A mobile banking trojan called Trojan-Banker.AndroidOS.Gugi.c, or “Gugi” for short, found no problem bypassing a couple of the security measures introduced in Android 6.
The name of the game is social engineering when it comes to a Gugi infection.
According to Kaspersky Lab’s senior malware analyst Roman Unuchek, the trojan first infects a device by posing as a spam SMS message that reads as follows:
“Dear user, you receive MMS-photo! You can look at it by clicking on the following link.”
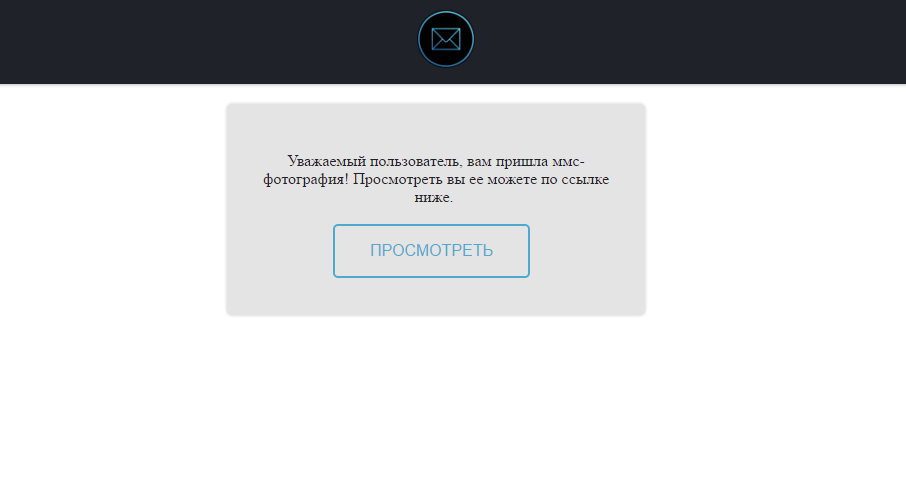
If clicked, the link begins downloading Gugi onto the device.
The malware then faces its first test.
In response to an expanding field of Android ransomware–which includes samples that havemasqueraded as adult apps, infected Android smart TVs, and demanded ransom in the form of iTunes gift cards–Google built into Android 6 a feature that requires an app to request permissions if it wants to overlay its window over another app.
For Gugi, that’s nothing a little social engineering can’t fix. As Unuchek explains:
“The first thing an infected user is presented with is a window with the text ‘Additional rights needed to work with graphics and windows’ and one button: ‘provide.’… After clicking on this button, the user will see a dialog box that authorizes the app overlay (‘drawing over other apps’).”
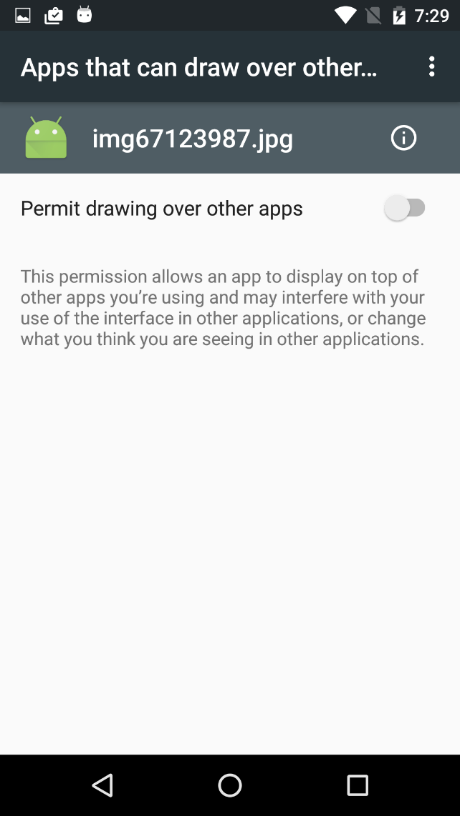
Flipping that switch surrenders control of the device to Gugi. Indeed, with the ability to overlay other apps, the trojan initiates a series of requests for additional permissions by abusing another feature of Android 6: a dynamic request capability that allows mobile apps to ask for additional permissions after they have been installed.
Among other things, Gugi requests to be made device administrator, a status which allows the malware to act as a regular mobile banking trojan by opening up phishing pages for banking credentials and stealing contacts/SMS messages off the device.
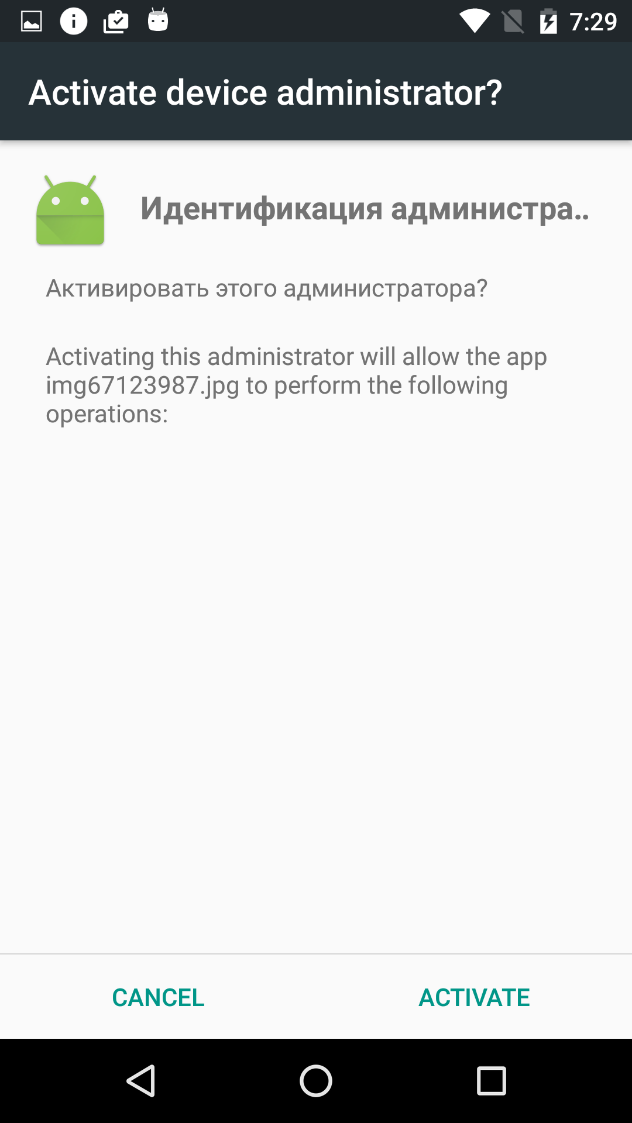
If the user denies Gugi’s requests, they face their own set of consequences, as Unuchek rightly notes:
“Should the user deny permission, subsequent requests will offer them the option of closing the request. If the Trojan does not receive all the permissions it wants, it will completely block the infected device. In such a case the user’s only option is to reboot the device in safe mode and try to uninstall the Trojan.”
Currently, Gugi is targeting users living in Russia primarily, but it could set its sights on other demographics in the coming weeks and months.
Kaspersky Lab intends to release a report on Gugi soon. In the meantime, users should protect themselves against an infection by exercising caution around suspicious links and email attachments, by reviewing app permission requests carefully, and by keeping an up-to-date antivirus solution installed on their devices.
Source:https://www.bleepingcomputer.com

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.










