Today I’m going to tell you about a couple of techniques used to build stealth backdoors. Then, I will also show you how to detect that kind of malware and keep your systems safe. But first, a brief introduction.
I started looking into this after reading a quite sensationalist article about a Linux backdoor. The article basically said that such a backdoor was undetectable and that it can be installed almost everywhere without being noticed by users. The paper was talking about the Turla Trojan which is based on the cd00r PoC port knocking backdoor.
How Does It Work?
I haven’t manage to get the Turla source code so we are going to use the publicly available cd00r backdoor. Before diving into the code, let’s first quickly take a look to how does it work.
This backdoor uses the technique known as Port Knocking. This technique consists on detecting a specific sequence of connection attempts to different ports. If the sequence is correct, the firewall rules are changes enabling access to a specific service.
The cd00r backdoor makes use of this technique to enable a telnet service on the victim’s machine using the inetd superdaemon.
How Is It Implemented?
cd00r is implemented as a sniffer that captures traffic on the target machine. The sniffer captures the packets and looks for TCP SYN packets with a target port that matches a pre-defined sequence. The cd00r backdoor uses libpcap to capture those packets.
All the code to setup the sniffer is in the main function. I will give you some hints on how to go through it. The rest of the code is standard C and does not really need much explanation. Anyhow, do not hesitate to comment below if you need some help.
A Libpcap Sniffer
So, let’s see how does a libpcap sniffer looks like. The cd00r code is quite verbose, so I will use a modified version here for the sake of simplicity. Whenever you have grasp the basic idea, jump into the main function of cd00r to see some more complete code.
A minimal libpcap sniffer requires roughly 5 function calls (and a bunch of variables). Something like this:
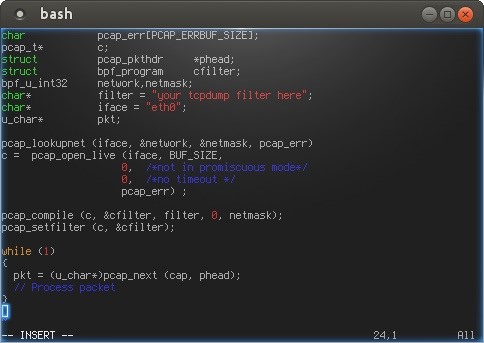
Yep, finally I uploaded code as a image… I will burn in the bandwidth hell forever….
That’s basically it… a mini tcpdump.
In the main loop (the stuff inside the while block), the application gets the packets matching the specified filter calling the pcap_next function. Then the packet is processed and the process starts again.
If you look at cd00r.c from line 449 and on, you will see how the different headers (Ethernet and IP) are skipped to get to the TCP packet. Then, after some checks (basically ensuring that it is a valid SYN packet) the port is compared against the pre-defined list.
When all the ports are “knocked” (in the right order), the cdr_open_doorfunction is executed. This function just brings up a telnet server using inetd, effectively enabling remote access to the victim’s machine.
A Stealth BackDoor
A backdoor like cd00r is practically invisible most of the time. Tools like netstat or even tcpdump will not see any kind of activity at all. There is no port open. There is no connection going on.
Then, when the right sequence of packets is received, telnet server will be easily visible as well as any connection from outside. But doing short connections will difficult the detection.
That is pretty scary. Well, actually, it is not. This kind of backdoors can be detected very easily if you know where to look at.
In the previous section, I had shown you how to write a sniffer using libpcap. But, under the hood, libpcap actually creates a RAW socket that can be seen with a line like this:
sudo lsof | grep RAW
If you just run this line on your computer right now, you may see somedhclient instances or nothing. Any sniffer on your system will be easily detected that way (as far as no rootkit is installed). Fire your preferred sniffer (tcpdump, wireshark, …), start capturing traffic and re-run lsofagain…
Even More Stealth
The cd00r was a proof of concept exercise and it is not really intended to be a real threat. Whenever the telnet service is started it will be easily noticeable, and usually the firewall will prevent connection from outside. In order to stay stealth, the data has to be transmitted using a less obvious protocols. For instance: ICMP.
You can find an example of a ICMP reverse shell implementation here. This one uses low-level RAW sockets instead of libpcap, but the overall principle is the same. It also provides an alternative popen implementation that might be of interest for somebody here.
The remote part of the system sniffs ICMP packets. When a special ICMP packet is captured, the data contained in the packet is considered a command and it is executed. The result of the execution is sent back in another ICMP packet to the attacker’s machine.
ICMP sits besides IP in the TCP/IP stack and, therefore, it is not at transport level. That means that there is no port associated to a ICMP packet. So no open port to monitor or detect.
However, as it happens with cd00r, the RAW socket will be there and will be detectable. Also the unusual ICMP traffic will probably be noticed by the experienced administrator.
Conclusions
If you have get this far and followed the different references on this post you may know by now, how to write your own sniffer and how to deploy close to undetectable network applications. You may have also learned that it is nearly impossible (without rootkitting the system) to deploy a completely undetectable application. There is always something left behind…
Source:https://null-byte.wonderhowto.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.










