A group of malware authors has come up with a new method of transcending an infection from the user’s computer to his Android smartphone.
Discovered by security researchers from BadCyberLabs, the initial infection is with the ISFB (also known as Gozi2) banking trojan, while the second-stage infection was via the Marcher Android banking trojan.
ISFB trojan first, then Marcher
Researchers say that users first get infected with the ISFB trojan after they open a file attachment they received via spam email. The spam campaign poses as emails from the Polish Ministry of Finance and spreads a file with a double-extension such as .PDF.EXE.
Opening this phony executable installs the ISFB trojan on the victim’s computer, which is your regular run-of-the-mill banking trojan that relies on a technique called “web injects” to insert extra content inside live websites.
Most of the websites targeted by the ISFB trojan are banking portals, with your occasional social network, in case the malware operators wanted to collect some of the user’s login credentials.
Malware uses phony Gmail popup
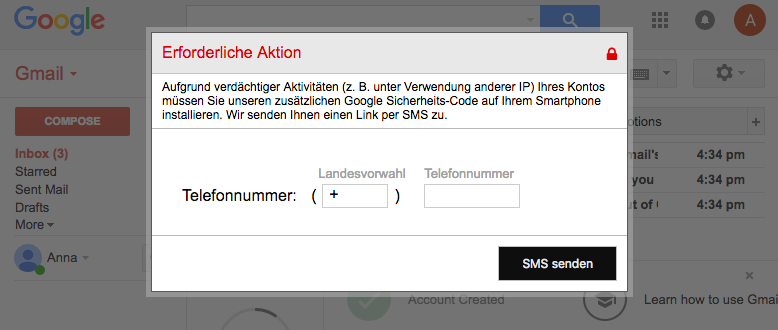
But in a recent variant of this threat, BadCyberLabs researchers said they observed the ISFB trojan showing web injects inside the Gmail window after the user has logged in.
The web inject is a simple popup that asks the user for its phone number, in order to send it a version of the Google Authenticator Code app, so the user would secure his Gmail account.
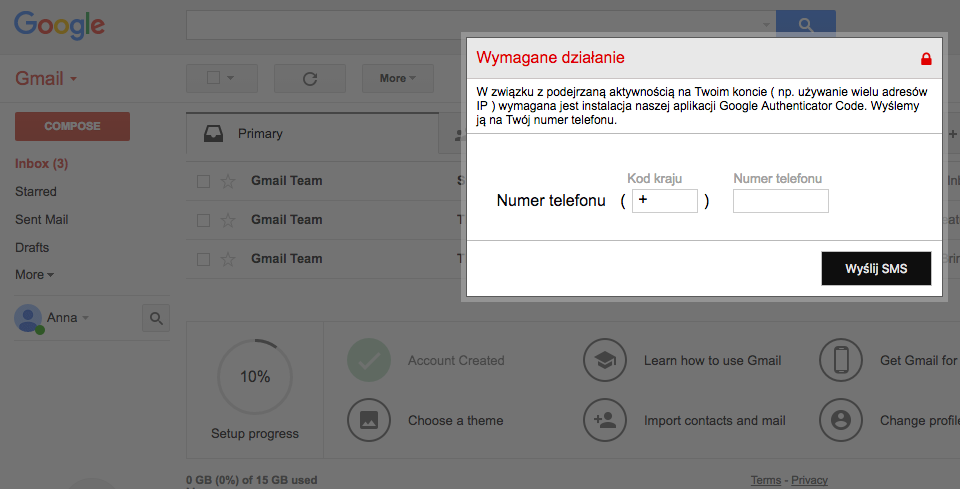
If the user falls for this popup, and there’s a high chance most will, he receives an SMS message on his phone, with a Goo.gl short link that points to an Android app package (APK file) hosted outside the Google Play Store.
Before it was taken down, over 100 users had received and clicked on the link, according to Google statistics, albeit it’s not sure that all would have installed the app. Android, by default, comes with settings that prevent the installation of apps from third-party locations, outside the Play Store.
In case the user wouldn’t mind disabling all those security settings to install the malicious APK, they’d be infected with the Marcher malware, one of the most advanced banking trojans known today.
Trojan targets Polish and German users
At this point, the ISFB trojan on the user’s desktop would detect a successful smartphone infection, and continue its social engineering game by asking the victim to input a 6-digit code they’d received via the app. This step is most likely carried out to reassure victims they installed a valid app, and not malware.
“It looks like the security mechanisms implement by banks, in particular webinject detection, became such an obstacle to criminals that they had to invent new ways of forcing users to install mobile malware,” researchers said.
“While the malicious mobile app does not steal banking credentials (as those are being stolen by it’s desktop companion),” researchers note, “it uses the opportunity to steal credit card data via app overlays in Google Play, Gmail or Paypal apps.”
BadCyberLabs researchers say the Marcher-infected app is preconfigured to avoid infecting users from former Soviet states, except for Georgia and the three Baltic countries.
At the moment, the ISFB+Marcher campaign appears to be targeting only Polish and German users.

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











