SVG has all the makings of a great malware distribution medium, and crooks are bound to migrate to this new file format, now that Google has moved to ban .js email attachments.
SVG is an image file format that’s used to store scalable vector graphics (SVG) using XML syntax.
Unknown to most is that developers can also embed JavaScript code in SVG files. While most use it to animate the image in one way or another, some clever crooks realized they could also do it to do harm.
SVG can carry JavaScript payloads
Today, JavaScript has been weaponized against users for years. Already used in malvertising and drive-by download attacks, JavaScript has become a feasible attack method even on the desktop itself.
In the past years, and last year alone, JavaScript has become one of the most used methods to infect computers with malware. Crooks usually hide JavaScript (.js) files in ZIP archives, and send the files via emails, as attachments.
Gmail and most email providers will look inside these archives unless they’re password protected. When the .js ban kicks in on February 13 for Gmail’s services, most spammers will be forced to adapt, as they won’t be able to use .js files anymore.
SVG is the prime candidate to replace .js files because it can also execute the same exact JavaScript payloads. All crooks have to do is to repackage their attachments and move their code from one file to another.
Even better, by default, on Windows, SVG files will run in Internet Explorer, which is the perfect medium for executing malicious JS.
SVGs used in malware campaigns in the past
In the past year, we’ve already seen SVG files used for malware delivery. For example, at the end of November, a spam campaign on Facebook spread SVG images to users in France.
When users opened this image, they were redirected to a YouTube website clone that asked them to install a rogue Chrome extension, which stole their browser credentials. The true damage came after, when some users reported having their PCs infected with Locky ransomware.
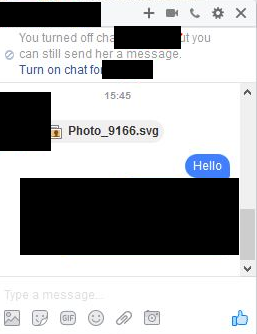
A more recent campaign was observed just this past week, spotted by @dvk01uk, Trustwave, and SANS ISC.
Researchers found emails with ZIP attachments that contained SVG files instead of JS, which when executed would load a page in IE that tried to trick users into downloading an EXE file. This EXE would install the Ursnif banking trojan.
According to researchers, this email campaign with zipped SVG attachments targeted only Japanese users.
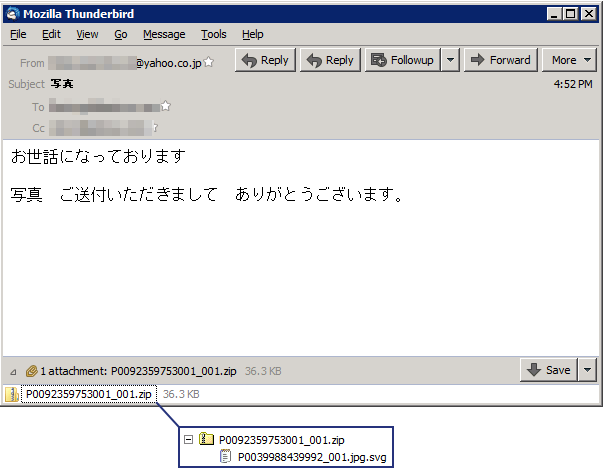
Source:https://www.bleepingcomputer.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











