Yesterday, GData malware analyst Karsten Hahn discovered an in-development ransomware disguised as a click me game. When executed the ransomware will launch a screen that contains a Click Me button that a user chases around the screen with their mouse cursor while trying to click on it. In the background, though, the ransomware will be silently encrypting the data on the drive.
This ransomware is currently in-development, which means that it does not contain the full functionality required to make it a viable ransomware. For example, though it does encrypt a file, it currently only targets the file located at D:\ransom-flag.png. Any other files on a computer will not be affected by this ransomware.
// Token: 0x06000007 RID: 7 RVA: 0x00002439 File Offset: 0x00000639
public void DoJob()
{
this.Encrypt_file("D:\\ransom-flag.png");
}
When encrypting files it will use AES encryption and encrypted files will have the .hacked extension appended to the filename.
As shown in the video above, when executed the ransomware will display a screen that pretends to be a click me game. As the user clicks on the button, it will show a different background screen.
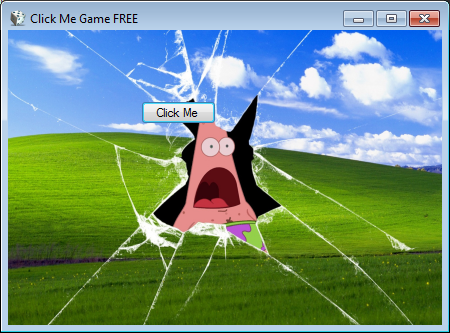
Eventually, if you click the button enough times or press enter, it will show the following ransom note screen.
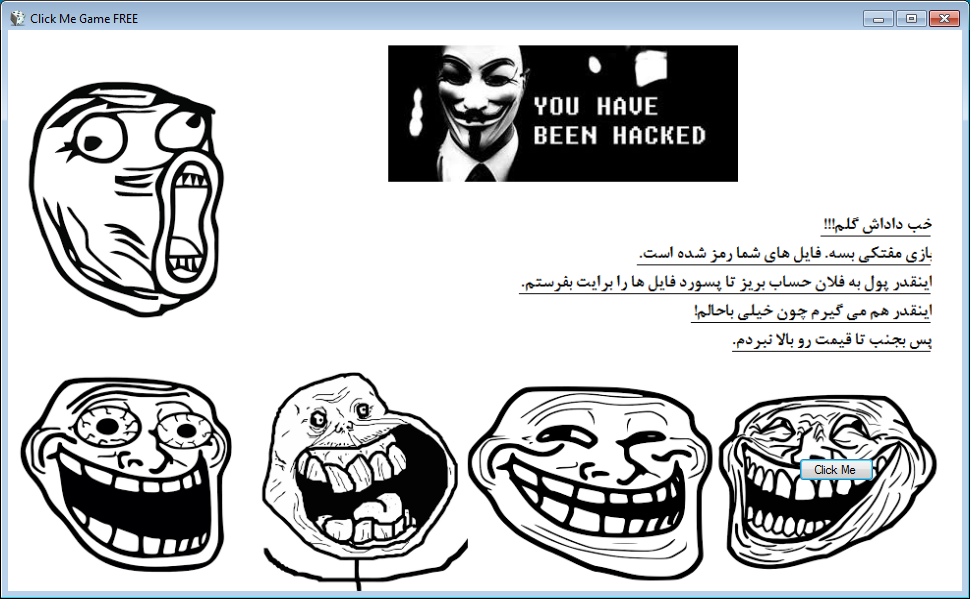
This ransom note contains a picture of Anonymous with the text You have been Hacked. It also contains text that I was told is Farsi that asks for payment to get the files back. A big thanks to مسعود الفارسي for translating this text to English, which is found below.
Alright my dear brother!!!
Enough free playing. Your files have been encrypted. Pay so much this much money so I can send you the password for your files.
I can be paid this much too cause I am very kind.
So move on I didn't raise the price.
The text of this ransom note is further indication that the malware is still in development because it does not contain any payment instructions such as an email address or payment site.
At this time this ransomware is currently not being distributed and there is a good chance it never will be. If this changes and someone encounters this ransomware in the wild, please let me know in the comments and we can further analyze the newer version for weaknesses.
Source:https://www.bleepingcomputer.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











