A lot has been said about the ransomware epidemic. The number of infections worldwide increases daily, as well as the number of different variants. Check Point researchers have been analyzing ransomware for almost two years, and it has been a fascinating study.
We can easily follow the trends, common aspects, and differences between ransomware families. As each wave of ransomware is countered by new security measures, ransomware adapts and changes directions to successfully bypass them, in an endless game of cat and mouse.
Incoming: ransomware
Ransomware has many variants, and each family’s execution flow is unique. However, despite these differences, all families share common traits, which allow security vendors to identify and create protections against them.
CryptoWall was the harbinger of the first wave of ransomware. As seen below, it used known Windows binaries for encryption and C&C communication. Together with polymorphism of other techniques, CryptoWall managed to easily evade signature-based anti-virus protections.
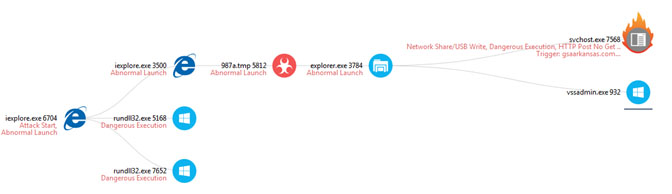
Figure 1 – CryptoWall 3, 4 variants context execution tree
Locky and TeslaCrypt refined their evasion techniques. They changed the code in runtime, camouflaging API calls to misdirect researchers and sandbox static analysis. These techniques were not new to malware in general, but were applied to ransomware relatively late.
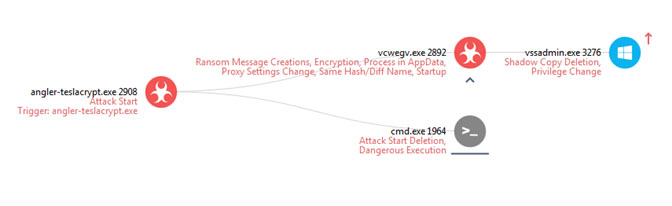
Figure 2 – TeslaCrypt variant: forensic signatures
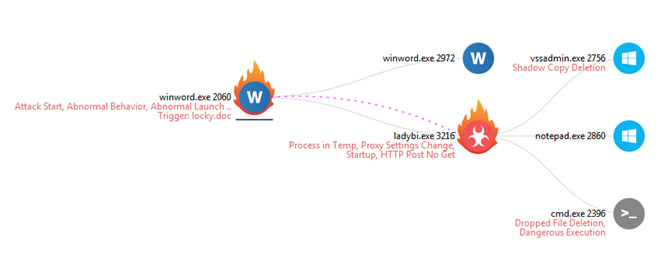
Figure 3 – Locky variant execution tree
In addition, completely new actors entered the scene, bringing new techniques and consequently new challenges for protectors. The new actors included Petya, Hydracrypt, Cerber, and many others.
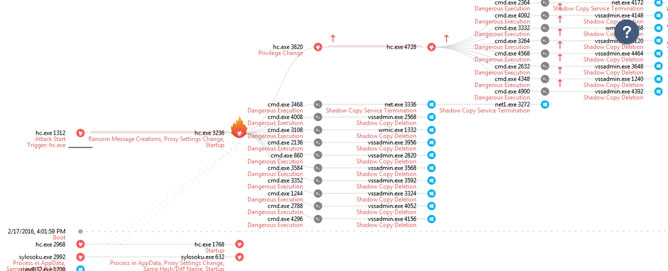
Figure 4 – HydraCrypt execution tree – deleting shadow copies for all drive letters
So what do they have in common?
At first glance, the implementation looks slightly different. However, most of the features are common to all of the first-wave ransomware families:
- Run-injected instances of Windows binaries to do most of the malicious activity
- Use Windows common binaries to delete shadow copies to block recovery
- Use Windows binaries (like Notepad.exe and photo viewer) and browsers to display the ransom messages
- Use Windows Registry RUN and RUNONCE keys for persistence, as well as the startup Windows folder
- Delete the initial sample to avoid further analysis
- Receive/send the encryption key from the C&C
- Present ransom message in 2-3 different formats, including text and HTML
- Execute the encryption in a subsequent instance
Spreading the word – 2016 ransomware “home” editions
As the ransomware trend gained more attention, many malware developers realized it is a great business, and a new wave of “home” editions emerged. Attackers find developing ransomware very attractive for several resons. Thanks to anonimizers, there is a relatively low chance of getting caught, and the actual coding of the ransomware is simple. In fact, most of the code is available in GIT or as a service. To make it even simpler, you can use code sources like MSDN that give you code samples to correctly encrypt files using Windows encryption APIs. Even so, most “home” attackers seemingly didn’t even try to do it properly.
Ransomware such as Jigsaw, Badlock, or Kovter didn’t put a lot of effort into unbreakable encryption, or professional evasion techniques. The attackers’ motto seemed to be the simpler, and the scarier, the better. Instead of investing in development, they invested in displaying a scary picture. While these “home” edition encryptions are easily breakable, the ransomware remains profitable, as the average user doesn’t know how to deal with them.
Unlike the previous “professional” wave, these later ransomware don’t execute any shadow copy deletion, self deletion, or advanced evasion techniques. The common trait among them, apart from what they don’t do, is the fact that they use their own binaries to execute the activity, without injections and usage of other binaries.
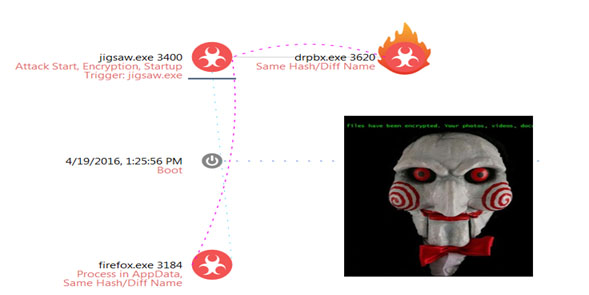
Figure 5 – Jigsaw
Joining the party – the current wave of ransomware
Following the “home” edition of ransomware, in the current wave, most of the previously named indicators are simply not present. This new wave includes ransomware like Samsam, Maktub, CTB Locker, and latelyCryptXXX. Most of them are professionally packaged and well-obfuscated pieces of code.
The most common feature these ransomware variants share are that instead of creating their own instances, they use already running binaries to perform malicious activities. This behavior makes the ransomware harder to detect, as those binaries are very common and are used to perform many different tasks.
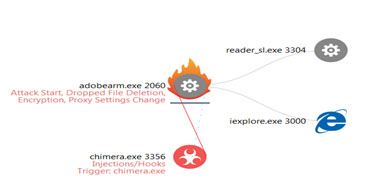
Figure 6 – Chimera
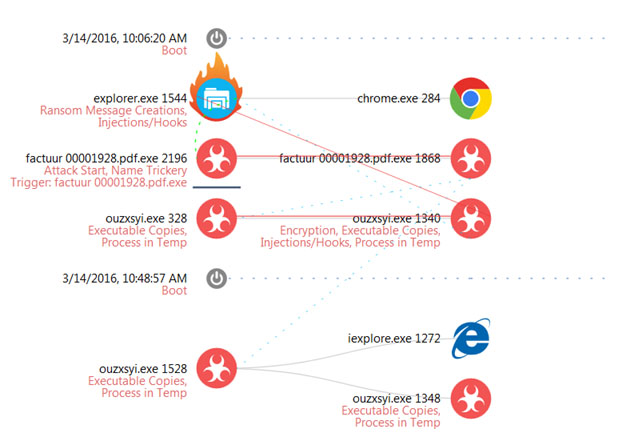
Figure 7 – CTB Locker
Looking ahead – the future of ransomware
It is still too early to determine the future of ransomware. However, as compared to other malware, we know that there is plenty of room for ransomware to continue to evolve and change tactics. Ransomware remains an excellent example of the nature of cyber threats: agile, adaptable, and simple in essence. Check Point researchers will continue to follow ransomware wherever it may go to keep users one step ahead.

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











