With only a small amount of work, ExtraBacon will commandeer new versions of ASA. Recently released code that exploits Cisco System firewalls and has been linked to the National Security Agency can work against a much larger number of models than many security experts previously thought.
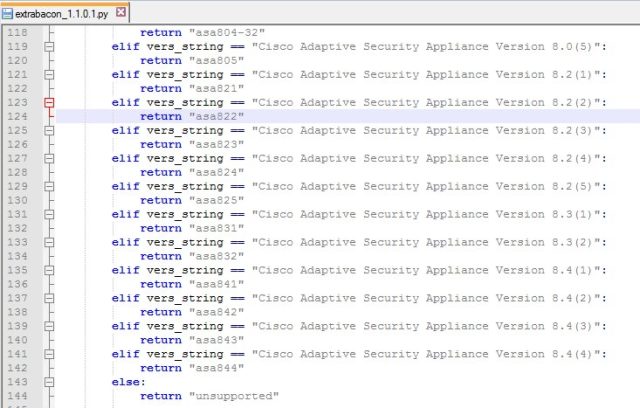
An exploit dubbed ExtraBacon contains code that prevents it from working on newer versions of Cisco Adaptive Security Appliance (ASA), a line of firewalls that’s widely used by corporations, government agencies, and other large organizations. When the exploit encounters 8.4(5) or newer versions of ASA, it returns an error message that prevents it from working. Now researchers say that with a nominal amount of work, they were able to modify ExtraBacon to make it work on a much newer version. While Cisco has said all versions of ASA are affected by the underlying vulnerability in the Simple Network Messaging Protocol, the finding means that ExtraBacon poses a bigger threat than many security experts may have believed.
The newly modified exploit is the work of SilentSignal, a penetration testing firm located in Budapest, Hungary. In an e-mail, SilentSignal researcher Balint Varga-Perke wrote: We first started to work on the exploit mainly to see how easy it would be to add support for other (newer) versions. Turns out it is very easy, that implies two things:
- The leaked code is not as poor quality as some might suggest
- The lack of exploit mitigation techniques in the target Cisco software makes the life of attackers very easy
As Ars previously reported, the zero-day exploit allows remote attackers who have already gained a foothold in a targeted network to take full control of a firewall. It was one of more than a dozen highly advanced attacks that was part of a mysterious leak by a previously unknown group calling itself the ShadowBrokers. Researchers say digital fingerprints left inside the code all but prove the attacks belonged to the Equation Group, an elite hacking crew with ties to the NSA-sponsored Stuxnet and Flame malware that targeted Iran and the Middle East.
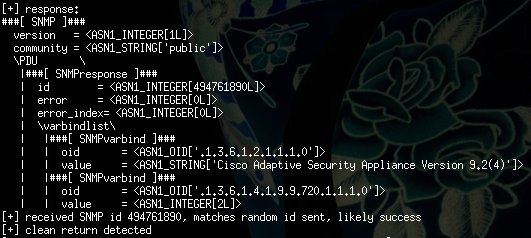
Michael Toecker, an engineer at a firm called Context Industrial Security, has analyzed ExtraBacon and found that it was designed to work only with versions 8.4(4) and earlier of ASA. He provided the following screenshot to illustrate the restrictions.

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











