Spammers are mass-messaging Facebook users with PDF files claiming to contain nude celebrity pictures, but which lead users to a malicious Chrome extension and overly aggressive advertising sites.
This spam campaign was detected by Cyren researchers Magni Reynir Sigurðsson & Maharlito Aquino, who shared their findings with Bleeping Computer readers in advance, albeit their research will be made available on the Cyren blog with more details about the attacks. [Update: Cyren blog post is now live.]
Sexualized PDF files spread on Facebook
According to the Cyren crew, the spam campaign spreads via private messages and posts in various Facebook groups.
The infected user uploads a double-extension file in the form of [celebrity_name]-[sexualized_lure].mp4.pdf.
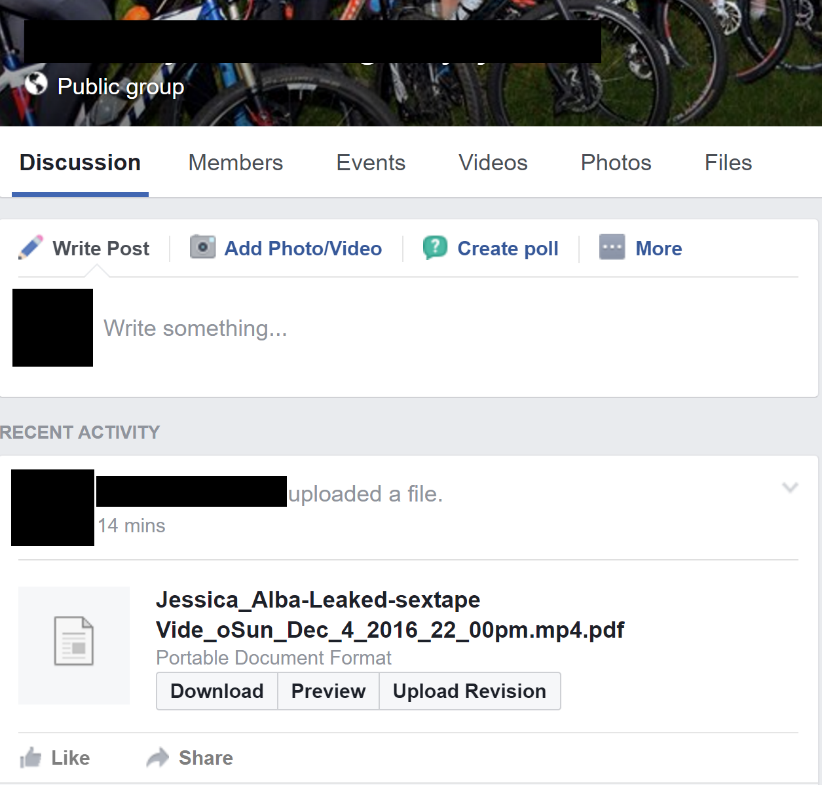
Users who open the PDF file are greeted with a giant image that contains a play button in the middle, alluding that the PDF may contain a video.

In reality, users that click the link are redirected to an online page. This page filters incoming victims based on their browser.
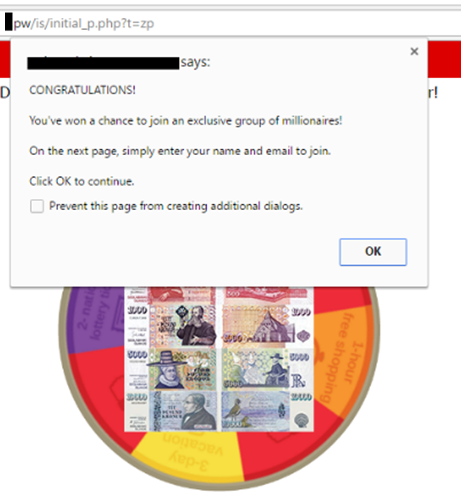
Users accessing the link via desktop browsers such as Internet Explorer, Firefox, or Safari, are shown a page with overly-aggressive popups and advertisements.
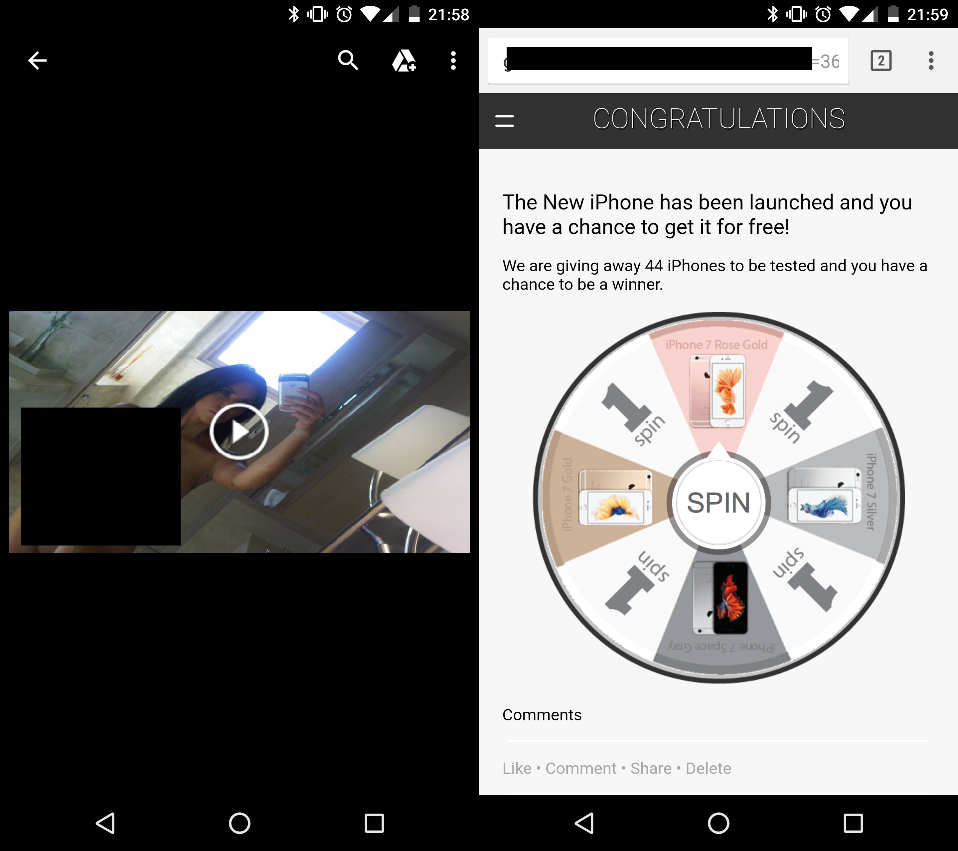
Mobile users, regardless of browser, land on the same page with aggressive ads.
On the other hand, Chrome desktop users are in for a treat, as they’re redirected to a fake YouTube page, which asks them to install a Chrome extension to view the videos.
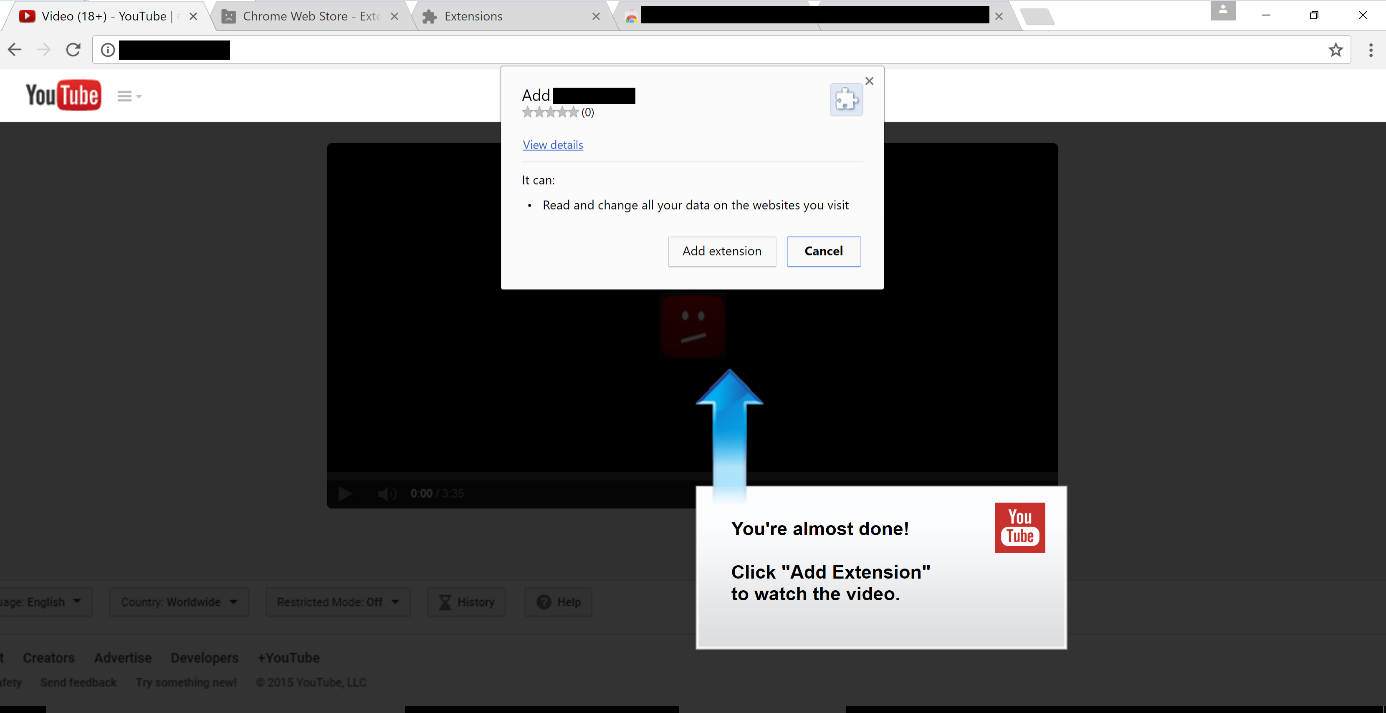
Cyren researchers said that the crooks behind this spam campaign managed to squeeze their extension by Google’s security team and uploaded it to the Chrome Web Store. The extension has been removed, at the time of writing, the Cyren team said.
Chrome extension infects other users and spreads the spam further
The role of this malicious extension is to prompt users to re-authenticate on Facebook. This allows the attacker(s) to collect the user’s credentials and use the victim’s account to spread the malicious spam to other users.
The Cyren team has also taken a look at the Chrome extension’s source code, in order to better understand how this spam campaign worked.
Sigurðsson & Aquino discovered that the Chrome extension comes with support for intercepting web traffic in real-time, in order to determine what the user can access through his browser.
For example, the malicious Chrome extension comes with a long list of security-related domains that it blocks and prevents the user from loading.

Furthermore, the Chrome extension also prevents the user from accessing the Chrome Extensions settings page (chrome://extensions), so the victim can’t disable the rogue add-on.
Similarly, the extension also prevents the user from accessing herokuapp.com links and blocks the user from opening Chrome’s built-in Developer Tools.
Functionality is also included for downloading and running other malicious scripts.
Inside the extension’s source code, the two Cyren researchers also discovered the malicious code responsible for generating the spam.
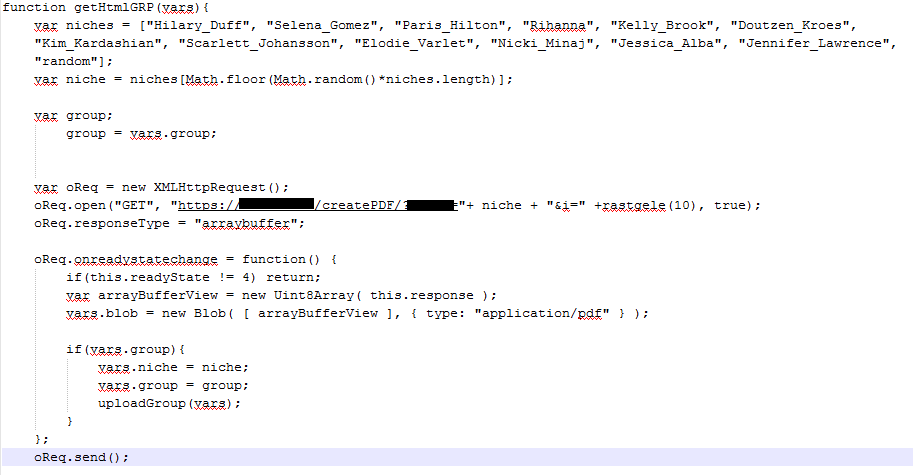
According to the code pictured above, the malicious PDF files uploaded on Facebook contain the name of celebrities such as Hillary Duff, Selena Gomez, Paris Hilton, Rihanna, Kelly Brook, Doutzen Kroes, Kim Kardashian, Scarlett Johansson, Elodie Varlet, Nicki Minaj, Jessica Alba, and Jennifer Lawrence.
Chrome extension removal instructions
In order to remove this malicious Chrome extension, users have to do two things. The first step is to remove a Windows Registry key the extension adds during installation.
Users must open the Windows Registry Editor by pressing the Start button and typing “regedit” in the Search/Run option. In the new window, use the side menu to find the folder below, right-click it and select “Remove.”
HKEY_LOCAL_MACHINE\Software\Google\Chrome\ExtensionFor the second step, the extension must be removed from the browser. Because the Chrome extension prevents access to the native Chrome Extensions settings page, users must remove it by deleting the following folder from their computer.
C:\Users\USER\AppData\Local\Google\Chrome\User Data\Default\ExtensionsDeleting this folder removes all your Chrome extensions. Normally this folder would contain a list of randomly-named directories, with each random name representing the ID of a Chrome extension.
Because users can’t access the Chrome Extensions settings page to get the malicious extension’s ID, it’s better if they delete all the folders and cleanse their browser of this threat.

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











