“Off-path” attack means hackers can be anywhere with no man-in-the-middle needed.
Computer scientists have discovered a serious Internet vulnerability that allows attackers to terminate connections between virtually any two parties and, if the connections aren’t encrypted, inject malicious code or content into the parties’ communications.
The vulnerability resides in the design and implementation of RFC 5961, a relatively new Internet standard that’s intended to prevent certain classes of hacking attacks. In fact, the protocol is designed in a way that it can easily open Internet users to so-called blind off-path attacks, in which hackers anywhere on the Internet can detect when any two parties are communicating over an active transmission control protocol connection. Attackers can go on to exploit the flaw to shut down the connection, inject malicious code or content into unencrypted data streams, and possibly degrade privacy guarantees provided by the Tor anonymity network.
At the 25th Usenix Security Symposium on Wednesday, researchers with the University of California at Riverside and the US Army Research Laboratory will demonstrate a proof-of-concept exploit that allows them to inject content into an otherwise legitimate USA Today page that asks viewers to enter their e-mail and passwords. The malicious, off-site JavaScript code attack is possible because the vulnerable USA Today pages aren’t encrypted. Even if they were protected, attackers could still terminate the connection. Similar attacks work against a variety of other unidentified sites and services, as long as they have long-lived connections that give hackers enough time—roughly 60 seconds—to carry out the attack.
The researchers have also provided the following video demonstration:
Top sites remain vulnerabl
The problematic RFC 5961 has not yet been fully implemented in Windows or Mac OS X, so those operating systems aren’t believed to be vulnerable. By contrast, the Linux operating system kernel, starting with version 3.6 introduced in 2012, has added a largely complete set of functions implementing the standard. Linux kernel maintainers released a fix with version 4.7 almost three weeks ago, but the patch has not yet been applied to most mainstream distributions. For the attack to work, only one of the two targeted parties has to be vulnerable, meaning many of the world’s top websites and other services running on Linux remain susceptible.
In an accompanying research paper titled Off-Path TCP Exploits: Global Rate Limit Considered Dangerous, the researchers said the vulnerability is the result of changes in the way TCP establishes a connection. When carrying out a so-called three-way handshake, the first of two parties sends a SYN (short for synchronize) packet, the receiving party responds with a SYN-ACK (synchronize-acknowledgement) packet, and the connection is established when the first party sends an ACK packet.
While similar attacks have existed for several years, the introduction of RFC 5961 makes this new exploit much more powerful. That’s because the attacker need only have an Internet connection, even when there’s no man-in-the-middle ability to control or monitor traffic passing between the two parties. The researchers wrote:
In this paper, we discover a much more powerful off-path attack that can quickly 1) test whether any two arbitrary hosts on the Internet are communicating using one or more TCP connections (and discover the port numbers associated with such connections); 2) perform TCP sequence number inference which allows the attacker to subsequently, forcibly terminate the connection or inject a malicious payload into the connection. We emphasize that the attack can be carried out by a purely off-path attacker without running malicious code on the communicating client or server. This can have serious implications on the security and privacy of the Internet at large.
The root cause of the vulnerability is the introduction of the challenge ACK responses and the global rate limit imposed on certain TCP control packets. The feature is outlined in RFC 5961, which is implemented faithfully in Linux kernel version 3.6 from late 2012. At a very high level, the vulnerability allows an attacker to create contention on a shared resource, i.e., the global rate limit counter on the target system by sending spoofed packets. The attacker can then subsequently observe the effect on the counter changes, measurable through probing packets.
Through extensive experimentation, we demonstrate that the attack is extremely effective and reliable. Given any two arbitrary hosts, it takes only 10 seconds to successfully infer whether they are communicating. If there is a connection, subsequently, it takes also only tens of seconds to infer the TCP sequence numbers used on the connection. To demonstrate the impact, we perform case studies on a wide range of applications.
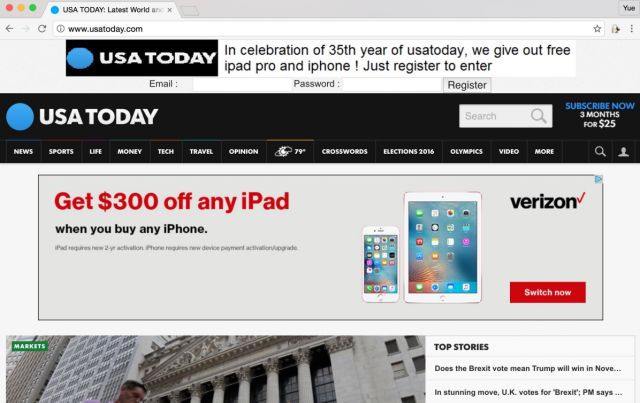
Besides injecting malicious JavaScript into a USA Today page, the researchers also show how the vulnerability can be exploited to break secure shell, or SSH, connections and tamper with communications traveling over Tor. In the latter case, attackers can terminate key links in the Tor chain—for instance, those connecting an end user to an entry node, an entry node to a middle relay, or a middle relay to the exit node. The Tor attack could be particularly effective if it knocked out properly functioning exit nodes because the technique would increase the chances that connections would instead use any malicious exit nodes that may exist.
“In general, we believe that a DoS attack against Tor connections can have a devastating impact on both the availability of the service as a whole and the privacy guarantees that it can provide,” the researchers wrote. “The default policy in Tor is that if a connection is down between two relay nodes, say a middle relay and an exit relay, the middle relay will pick a different exit relay to establish the next connection. If an attacker can dictate which connections are down (via reset attacks), then the attacker can potentially force the use of certain exit relays.”
The researchers went on to offer a workaround solution while administrators of vulnerable systems wait for a permanent fix. While Windows, OS X, and most other operating systems aren’t believed to be vulnerable, the researchers warned that they could become susceptible if developers don’t use extreme care when more fully implementing RFC 5961.
“It is a subtle problem,” researcher Zhiyun Qian told Ars when asked if the vulnerability resided in the RFC specification itself or a specific implementation of it. “I want to say that the RFC is written in a way that if OSes implement it straightforwardly, it is going to be problematic. So I think we should probably split the responsibility between the RFC and implementation.”
Source:https://arstechnica.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.










