Update DNS provider Dyn has confirmed two massive distributed denial of service attacks against its servers Friday impacting many of its customers including Twitter, Spotify and GitHub. The attacks came in two waves, one early Friday morning and a second just a few hours later.
“This attack is mainly impacting U.S. East and is impacting Managed DNS customers in this region. Our engineers are continuing to work on mitigating this issue,” according to a statement by the company to customers.
As of 5:30 p.m. EDT Dyn was still reporting it was investigating and mitigating several DDoS attacks against its domain name servers.
It’s unclear how many sites have been impacted. For hours Friday morning many popular sites appeared to be experiencing outages or extremely sluggish performance including Twitter, Etsy, Github, SoundCloud, Spotify, Heroku, PagerDuty and Shopify. Dyn representatives would not confirm if each one of these outages was tied to the DDoS attack.
Both the Department of Homeland Security and the Federal Bureau of Investigation said they were monitoring the attacks. Gillian Christensen, acting deputy press secretary for DHS said in a statement: “DHS and FBI are aware and are investigating all potential causes.”
Manchester, New Hampshire-based Dyn said it first began monitoring the DDoS attack at 7:10 a.m. EDT Friday. The company said in a statement to customers:
“Starting at 11:10 UTC on October 21th-Friday 2016 we began monitoring and mitigating a DDoS attack against our Dyn Managed DNS infrastructure. Some customers may experience increased DNS query latency and delayed zone propagation during this time. Updates will be posted as information becomes available.”
Dyn said at 9:36 a.m. EDT, its services were restored and many of its affected customers, including Twitter, were back online. However, at 11:52 a.m. (EDT) Dyn updated its network status reporting an additional attack impacting its managed DNS infrastructure. Then 40 minutes later Dyn added the attacks had spread to its “managed DNS advanced services with possible delays in monitoring.”
It’s unclear, at this time, the source of the DDoS attack, Dyn said.
Dale Drew, chief security officer for telecommunications firm Level 3 Communications said he had been monitoring the attack and the likely source were overseas hackers targeting U.S. cyber infrastructure. He added, via a video statement posted to Periscope, “We are seeing attacks coming from an Internet of Things botnet we have identified as Marai.”
Security firm Flashpoint also identified Marai as the likely culprit in the attack.
The Mirai malware continues to recruit vulnerable IoT devices into botnets at a record pace, one that’s only gone up since the source code for Mirai was made public two weeks ago, according to Level 3.
Craig Young, principle security researcher at Tripwire said the attack has telltale signs of an IoT-based DDoS attack similar to ones experienced by Krebs on Security in September. In those attacks, hackers also used Mirai malware to compromise IoT devices to launch DDoS attacks.
“We are seeing an increase in the number of high-intensity attacks that leverage compromised consumer DVRs and cameras. Without being able to analyze the source of Dyn’s traffic it’s impossible to know for sure. But what we are already seeing today, in terms IoT-based attacks, is the tip of the iceberg,” Young said.
Requests to Dyn for information on the source of the attacks have not been returned.
Young said that security experts have seen an increase in DDoS extortion attempts. However, he points out, many have been hoaxes and when companies didn’t pay up nothing happened.
ForeScout CEO, Michael DeCesare said that attacks, such as the ones carried out Friday, are exasperated by the lack of security in IoT devices.
“These attackers can now recruit an army of IoT devices to launch a wide scale DDoS attack due to the volume of these devices and their ease of infiltration,” DeCesare said in a prepared statement regarding Friday’s attacks.
“The question corporations should be asking themselves is whether or not their devices are being exploited as part of these attacks. The solution starts with visibility – you cannot secure what you cannot see,” he said.
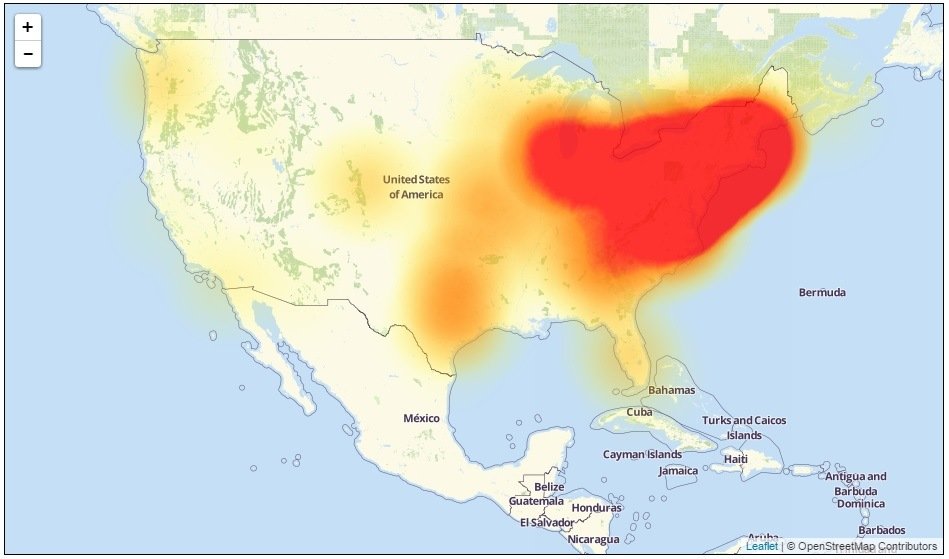
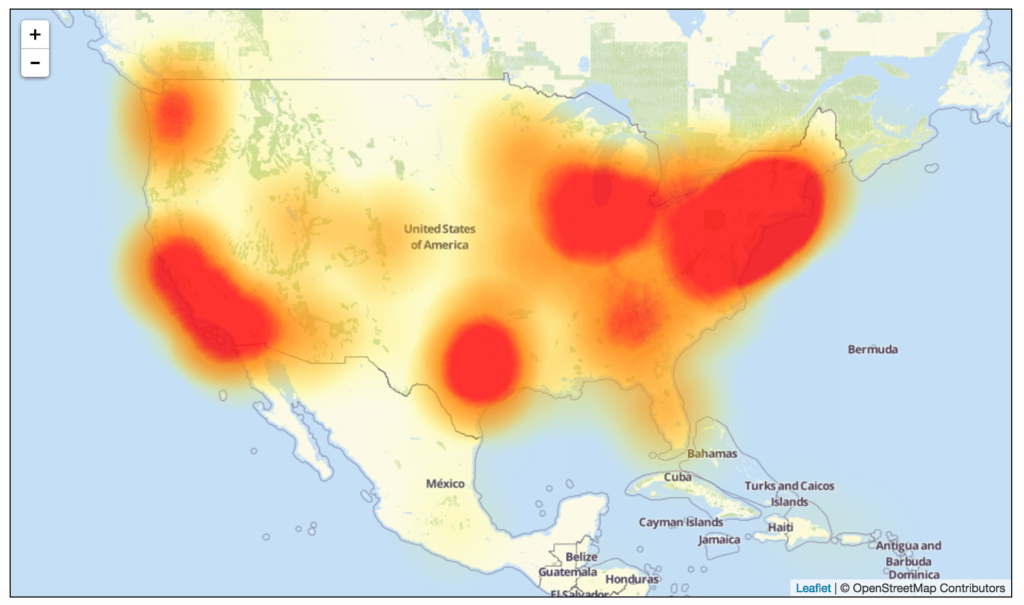
Level3 live outage map on Friday 9:50 AM (EDT) Level3 live outage map on Friday 5:20 PM (EDT) This article was updated Oct. 21 at 5:30 p.m. with new information from the Department of Homeland Security, new information tying the attacks to Mirai malware and quotes from both Level 3 Communications and ForeScout.
Source:https://threatpost.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











