When it comes to ransomware, we are seeing the oddest variants being released. This is no exception with a batch file ransomware discovered by Avast malware analyst Jakub Kroustek that runs within the Windows command prompt.
Jakub had found two in development variants, with the first one being called PayDOS and the second one being called Seprent. Though both ransomware infections do demand a ransom payment, neither of them actually encrypt your files, but rather rename them instead.
The PayDOS Command Prompt Ransomware
The first variant discovered by Jakub is called PayDOS and is a batch file converted into a executable. When run, the executable will extract the batch file into the %Temp% folder and run it from there. Once executed, batch file will scan certain folders for certain file extensions and rename the file so that one letter of the extension is changed. For example, test.png may become test.dng. It does not actually encrypt the files.
The program will then display the ransom screen where it asks for a passcode to “decrypt” the files. Once a victim enters the hard coded passcode of AES1014DW256, the batch file will rename all the files back to their original extension so that they can be opened again.
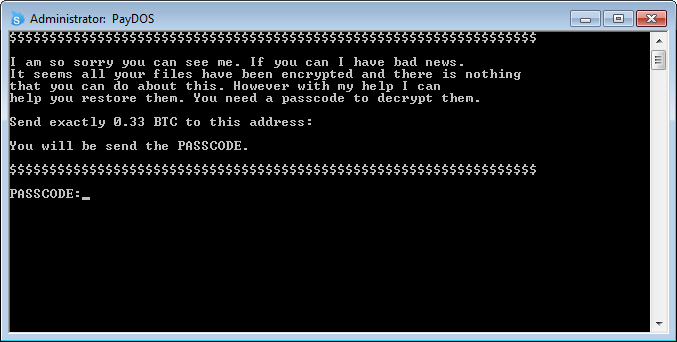
Below is a screen shot showing how a folder of PNG files would be renamed.
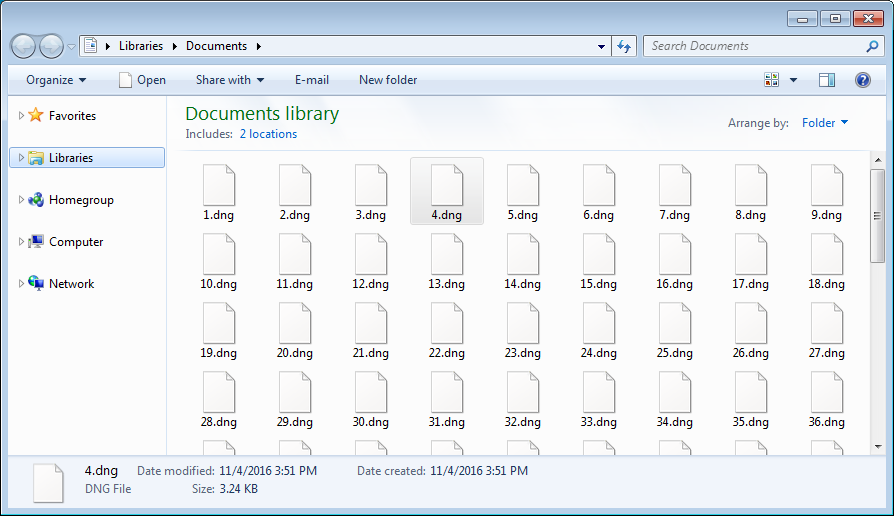
If a victim did not know the passcode, they could simply rename the files back to .png and the files would open as normal.
Serpent Ransomware: The next step in PayDOS Development
A newer version of PayDOS was renamed as Serpent and now included a fake email to contact called serpent.ransom@notrealemail.com. Like the previous variant, though, this still appears to be in development as though it does provide an email, this email address is fake. Furthermore, like like PayDOS it continues to just rename the files rather than encrypting them and uses a hardcoded password of RSA1014DJW2048.
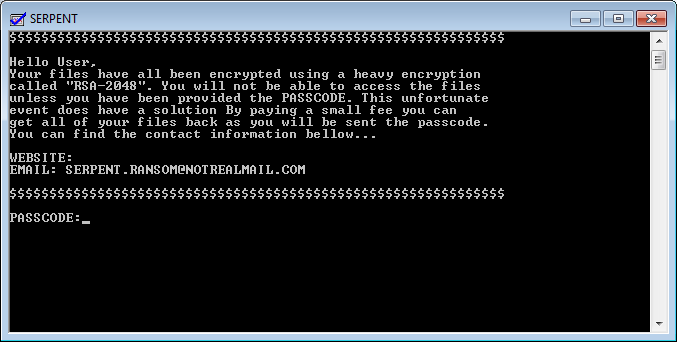
One other feature added to this variant is the inclusion of a VBS file that will speak a warning to the victim similar to Cerber. When the batch file is executed, it will create the file called C:\USERS\[username]\APPDATA\LOCAL\WINDOWS\WindowsUpdate.VBS and include the VBS code to make the computer speak to you and then launch it.
Will PayDOS ever be actively distributed?
Every week myself and other researchers see many new ransomware variants released. In many cases , these variants are in-development and uploaded to sites like VirusTotal by the developers to see what security vendors will detect their programs. For the most part, the in-development ransomware variants we see are never fully completed or distributed.
My guess is that this ransomware will not be distributed because the functionality required to create a true fully-functional encrypting ransomware is just not available from batch files. A developer could also include PowerShell or other routines to perform the encryption and network communication, but it makes the program that much more complicated and not something most new developers can do.
Source:https://www.bleepingcomputer.com

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.










