According to security researcher Timothy Davies, a new version of the Locky Ransomware, aka Zepto, has been circulating since around the September 5th 2016 that includes an embedded RSA key. This key allows Locky to encrypt a victim’s computer without having to contact their Command & Control server. As many system administrators block Command & Control servers on their firewalls, by using an embedded RSA key, Locky can encrypt a computer regardless of what has been blocked at the edge.
The good news is that this version is having distribution problems as there attachments are not being named properly. For example, a current campaign is using ZIP attachments that contain JS files. When executed, these files are giving an error as seen below.
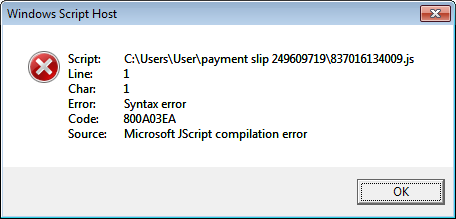
This error is occurring because the attachments are actually HTA files and not JS files. Once the file is renamed to HTA, it works properly.
Other than that, this version continues to append the .ZEPTO extension to encrypted files and create ransom notes that are named %Desktop%\[number]_HELP_instructions.html, %Desktop%\_HELP_instructions.html, and %Desktop%\_HELP_instructions.bmp.
This version is targeting the following extensions for encryption:
.ARC, .CSV, .DOC, .DOT, .MYD, .MYI, .NEF, .PAQ, .PPT, .RTF, .SQLITE3, .SQLITEDB, .XLS, .aes, .apk, .asc, .asf, .asm, .asp, .asset, .avi, .bak, .bat, .bik, .bmp, .brd, .bsa, .cgm, .class, .cmd, .cpp, .crt, .csr, .d3dbsp, .das, .dbf, .dch, .dif, .dip, .djv, .djvu, .docb, .docm, .docx, .dotm, .dotx, .fla, .flv, .forge, .frm, .gif, .gpg, .hwp, .ibd, .iwi, .jar, .java, .jpeg, .jpg, .key, .lay, .lay6, .lbf, .ldf, .litemod, .litesql, .ltx, .max, .mdb, .mdf, .mid, .mkv, .mml, .mov, .mpeg, .mpg, .ms11 (Security copy), .odb, .odg, .odp, .ods, .odt, .onetoc2, .otg, .otp, .ots, .ott, .pas, .pdf, .pem, .php, .png, .pot, .potm, .potx, .ppam, .pps, .ppsm, .ppsx, .pptm, .pptx, .psd, .pst, .qcow2, .rar, .raw, .sav, .sch, .sldm, .sldx, .slk, .sql, .stc, .std, .sti, .stw, .svg, .swf, .sxc, .sxd, .sxi, .sxm, .sxw, .tar, .tar.bz2, .tbk, .tgz, .tif, .tiff, .txt, .uop, .uot, .upk, .vbs, .vdi, .vmdk, .vmx, .vob, .wallet, .wav, .wks, .wma, .wmv, .xlc, .xlm, .xlsb, .xlsm, .xlsx, .xlt, .xltm, .xltx, .xlw, .xml, .zip
Source:https://www.bleepingcomputer.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











