Most of popular botnet Andromeda’s (also known as Gamarue) distribution channels have been discovered and analyzed by antivirus vendors. This has forced Andromeda’s distributors to come up with a new attack strategy to continue to drop Andromeda binaries onto PCs.
Meanwhile at the Andromeda headquarters…
Operator: “Captain, all of our distribution channels have been discovered!”
Captain: “Report the loss..”
Operator: “Email scams, exploit kits, everything is known to the public.”
Captain: “Operator, let’s start with plan N!”
Operator: “Roger that, captain”
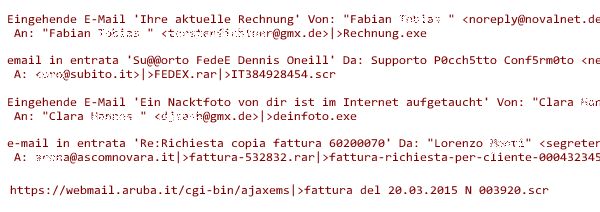
Before we dive into Andromeda’s new tactic, I’d recommend you to read this article by fellow security researchers from Stormshield, which describes one of Andromeda’s most recent phishingcampaigns. We have observed similar Andromeda email phishing campaigns. Most of the emails we have seen seem to be targeting Germans and Italians. However, these two target groups seem to be too clever to fall for the bait, as they are not the top infected users.
Some of the popular subject lines used to target Germans and Italians are “Your current bill” and “A nude photo of you has appeared on the Internet”.
Another popular method used to spread Andromeda is via a Nuclear exploit kit, which can be distributed, for example, through phishing campaigns or infected advertising systems. After exploiting a particular vulnerability on a victim’s PC, the Nuclear exploit kit typically leads to a URL, which then downloads a dropper. The URL looks like this:
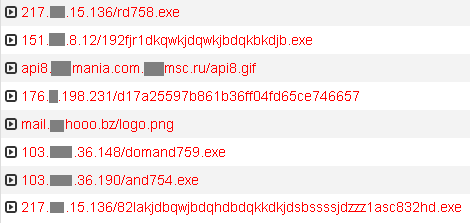
Once the dropper is downloaded, the infection chain described in our previous Andromeda blog post begins. This was the method Andromeda’s distributors had been previously using, but they have now moved onto “plan N”. But what is this plan N, as we call it in the fictitious dialog between Andromeda’s authors and distributors?
NSIS-powered Andromeda dropper
NSIS stands for NullSoft Installation System, which is one of the most popular open source platforms to build setup applications. It has been used by other malware authors in the past, but the way Andromeda’s creators are leveraging it now is slightly different.
Recently, a new source URL related to Andromeda appeared in our statistics:
hxxp://bjind.com/js/lib/suivi-colisnr345efr.zip
The target is a simple ZIP archive with just one executable binary inside. The binary was created with NSIS. We were able to easily unpack the NSIS binary to look at what’s actually inside of it.
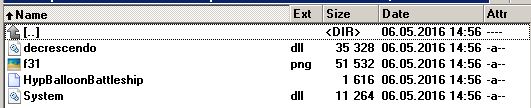
We can see two libraries, one image and one unknown file type. If we take a closer look, we can spot the true character of these files. System.dll is not interesting for us, but f31.png, is actually not an image, it is a block of encrypted binary data. You may be asking yourself, how is this supposed to work? There’s no executable file (.exe). We dug deeper into the installation script. And here we go:
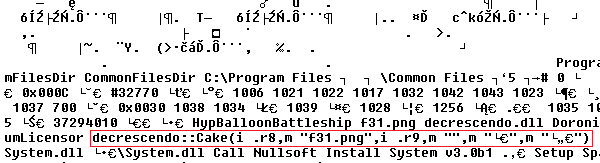
Now it’s evident. The decrescendo.dll library contains an exported function (called Cake) to decrypt f31.png and guess what – the result is the Andromeda payload loader, which we describe in our previous analysis. So, this was another attempt by Andromeda’s authors to evade our monitoring of Andromeda’s activity. However, we were able to put other pieces of the Andromeda ecosystem together to provide a clearer picture of what is going on.
A few days later, we saw Andromeda being distributed in a similar fashion through another URL:
hxxp://beton-cire-expert.nl/js/lib/suivi-colisfr6755.zip
There’s no significant difference between the principle described above and this case, just the distribution URL has been changed.
We are in the process of preparing a post about Andromeda’s plugins to cover all aspects of their updating mechanism or some very interesting fileless persistence tricks.
Stay tuned!
SHA256:
1152D9899196FFE7EAF1FFBB459925A987DE0623AF08D60EEF551664D70ED563
E9A96AB850F70275FED821E166AE9889AB98D024A95C1F51505D02F5D7C96A87
Source:https://blog.avast.com

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.










