Malware distributed via affiliate programs and bundled with other applications is using a devious tactic to fool users into installing it on their systems.
Detected this month by malware analysts from Dr.Web, the malware’s name is Ticno (Trojan.Ticno.1537), and despite its shady tactics, this threat comes with top-shelf anti-detection features.
Ticno isn’t your regular malware downloader that blindly listens to instructions and installs its payload on every system.
This malware comes packed with features that scan the potential host’s system in order to determine if the computer is a real PC, or a virtual machine used by security researchers to scan and analyze the malware.
According to Dr.Web, the malware scans for the following processes:
IrisSvc.exe
wireshark.exe
ZxSniffer.exe
Regshot.exe
ollydbg.exe
PEBrowseDbg.exe
Syser.exe
VBoxService.exe
VBoxTray.exe
SandboxieRpcSs.exe
SandboxieDcomLaunch.exe
windbg.exe
ollydbg.exe
vmtools.exe
Additionally, it scans computers for the following registry keys:
HKCU\Software\CommView
HKLM\SYSTEM\CurrentControlSet\Services\IRIS5
HKCU\Software\eEye Digital Security
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Wireshark
hklm\SOFTWARE\ZxSniffer
HKCU\Software\Win Sniffer
HKCU\Software\Microsoft\Windows\CurrentVersion\Explorer\MenuOrder\Start Menu2\Programs\APIS32
HKCU\Software\Syser Soft
hklm\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Oracle VM VirtualBox Guest Additions
HKLM\SYSTEM\CurrentControlSet\Services\VBoxGuest
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Sandboxie
HKCU\Software\Classes\Folder\shell\sandbox
HKCU\Software\Classes\*\shell\sandboxIf more than three of these checks are successful, Ticno stops its execution and starts the Windows Explorer process as a decoy.
However, if these checks pass, Ticno shows a “Save As” dialog window, asking the user to save a file on his computer named 1.zip.
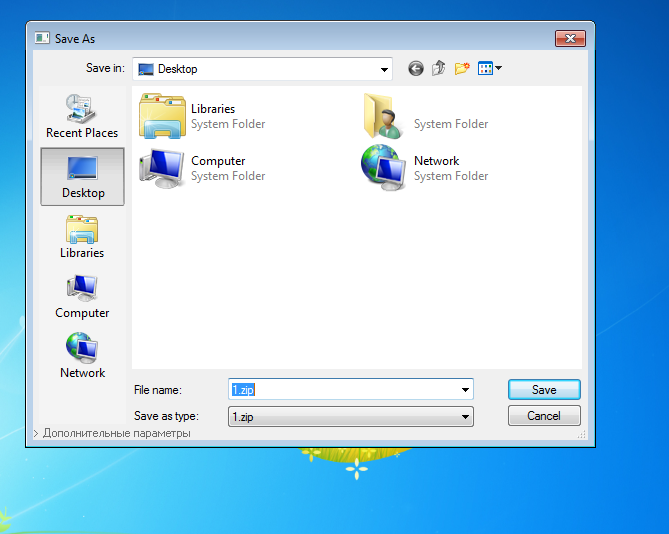
An experienced user will find it very disturbing that he’s asked to save a ZIP file to disk out of the blue, or during the installation of another program.
Unfortunately, malware was never meant to infect smart tech-savvy users, and there will be people that click on the Save button.
But there’s a hint that gives away this fake “Save As” popup, and that’s a link in the bottom-left corner of the window that reads “Additional settings.”
The presence of this link, especially on a “Save As” dialog window is very conspicuous. Clicking the link reveals the true nature of this windows.
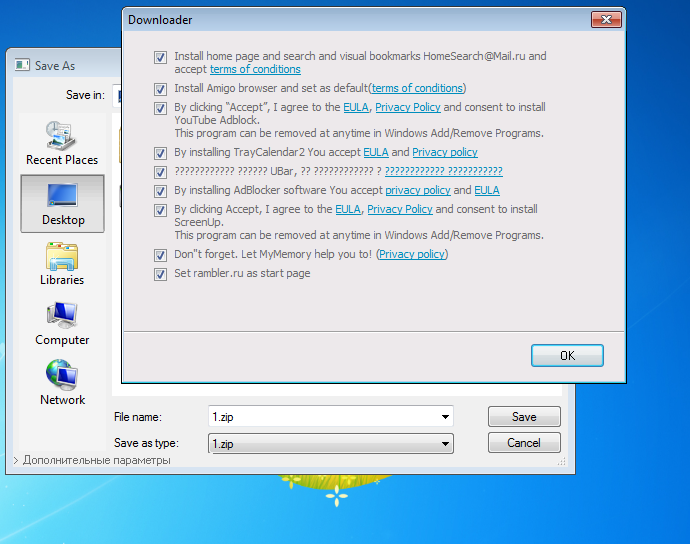
This brings up another popup, a classic page included with all bundled installers, which allows users to select which of the bundled programs they want to install.
Ticno used to push adware and Chrome extensions
According to Dr.Web, this window includes installation options for all sorts of adware, packaged as Windows software or Chrome extensions.
The list includes Trojan.ChromePatch.1, Trojan.Ticno.1548, Trojan.BPlug.1590, Trojan.Triosir.718, Trojan.Clickmein.1, and Adware.Plugin.1400.
Legitimate apps, such as the Amigo browser and the HomeSearch@Mail.ru developed by Mail.ru are also included, most likely part of affiliate software installation schemes that net the Ticno authors a nice profit.
If users fail to spot this link and press the Save button, the “Save As” dialog box shows its true face and transforms into an installer.
Source:https://www.bleepingcomputer.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.










