user falls prey into the hands of the attacker, the Local Security Authority Service (LSASS) – where the vulnerability exists – on the Windows system can be crashed remotely, causing a denial of service attack. LSASS keeps an eye on who is logging into the system and take care of the passwords and logs for user accounts.
The affected systems include Windows XP, Windows 7, Windows 8, Windows 10, Windows Server 2003, Windows Server 2008, Server 2016, etc. As a preventive measure, US-CERT advises blocking of outbound SMB connections from users LAN to the internet.
Source:https://fossbytes.com

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.