Zachary Shames pleaded guilty today to charges of developing and selling malware that was later used to infect thousands of victims.
Before he was arrested this summer, the 21-year-old Shames worked as a technical intern at Northrop Grumman, a defense and security government contractor.
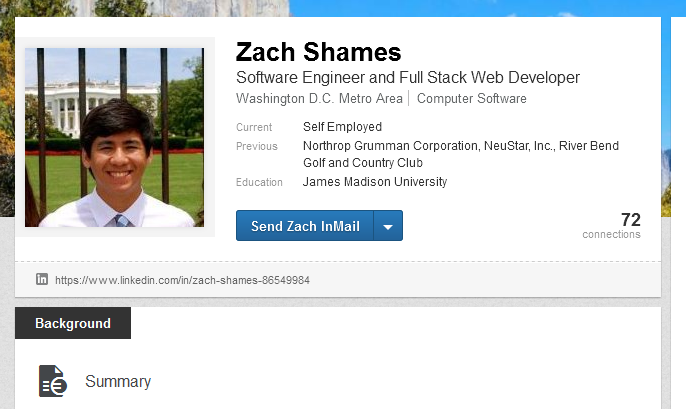
Unknown to his employer is that while in high school and college, Shames developed and sold malware on underground hacking forums.
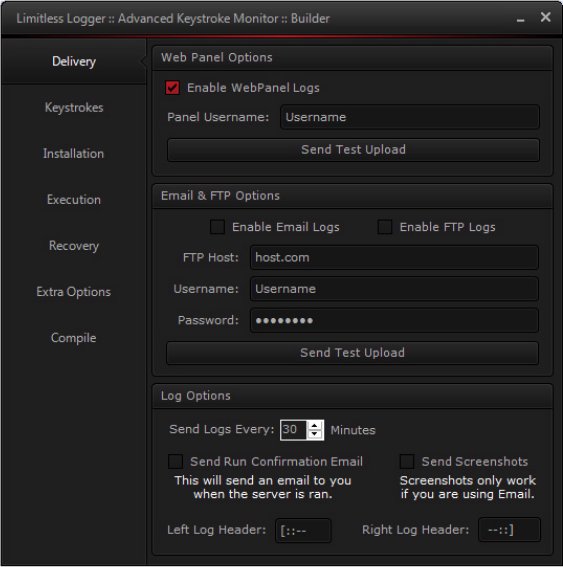
Shames is the author of a now-defunct keylogger known as Limitless Logger, sold for $35 on the infamous Hack Forums, according to Vice, quoting anonymous sources in the infosec industry.
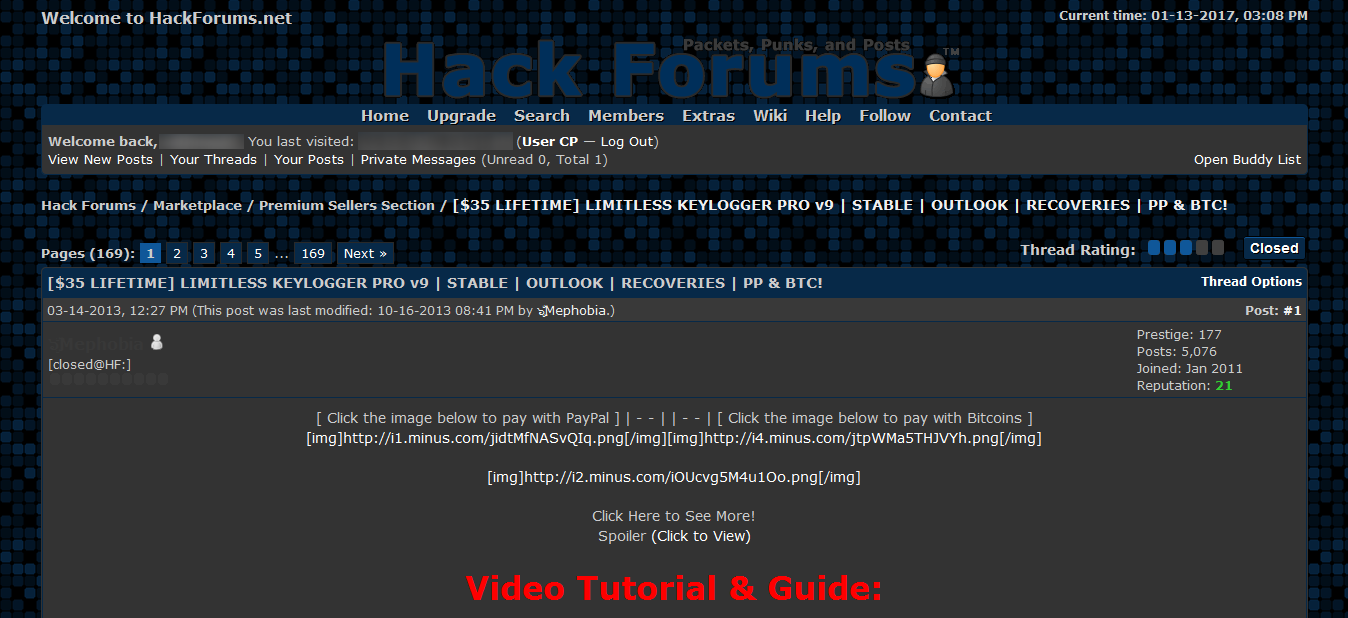
According to court documents, Shames sold his keylogger to over 3,000 customers, who then used it to infect at least 16,000 users.
Shames developed his keylogger in 2013
Shames started advertising his keylogger in March 2013. As his side-project advanced, Shames graduated Langley High School and moved on to James Madison University.
At the same time, his keylogger slowly transformed into a powerful tool, adding extra features on top of keystroke logging.
These features included a dedicated builder, the ability to upload stolen data to a FTP server, and the ability to dump data and passwords from the following applications: Chrome, Firefox, IE, Opera, Safari, Bitcoin Wallet, EpicBot, Spotify, Minecraft, Rarebot, RSBot, FileZilla, Core FTP, Smart FTP, DynDNS, Nimbuzz, Pigdin, Imvu, MSN, and Internet Download Manager.

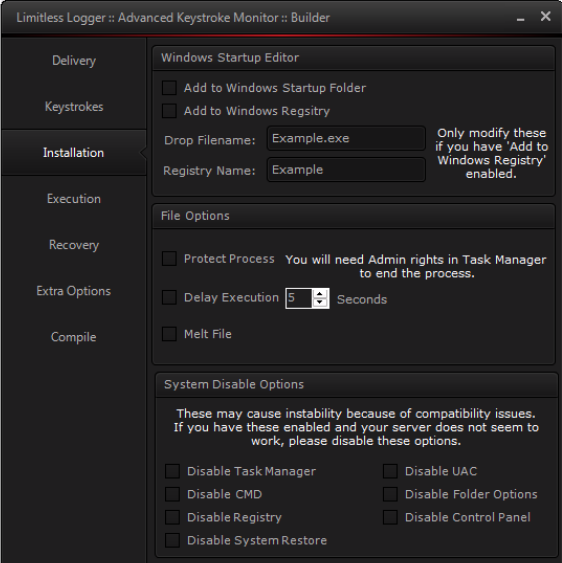
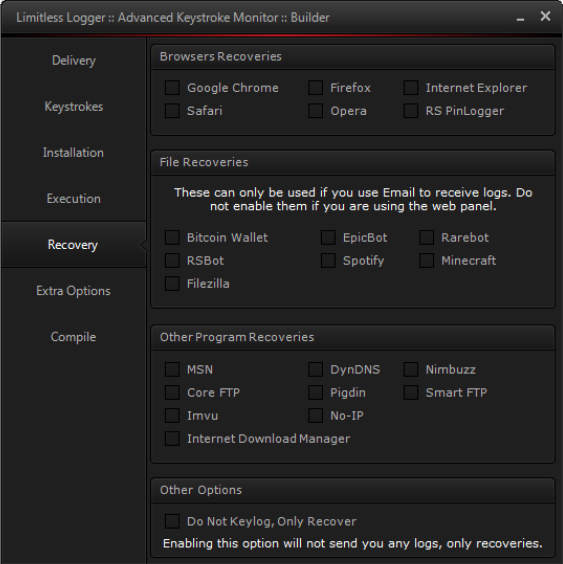
His keylogger, along with many others had been at the center of many economic espionage campaigns against Fortune 500 companies in the past few years. A Trend Micro report published in November 2014 damned Shames, turning the FBI’s gaze on his activities.
As Shames’ career as a successful software engineer took off, he later gave up developing his keylogger.
Nevertheless, authorities caught up with the former hacker, who now faces a maximum penalty of up to ten years in prison for his past deeds. Shames’s sentencing is scheduled for June 16, 2017.

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











