Researchers at Fox-IT warn that the website of security certification provider EC Council has been compromised to host the malicious Angler Exploit Kit.
No one is secure, we are all potential targets, even if you are a skilled expert and the fact that I’m going to tell you demonstrates it. The website of security certification provider EC-Council, that organization that offers the Certified Ethical Hacker program, has been hacked and used to spread the Angler exploit kit.
According to the security researchers at Fox-IT, the official website of the EC-Council was compromised by hackers, this means that for several days visitors with vulnerable systems were open to malware infections.
The Angler EK used in the attack is serving the TeslaCrypt ransomware, the website is redirecting visitors to the Angler EK since Monday, March 21.
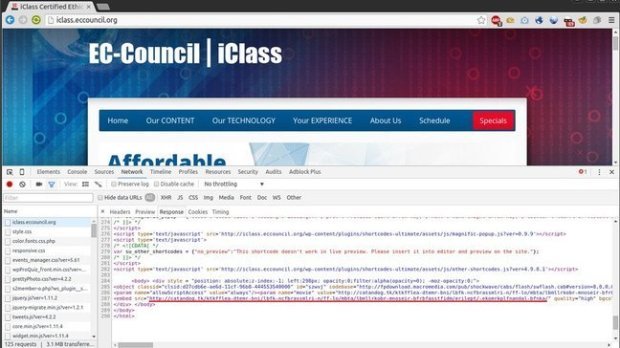
“Since Monday the 21st of March the Fox-IT Security Operations Center (SOC) has been observing malicious redirects towards the Angler exploit kit coming from the security certification provider known as the EC-COUNCIL. As of writing this blog article on the Thursday the 24th of March the redirect is still present on the EC-COUNCIL iClass website for CEH certification located at iclass[dot]eccouncil[dot]org. We have reached out and notified the EC-COUNCIL but no corrective action has been taken yet.” explains the Fox-IT senior threat intelligence analyst Yonathan Klijnsma.
The experts reported the issue to the EC Council, but they also added that the organization “didn’t seem to care.”
Recently the security researcher Kafeine confirmed that the authors of the Angler EK have integrated the exploit for a recently patched Microsoft Silverlight vulnerability.
The popular exploit kit is used by criminal organizations to exploit vulnerabilities in popular software such as Internet Explorer, Adobe Flash and Java.
In the specific case of the EC Council website, visitors with un-patched Internet Explorer browser are at risk. The redirect of visitors is performed only if the visitors use Internet Explorer, if they come from a search engine, and if their IP address is not blacklisted or belongs to a blocked geolocation.
Let me include the Indicators of Compromise (IOCs) for the specific campaign provided by Fox-IT
Bedep C&C servers:
- 89.163.240.118 / kjnoa9sdi3mrlsdnfi[.]com
- 85.25.41.95 / moregoodstafsforus[.]com
- 89.163.241.90 / jimmymorisonguitars[.]com
- 162.244.32.121 / bookersmartest[.]xyz
TeslaCrypt C&C servers:
- 50.87.127.96 / mkis[.]org
- 213.186.33.104 / tradinbow[.]com
Source:https://securityaffairs.co/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.