Our team recently discovered a new Android Trojan called SpyNote which facilitates remote spying. The builder, which creates new versions of the malware, recently leaked on several malware discussion forums. SpyNote is similar to OmniRat and DroidJack, which are RATs (remote administration tools) that allow malware owners to gain remote administrative control of an Android device.
Like these other RATs, SpyNote has a large feature set including the following:
- No root access required
- Install new APKs and update the malware
- Copy files from device to computer
- View all messages on the device
- Listen to calls made on the device
- List all the contacts on the device
- Listen live or record audio from the device’s microphone
- Gain control of the camera on the device
- Get IMEI number, Wi-Fi MAC address, and cellphone carrier details
- Get the device’s last GPS location
- Make calls on the device
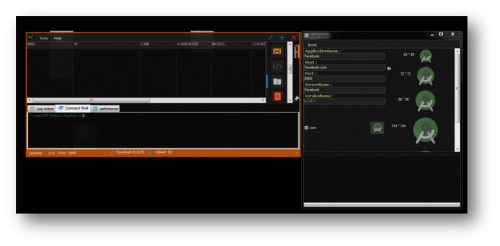
Figure 1: SpyNote Control Panel
The SpyNote APK requires victims to accept and give SpyNote many permissions, including the ability to edit text messages, read call logs and contacts, or modify or delete the contents of the SD card. We have found that a sample of SpyNote was uploaded to the VirusTotaland Koodous malware analysis websites.
Analysis
Upon installation, SpyNote will remove the application’s icon from the victim’s device. Also apparent is that the SpyNote builder application is developed in .NET
The application is neither obfuscated nor protected with any Obfuscator or Protector.
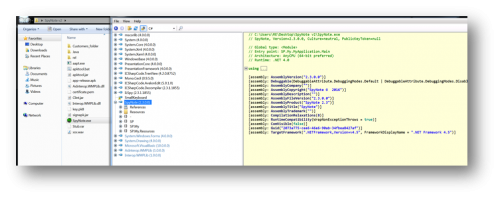
Figure 2: Decompiled SpyNote Builder
The uploader might be following the instructions described in YouTube videos on using SpyNote, considering the port number used is exactly the same as in the videos (https://www.youtube.com/watch?v=E9OxlTBtdkA) and the uploader only changes the icon of the APK file.
Furthermore, this RAT has been configured to communicate to the command and control (C&C) IP address (141.255.147.193) over TCP port 2222 as shown in the image below.
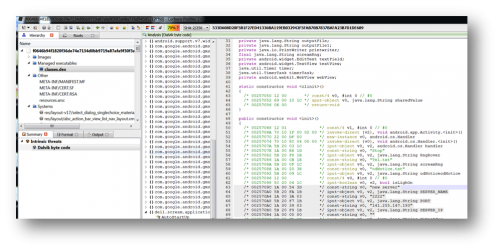
Figure 3 – Dalvik bytecode view using Cerbero profiler
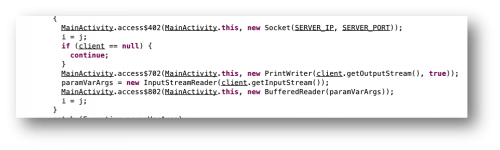
Figure 4 – SpyNote opening a socket connection
Based on the information we have already found, we now know that the malware is using the hard-coded SERVER_IP and SERVER_PORT values (Figure 4) for this socket connection. We can now create an extractor for the C2 information using Androguard (https://github.com/androguard/androguard) as shown below. The spynote.C2.py script (shown below) parses these values from the APK file and prints them to the command line (Figure 5).
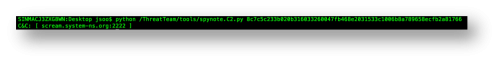
Figure 5 – Extracted C2 information
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
|
#!/usr/bin/python
import sys
from sys import argv
from androguard.core.bytecodes import apk
from androguard.core.bytecodes import dvm
#—————————————————
# _log : Prints out logs for debug purposes
#—————————————————
def _log(s):
print(s)
if __name__ == “__main__”:
if (len(sys.argv) < 2):
_log(“[+] Usage: %s [Path_to_apk]” % sys.argv[0])
sys.exit(0)
else:
a = apk.APK(argv[1])
d = dvm.DalvikVMFormat(a.get_dex())
for cls in d.get_classes():
#if ‘Ldell/scream/application/MainActivity;’.lower() in cls.get_name().lower():
if ‘dell/scream/application/MainActivity;’.lower() in cls.get_name().lower():
c2 = “”
port = “”
string = None
for method in cls.get_methods():
if method.name == ‘<init>’:
for inst in method.get_instructions():
if inst.get_name() == ‘const-string’:
string = inst.get_output().split(‘,’)[–1].strip(” ‘”)
if inst.get_name() == ‘iput-object’:
if “SERVER_IP” in inst.get_output():
c2 = string
if “PORT” in inst.get_output():
port = string
if c2 and port:
break
server = “”
if port:
server = “{0}:{1}”.format(c2, str(port))
else:
server = c2
_log(‘C&C: [ %s ]’ % server)
|
Conclusion
Installing apps from third-party sources can be very risky — those sources often lack the governance provided by official sources such as the Google Play Store, which, even with detailed procedures and algorithms to weed out malicious applications, is not impregnable. Side-loading apps from questionable sources exposes users and their mobile devices to a variety of malware and possible data loss.
Source:https://researchcenter.paloaltonetworks.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











