If you ask any malware analyst these days, they’ll tell you they come across countless of useless or unfinished malware variants on a daily basis.
One of the latest, and probably the weirdest was uncovered yesterday by GData malware analyst Karsten Hahn, who came across a fake cleaner app called CainXPiiCleaner, which exhibited some odd features.
When ran, the malware will connect to a URL hardcoded in the program and download the contents of the web page. The URL currently used by the malware is “http//ni565894_1.vweb16.nitrado[.]net/site.html”, but it has been suspended by the ISP. When the site was live, it would contain a list of commands that the malware would download and execute one-by-one.
Based on an analysis of its source code and by using the Fiddler autoresponder feature to make it seem like the site will still operational and providing commands, Lawrence Abrams of BleepingComputer.com was able to test each command and their functionality.
A breakdown of these instructions and their odd actions is listed below.
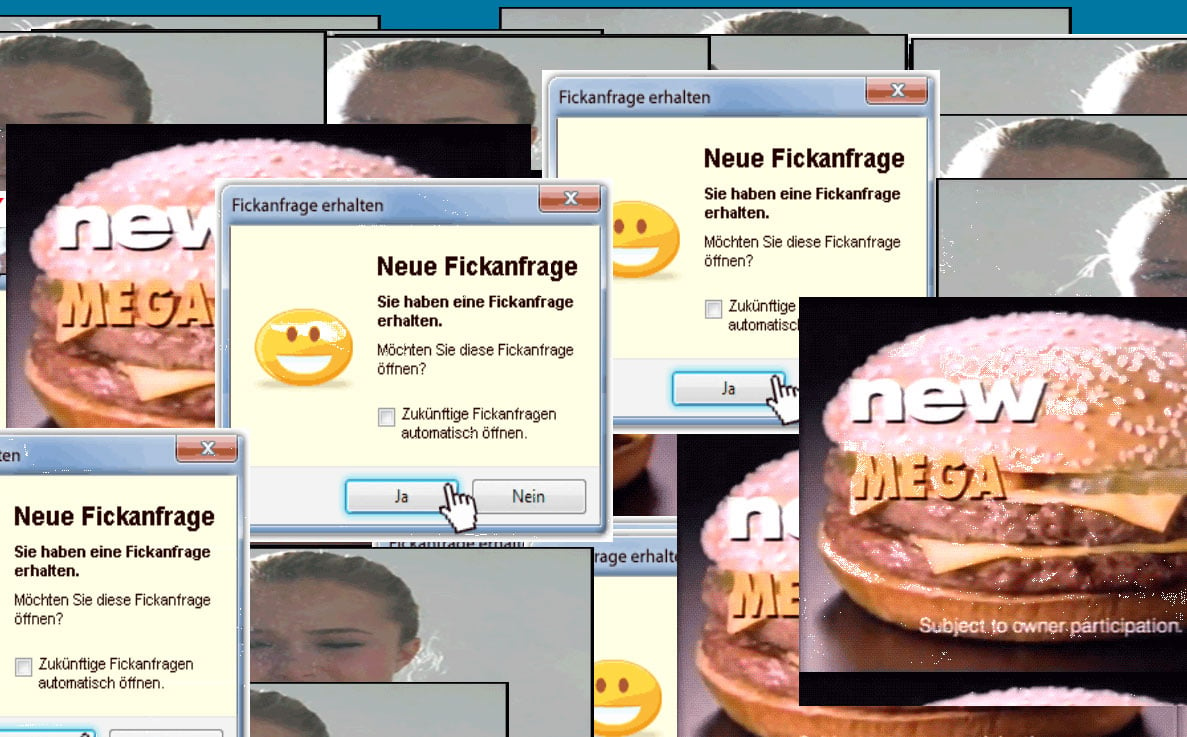
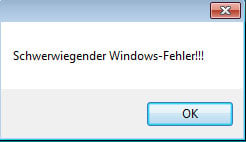
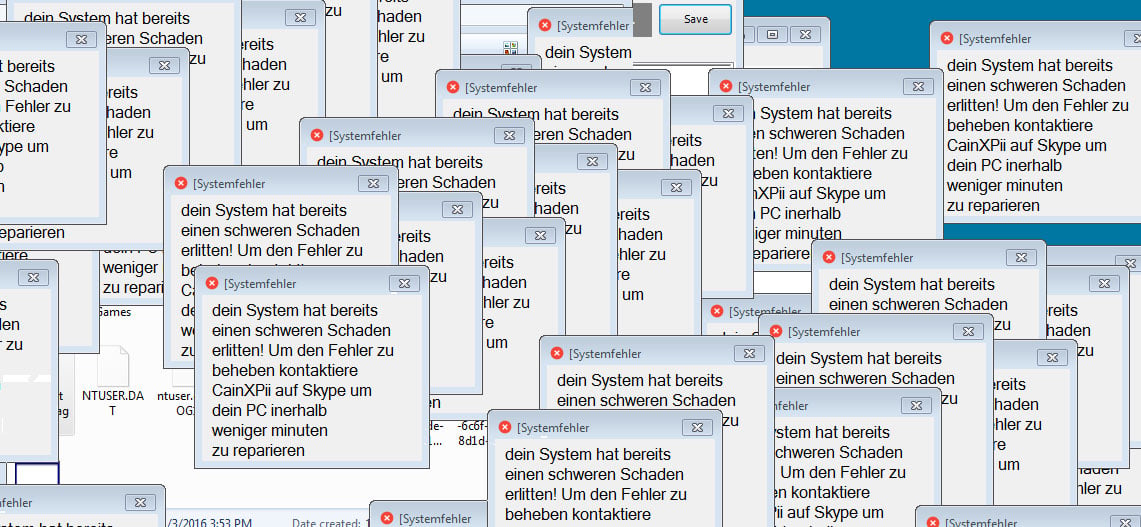
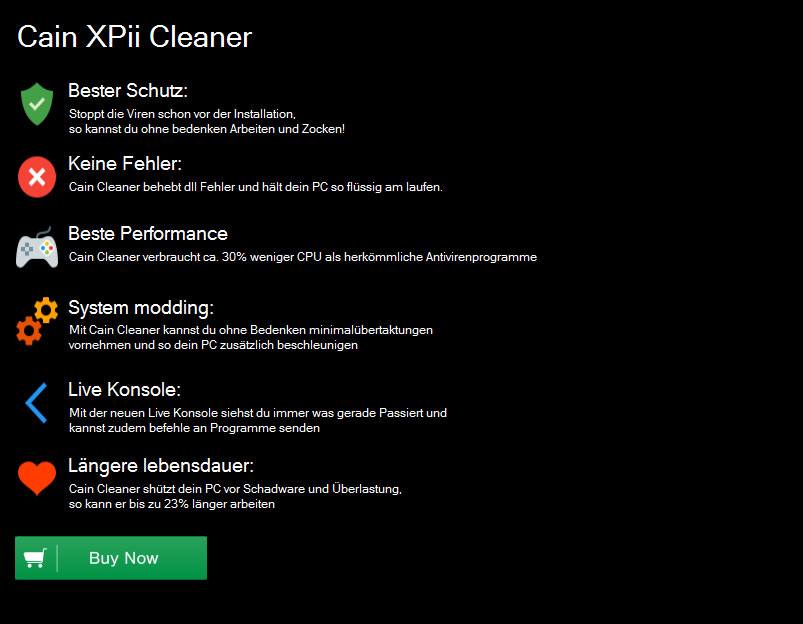
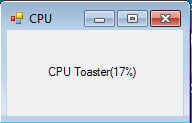
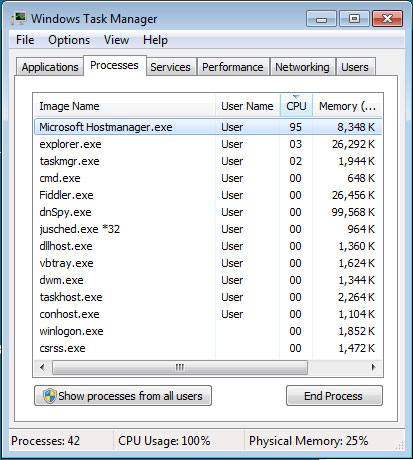
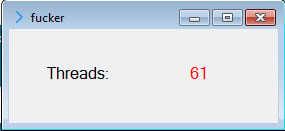
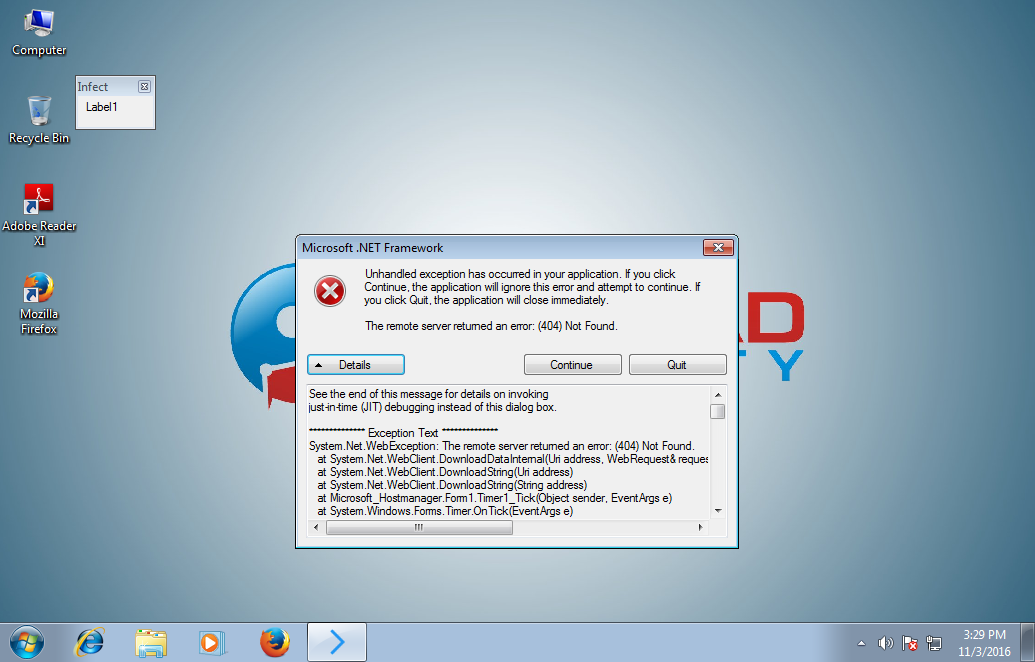
All clues point to this being a future trojan, currently in development, capable of opening fully-functional backdoors on infected systems, most likely for delivering unwanted ads. At this time, current versions of this malware won’t work because the URL it needs to connect is down and returns a 404 error. Speaking to Bleeping Computer, Hahn shares the same opinion, of this being an unfinished threat.
“The malware does not check if there is an Internet connection or if the website works, so it just crashes,” Hahn told Bleeping Computer.
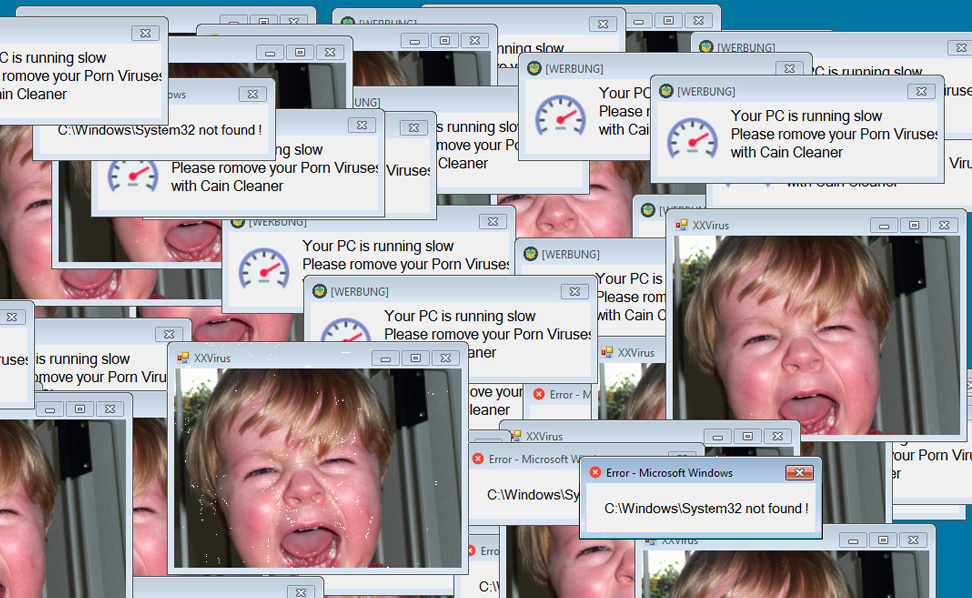
“There is a small screen indicating that the malware is running with the title ‘infect’,” Hahn also added. “You see it in the upper left corner. It looks like this is there for test purposes. So the author knows everything works.”
Because the malware seems to be a work-in-progress and it’s C&C server is down, it’s very likely that its author isn’t distributing this through spam or other means. If he did, we pity the poor souls that have to endure its annoying popups and CPU-killing features.
Source:https://www.bleepingcomputer.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.










