In the past week, two security firms, Dr.Web and Emsisoft, suffered DDoS attacks at the hands of cyber-criminals who attempted to bring down their websites as payback for meddling with their illegal activities.
The first attack hit Russian security firm Dr.Web, who revealed over the weekend that a DDoS attack hit its Russian and Ukrainian domains (drweb.ru & drweb.ua).
According to the company, the attack arrived at a rate that ranged between 200,000 to 500,000 packets per second, and it lasted for over two days until its engineers managed to keep it under control and restore full service to its servers.
The DDoS attack hit the company on January 25, a day after the security firm published research which exposed a botnet that numbered thousands of infected Linux devices, which crooks were using to relay malicious traffic and hide their IPs.
DDoS attacks hit Emsisoft over the weekend
Three days later, on Saturday, January 28, Emsisoft suffered a similar fate, when a DDoS attack hit a specific section of the company’s portal, the place where Emsisoft hosts ransomware decrypters.
Speaking to Bleeping Computer, Emsisoft’s CTO Fabian Wosar said the attack clocked in at around 80 Gbps, and its defenses held up just fine, with no downtime to its website.
“They didn’t manage to take the site down,” Wosar said. “According to our provider it was a smaller attack of about 80 GBit. It was […] kinda slow.”
MRCR ransomware author behind the attack
“The last [DDoS attack] was almost definitely related to MRCR because it coincided with the malware author showing up in our forums,” Wosar also added.
MRCR is an alternative name for the Merry Christmas (or Merry X-Mas) ransomware that popped up at the start of the year, and for which Emsisoft released a decrypter.
On Saturday, the company released an update for the MRCR decrypter, targeting the ransomware’s latest version.
Moments later, the DDoS attack hit. “The attack itself started on Saturday around 10:00 AM CET, hitting the decrypter site, our email infrastructure, and our self-help portal,” said Wosar. “It went on for about 8 hours.”
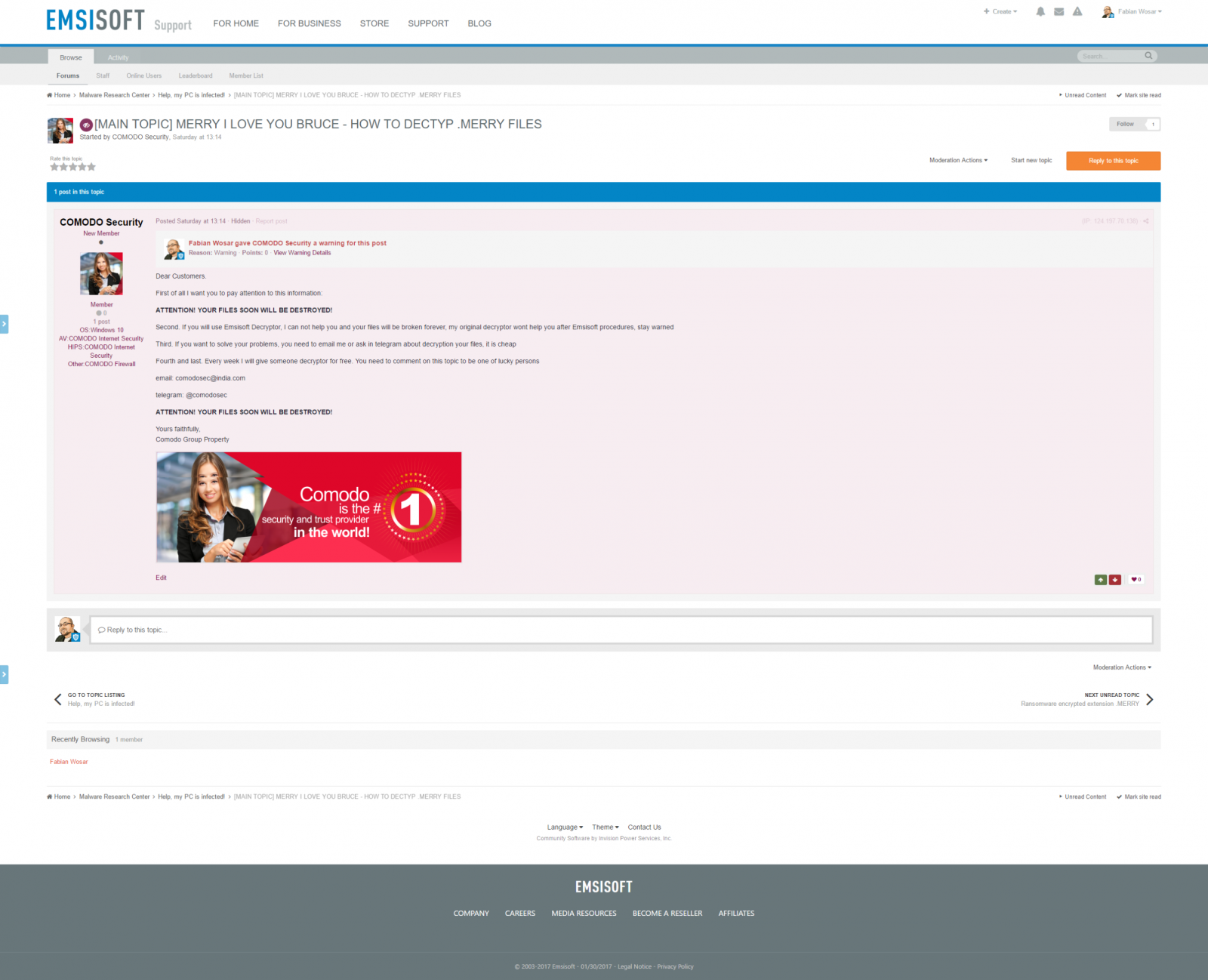
Wosar’s suspicion that the MRCR author was behind the DDoS attack was confirmed a few hours later when a person using the name COMODO Security signed up on the Emsisoft forum and made preposterous accusations that using Emsisoft decrypters will install ransomware or damage users’ computers.
In his message, this person used one of the email addresses at which the MRCR ransomware demanded users to get in contact to discuss ransom payment details.
According to Wosar, this wasn’t the first time the company’s decrypter hosting portal was hit by a DDoS attack.
“We had a bigger one just a couple of weeks ago of 640 GBps,” he said. “Multiple [attacks] actually.”
The Emsisoft researcher never discovered who was behind those attacks, but he says that at the time, he released three ransomware decrypters in a very short period at the time.
More precisely, one of the attacks hit on December 2, shortly after Emsisoft released a free decrypter for the NMoreira ransomware.
Cyber-security professionals targeted in the past
This is not the first time antivirus companies have been hit by DDoS attacks, according to Andy Shoemaker, founder and CEO of NimbusDDoS, a vendor of DDOS simulation and testing services.
Just like Dr.Web and Emsisoft, Kaspersky Lab was too, hit by DDoS attacks in the past, after exposing malware campaigns, Shoemaker told Bleeping Computer.
Another case is famous infosec journalist Brian Krebs, who was the target of several mammoth DDoS attacks in the fall of 2016, after exposing a DDoS-for-hire service called vDos.

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.