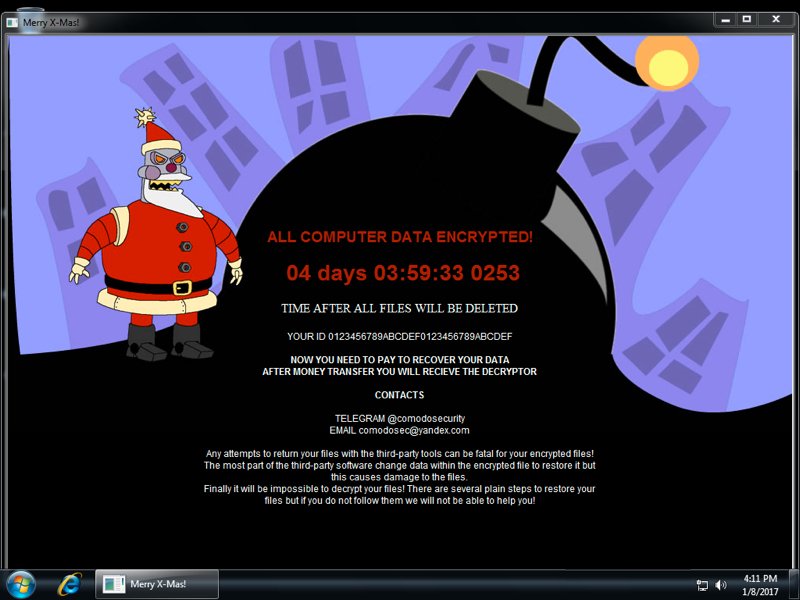
Recent variants of the “Merry Christmas” ransomware, also known as Merry X-Mas, are also dropping the DiamondFox malware on infected computers, which is used by the ransomware’s operators to collect data from infected hosts, such as passwords, sensitive files, and others.
Multiple security researchers detected the Merry Christmas ransomware in the first week of the year. Bleeping Computer ran an article detailing the modus operandi of the first ransomware variants on January 4.
The initial wave of Merry Christmas infections came from malicious documents spammed via emails posing as FTC consumer complaints.
Waves of Merry Christmas ransomware infections still being detected. Because of the ransomware’s Christmas theme, many security experts expected this ransomware to be a one-and-done affair.
To the surprise of many, a few days after the initial wave of Merry Christmas ransomware infections, security researcher Brad Duncan detected a second wave of attacks.
This time around, the ransomware used a different ransom note, and also used different spam lures. For this campaign, crooks distributed Merry Christmas using emails posing as court attendance notices.

Just like the first wave of malspam, these emails included links that downloaded a file from an online server, which contained macro scripts, and which if allowed to execute would download and install the latest version of the Merry Christmas ransomware.
Noted by Duncan, these attacks coincided with the Christmas holiday for Orthodox Christians who are following the Julian Calendar, such as large communities in former Soviet states and some Eastern European countries.
A few hours after Duncan published his findings, security researcher MalwareHunterTeam discovered that recent Merry Christmas ransomware versions would also unpack and drop the DiamondFox malware.
DiamondFox is a modular malware family that’s currently sold on various Dark Web malware marketplaces, such as AlphaBay and Hansa.
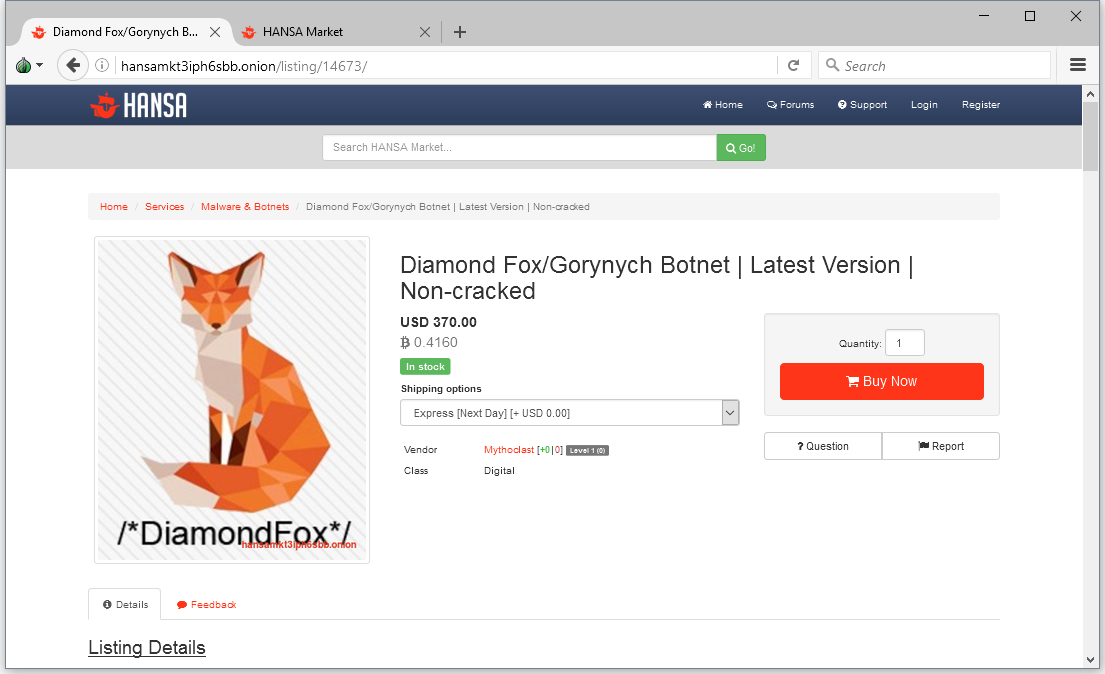
The malware is an all-around threat and includes modules that crooks can opt to deploy on a per-infection basis.
This malware includes components for transforming infected PCs into DDoS bots, components for stealing credit card data from PoS systems, components for ransacking browser passwords, components for opening RDP (remote desktop) connections, and many other more.
The Merry Christmas family is not the first ransomware threat to add secondary malware payloads to its normal attack routine. In the summer of 2016, security researchers from Kaspersky discovered versions of the Shade (Troldesh) ransomware that downloaded the Teamspy RAT in order to determine and evaluate the type of computer they infected, and decide if to charge a higher sum to unlock files.
Source:https://www.bleepingcomputer.com

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











