MongoDB administrators are about to be tought a hard lesson in database management practices, as the number of hackers that are now involved with DB hijacking attempts has gone from one to three, and more are expected to join in the upcoming days.
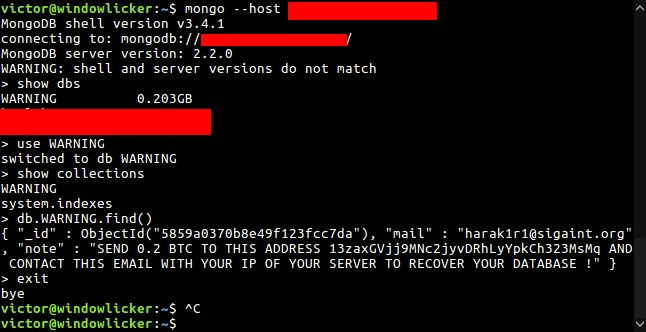
This Monday, Bleeping Computer broke the news that a hacker/group identified as Harak1r1 was taking over MongoDB databases left connected to the Internet without a password on the admin account.
The group was exporting the database’s content and replacing all tables with one named WARNING, that contained a ransom note, asking the owners of the hacked database to pay 0.2 Bitcoin (~$200) into Bitcoin wallet.
At the time of our article, Harak1r1 had hijacked just over 1,800 MongoDB databases, and 11 victims have paid the ransom in order to recover their files.
As time went by, Harak1r1 hijacked more databases, reaching at one point over 3,500 MongoDB instances, and currently peaking at over 8,500.
Among them, the hacker(s) had even managed to make a high-profile victim, in Emory Healthcare, a US-based healthcare organization.
According to the MacKeeper Security Research Team, Harak1r1 had ransacked and blocked Emory’s access to more than 200,000 medical records.
Second group joins the scene
Attacks from harak1r1 went on for two more days, but as worldwide infosec media started covering the topic, two copycats appeared and started doing the same.
The second group goes by the name of 0wn3d, and they work by replacing the hijacked database tables with a table named WARNING_ALERT.
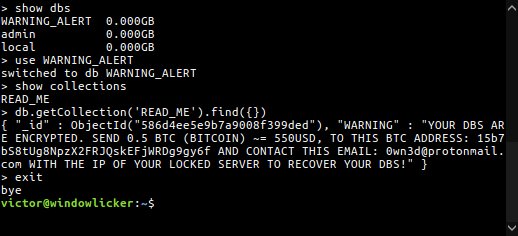
According to Victor Gevers, the researcher who initially discovered the first hacked MongoDBs around Christmas, this second group has hijacked just over 930 databases.
Unlike Harak1r1, this second group is a little bit more greedy and asks for 0.5 Bitcoin, which is around $500, but this hasn’t stopped companies from paying, with 0wn3d’s Bitcoin wallet showing that at least three victims had paid his ransom demands.
Third group discovered
A day later, the same Gevers came across a third actor, using the name 0704341626asdf, which appears to have hit over 740 MongoDB servers.
This hacker/group is asking for 0.15 Bitcoin (~$150), and he’s using a lengthier ransom note, in which he admonishes victims for leaving their DB open over the Internet.
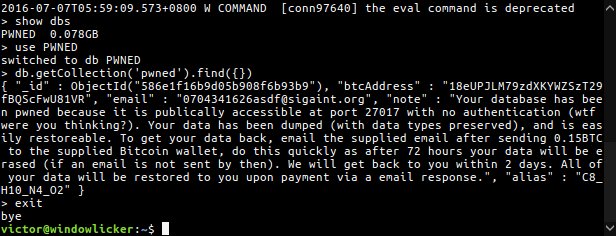
Furthermore, this threat actor appears to be more strict with victims and gives database owners 72 hours to pay the ransom.
Paying the ransom won’t mean victims get their data back
According to Gerves, the lines that allowed him to track the activity of these three groups is slowly blurring, as these groups started using more varied messages and different Bitcoin addresses.
Additionally, in newer variations of these attacks, the hackers don’t appear to bother copying the hacked database. In recent attacks, Gevers says that crooks just delete the DB’s content, ask for a ransom regardless, and hope nobody checks the logs and discovers what they’ve done.
Turf war over MongoDBs has begun
But the bad news doesn’t end here. According to Gevers, these groups are now fighting over the same turf, with many of them rewriting each other’s ransom notes.
This leads to cases where database owners pay the ransom to the wrong group, who can’t give their content back.
“It’s catching on and it looks more players are coming to the game. Which is a bad thing,” Gevers told Bleeping Computer today.
“Although this might be the little push the MongoDB owners needed to start fixing their open MongoDB databases,” the researcher added, referring to the large number of unprotected MongoDB servers connected online.
“The total of MongoDBs on Shodan is still growing, and ZoomEye shows over 90,000 open servers. The AWS security team is being flooded with help requests,” Gevers added, who himself has been busy providing aid to companies that have been hit by these attacks.
IOCs
The table below presents a summary of all details related to the MongoDB ransom attacks. The table is most likely incomplete. Feel free to reach out with any new details you have.
| Group name | Email Address | Bitcoin Address | Ransom size | Name of replaced DB | Known IPs |
|---|---|---|---|---|---|
| Harak1r1 | harak1r1@sigaint.org | 13zaxGVjj9MNc2jyvDRhLyYpkCh323MsMq 1MMA6YD99vAfzKqhrb3dY91KpSZV6TMd2x 14VaE8NpTBTvx8k4SmteYKwPiu2YeWmuhh |
0.2 BTC | WARNING | 92.99.14.33 |
| 0wn3d | 0wn3d@protonmail.com | 15b7bS8tUg8NpzX2FRJQskEFjWRDg9gy6f | 0.5 BTC | WARNING_ALERT | 185.106.120.159 |
| 0704341626asdf | 0704341626asdf@signaint.org | 18eUPJLM79zdXKYWZSzT29fBQScFwU81VR | 0.15 BTC | PWNED | 95.211.184.210 |
Ransom notes used by each group:
SEND 0.2 BTC TO THIS ADDRESS 13zaxGVjj9MNc2jyvDRhLyYpkCh323MsMq AND CONTACT THIS EMAIL WITH YOUR IP OF YOUR SERVER TO RECOVER YOUR DATABASE !
YOUR DBS ARE ENCRYPTED. SEND 0.5 BTC (BITCOIN) ~= 550USD, TO THIS BTC ADDRESS: 15b7bS8tUg8NpzX2FRJQskEFjWRDg9gy6f AND CONTACT THIS EMAIL: 0wn3d@protonmail.com WITH THE IP OF YOUR LOCKED SERVER TO RECOVER YOUR DBS!
Your database has been pwned because it is publicly accessible at port 27017 with no authentication (wtf were you thinking?). Your data has been dumped (with data types preserved), and is easily restorable. To get your data back, email the supplied email after sending 0.15BTC to the supplied Bitcoin wallet, do this quickly as after 72 hours your data will be erased (if an email is not sent by then). We will get back to you within 2 days. All of your data will be restored to you upon payment via a email response.Source:https://www.bleepingcomputer.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











