Exploit kit’s inner workings exposed as researchers help shut down its servers. Security researchers at Cisco Talos and Check Point have published reports detailing the inner workings of Nuclear, an “exploit kit” Web service that deployed malware onto victims’ computers through malicious websites. While a significant percentage of Nuclear’s infrastructure has been recently disrupted, the exploit kit is still operating—and looks to be a major contributor to the current crypto-ransomware epidemic.
Introduced in 2010, Nuclear has been used to target millions of victims worldwide, giving attackers the ability to tailor their attacks to specific locations and computer configurations. Though not as widely used as the well-known Angler exploit kit, it has been responsible for dropping Locky and other crypto-ransomware onto more than 140,000 computers in more than 200 countries, according to statistics collected by Check Point (PDF). The Locky campaign appeared to be placing the greatest demand on the Nuclear pay-to-exploit service.
Much of Talos’ data on Nuclear comes from tracking down the source of its traffic—a cluster of “10 to 15” IP addresses that were responsible for “practically all” of the exploit infrastructure. Those addresses were being hosted by a single cloud hosting provider—DigitalOcean. The hosting company’s security team confirmed the findings to Talos and took down the servers—sharing what was on them with security researchers.
At the same time, Check Point researchers had gained access to the paid malware delivery service’s customer control panel and were able to plumb the service to collect their own statistics about its use.
Clipping coupons for infrastructure
Remarkably, after getting shut down initially, the operators of Nuclear quickly set up new DigitalOcean instances of the servers, using a different free e-mail account, according to a blog post by Cisco Talos’ Nick Biasini. While Angler exploit kit servers have been usually tied to hosting accounts at various providers created with stolen credit card numbers, Nuclear’s operators stuck to DigitalOcean because they were using coupon codes “to avoid traditional payment,” Biasini noted, “and they remained careful by only registering a single host.”
From a user-experience point of view—a criminal user, not the victim receiving the malware—Nuclear’s Web console has a look and feel similar to that of any commercial hosting service’s Web console, with bilingual support (English and Russian) and fairly intuitive tabbed forms. All a customer really needed to do was configure some filters and just add their preferred malware package for delivery. The console pages are served up on non-standard Internet Protocol ports—only a few elements of the service were seen using ports usually associated with Web traffic—likely to prevent the pages from being picked up by Web search robots.
Nuclear has a sophisticated multi-tier server architecture, with a single master server providing automatic updates to “console” servers—the systems used by paying customers to access and customize their particular paid attack packages. Those console servers in turn manage a rotating stock of landing pages served up through malicious links, exploited web pages and malicious advertisements.
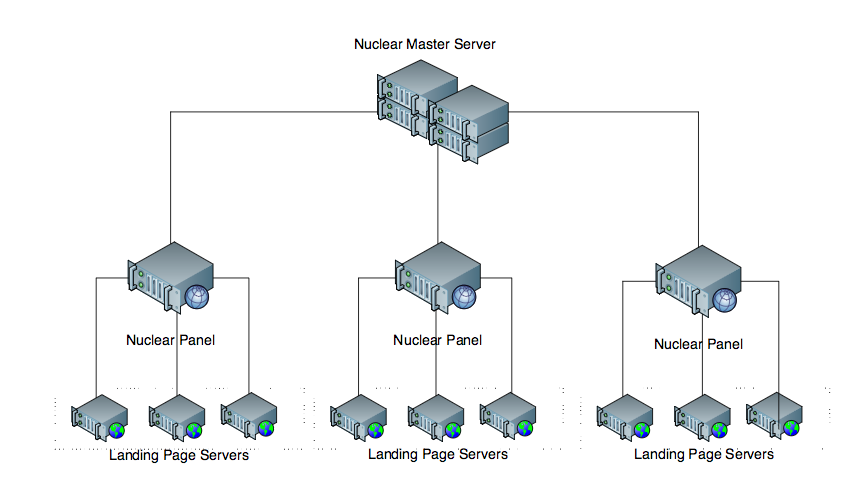
The console servers continuously check for software updates and content from the master server. In its most recent incarnation, Nuclear offers a collection of recent Flash exploits (including one posted this month), as well as a JavaScript exploit that targets Internet Explorer 10 and 11, and a VBScript that targets a two-year-old Windows Object Linking and Embedding vulnerability. Not a surprise: more than half of the systems that Check Point found had been successfully exploited were using Internet Explorer 8. The OLE exploit attacks are probably tied to phishing attacks.
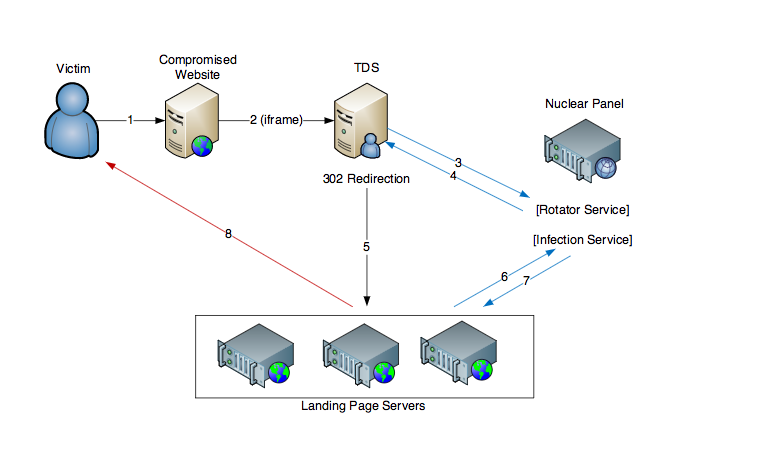
Attack types are set up as “threads” that can be tailored to different types of victims—including filters based on the location, browser type, operating system, and referrer page associated with each target that hits the landing pages controlled by the console. Each “thread” can use a different exploit or deliver a different malware package. Or it can do nothing if the target is not in the intended audience of the malware campaign.
Nuclear tries to disguise its landing pages from filtering software looking for exploit site signatures, shifting the patterns of the URLs it uses. The service once tried to disguise its URLs as content from phpBB and vBulletin Web discussion boards and Joomla content management servers, according to Check Point researchers. But now it performs a complex set of steps to randomly generate URLs to further avoid a specific pattern being associated with its landing pages. The URLs, if viewed by a human, should be obviously fishy, however, as they look something like this sample provided by Check Point:
https://(servername)/627g3g6if04s-92872/0f222441g584-23136/collaboration-polonaises.shtml?hateful=z69540vjag9e&gauze=heifers
The Nuclear landing pages themselves filter the type of browser based on the “user agent” fields in requests from systems to avoid tipping their hand—or sending an exploit to a system they can’t infect. The server searches the header data in the request looking for information suggesting that the request came from a game platform (Xbox, Playstation, Nintendo), a nonstandard browser or Web crawler (SeaMonkey, LSSRocketCrawler, CPython, Crawler, Mail.ru’s MRSPUTNIK crawler), or a security service (masscan, fMcAfee, etc).
Given that most of the victims of Nuclear were using IE 8 and were non-English speakers, the gibberish URLs may not have been recognizable, or for that matter, ever seen at all, since they were usually carried within advertisement IFRAME elements on the sites they were delivered from. And that advertising was of a very specific type.
Malware en la pornografía
 A censored pornography webcam ad used as part of the Nuclear campaign tracked by Cisco Talos.
Cisco Talos
A censored pornography webcam ad used as part of the Nuclear campaign tracked by Cisco Talos.
Cisco Talos
While the interface for Nuclear’s control panel—which sets up workflows for the delivery of malware to targets—is in English and Russian, the most popular targets for the exploit kit were Spanish speakers. About 28 percent of the content served up to targets was in Spanish, and about 20 percent of the devices that interacted with Nuclear had Spanish IP addresses. And the vast majority of the traffic that hit Nuclear’s exploit pages were redirected there by malicious advertisements—one Spanish-language ad for webcams pushed over 25,000 distinct visiting IP addresses to Nuclear in just one day, Talos found.
Just one server analyzed by Talos “showed approximately 60,000 unique IP’s [per day] connecting to this particular server,” Biasini wrote. “This amount of activity far exceeds what we were expecting based on previous data analysis.” Surprised at how so much traffic could get through websites without being noticed, Talos found the Spanish sex webcam ad was hosted on a single porn site—and accounted for nearly half the traffic to that server’s landing pages.
The elimination of the DigitalOcean infrastructure may change some of the tactics of Nuclear’s operator, but the exploit kit is probably not going away. Cisco has added Snort intrusion detection rules to help try to catch Nuclear exploit attacks, and Check Point has added detection for Nuclear exploit landing pages and the exploits themselves.
Source:https://arstechnica.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.










