The BadBlock Ransomware is one poorly coded and horribly designed ransomware as it not only encrypts your files, but also trashes your system. Unlike almost all other ransomware infections, BadBlock will not only encrypt your data files, but it will also encrypt the executables on your computer, including important Windows system files. You starting to see the issue here?
This means that if you reboot your computer after BadBlock encrypts your machine, you will find that the computer will no longer starts. This is because required executables have been encrypted as shown by the image below.
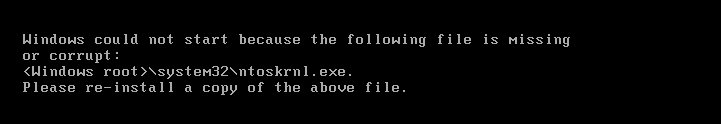
Source: Dell
Furthermore, most ransomware infections do not like to advertise their presence until after all of the encryption has been completed. BadBlock, on the other hand, goes in the opposite direction and clearly tells you what it is doing while it is doing it.
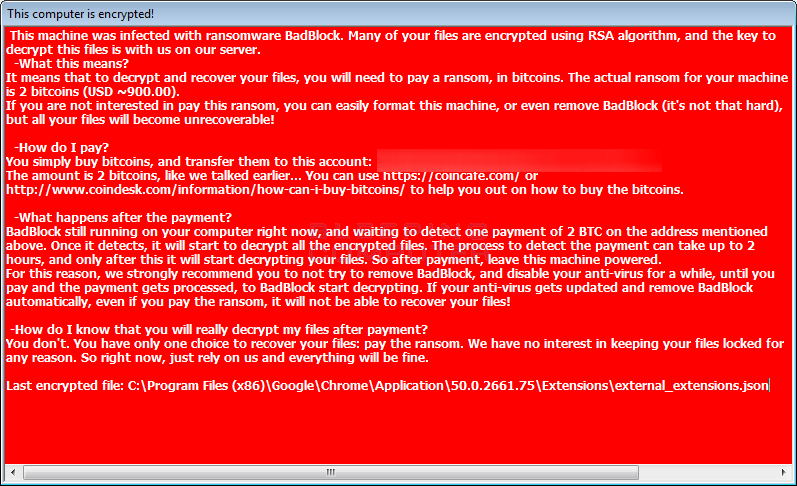
Since a user will know when BadBlock is encrypting their files, they can easily go into Task Manager and terminate the badransom.exe process in order to stop encryption.
Thankfully, for those who have been affected by BadBlock, Fabian Wosar ofEmisoft has released a free decryptor. Instructions for using this decryptor can be found below.
Decrypting BadBlock
If you are infected with this malware, simply download decrypt_badblock.exefrom the following link and save it on your desktop:
BADBLOCK DECRYPTOR
In order to find your decryption key, you need to drag an encrypted file and unencrypted version of the same file onto the decrypt_hydracrypt.exe icon at the same time. So you would select both the encrypted and unencrypted version of a file and drag them both onto the executable. If you do not have an an original version of one of your encrypted files, in our tests you can use a encrypted PNG file and any other unencrypted PNG file that you get off of the Internet and drag them together onto the decrypt_badblock.exe icon. Once you determine the key used to encrypt one of your files, you can then use that key to decrypt ALL other files on your computer.
To show what I mean about dragging both files at the same time, see the example below. To create the key, I created a folder that contains an encrypted PNG file, a totally different valid PNG file, and the decrypt_badblock.exe program. I then dragged both the regular PNG file and the encrypted one onto the executable at the same time.
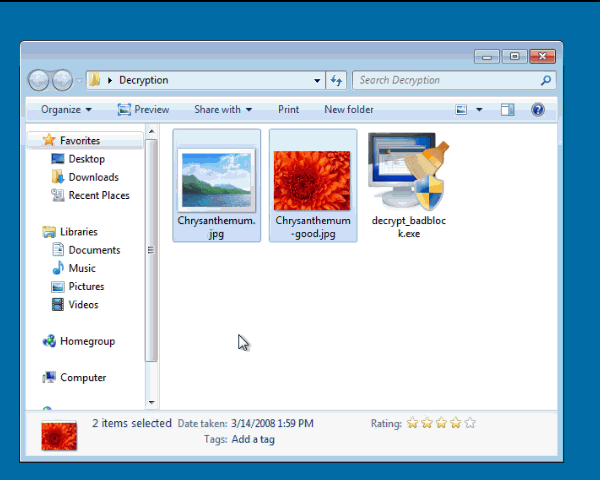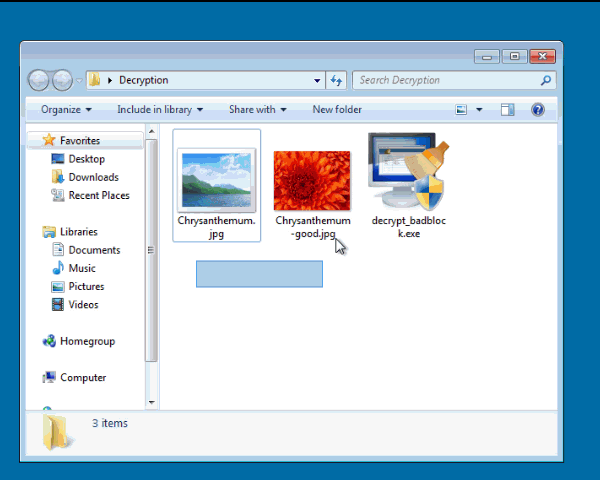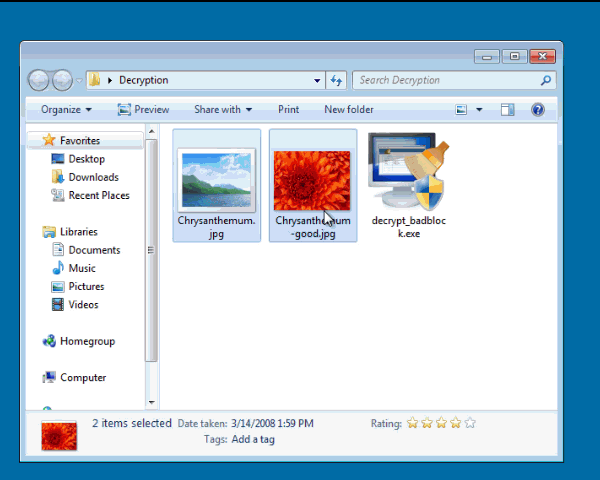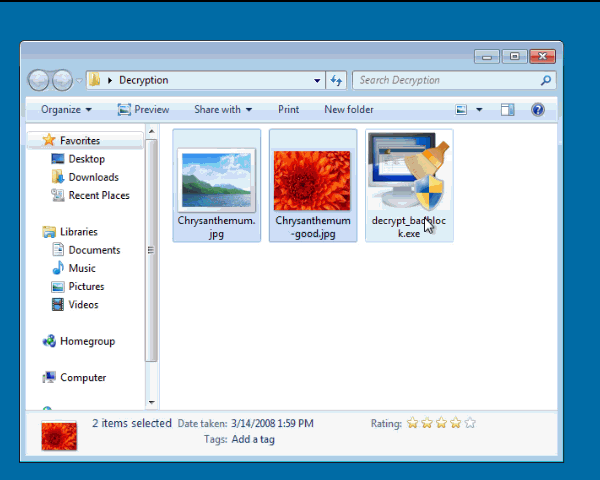
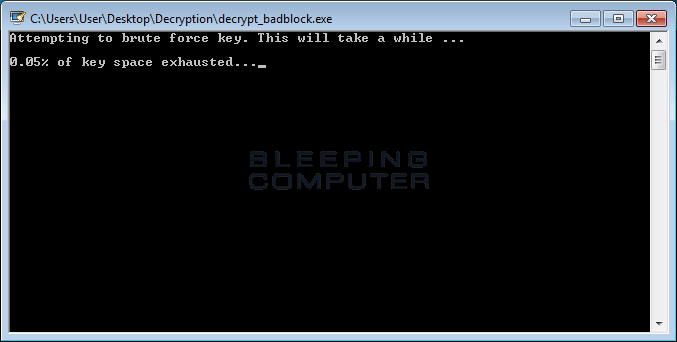
When the program starts, you will be presented with a UAC prompt as shown below. Please click on Yes button to proceed. The BadBlock Decryptor will now attempt to brute force the decryption key.
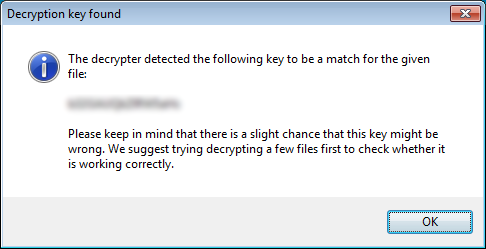
When a key was able to be brute forced, it will display it an a new window like the one below. Please write down this key in the event you need it again in the future.
To start decrypting your files with this key, please click on the OK button. You will then be presented with a license agreement that you must click on Yes to continue. You will now see the main decryptor screen with the C: drive set to be decrypted. If there are other drives or folders, please add them using the Add Folder button.
When ready, click on the Decrypt button to decrypt all of the encrypted files and display the decryption status in a results screen like the one below.
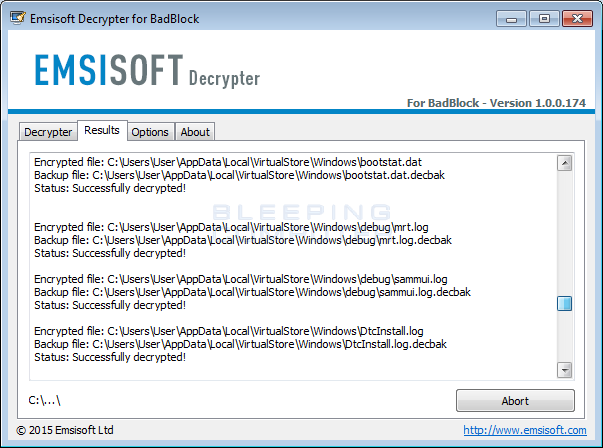
When the program is finished, all of your should now be decrypted.
Source:https://www.bleepingcomputer.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











