New malvertising campaign may have exposed tens of thousands in the past 24 hours. Mainstream websites, including those published by The New York Times, the BBC, MSN, and AOL, are falling victim to a new rash of malicious ads that attempt to surreptitiously install crypto ransomware and other malware on the computers of unsuspecting visitors, security firms warned.
The tainted ads may have exposed tens of thousands of people over the past 24 hours alone, according to a blog post published Monday by Trend Micro. The new campaign started last week when “Angler,” a toolkit that sells exploits for Adobe Flash, Microsoft Silverlight, and other widely used Internet software, started pushing laced banner ads through a compromised ad network.
According to a separate blog post from Trustwave’s SpiderLabs group, one JSON-based file being served in the ads has more than 12,000 lines of heavily obfuscated code. When researchers deciphered the code, they discovered it enumerated a long list of security products and tools it avoided in an attempt to remain undetected.
“If the code doesn’t find any of these programs, it continues with the flow and appends an iframe to the body of the html that leads to Angler EK [exploit kit] landing page,” SpiderLabs researchers Daniel Chechik, Simon Kenin, and Rami Kogan wrote. “Upon successful exploitation, Angler infects the poor victim with both the Bedep trojan and the TeslaCrypt ransomware–double the trouble.”
Update: According to a just-published post from Malwarebytes, a flurry of malvertising appeared over the weekend, almost out of the blue. It hit some of the biggest publishers in the business, including msn.com, nytimes.com, bbc.com, aol.com, my.xfinity.com, nfl.com, realtor.com, theweathernetwork.com, thehill.com, and newsweek.com. Affected networks included those owned by Google, AppNexis, AOL, and Rubicon. The attacks are flowing from two suspicious domains, including trackmytraffic,biz and talk915[.]pw.
The ads are also spreading on sites including answers.com, zerohedge.com, and infolinks.com, according to SpiderLabs. Legitimate mainstream sites receive the malware from domain names that are associated with compromised ad networks. The most widely seen domain name in the current campaign is brentsmedia[.]com. Whois records show it was owned by an online marketer until January 1, when the address expired. It was snapped up by its current owner on March 6, a day before the malicious ad onslaught started.
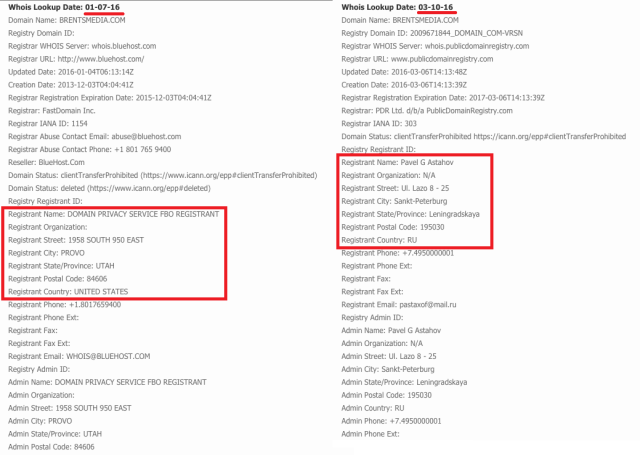
Other domain names being used in the current campaign include evangmedia[.]com and shangjiamedia[.]com. The SpiderLabs researchers speculate the people pushing the bad ads are on the lookout for expired domains containing the word “media” to capitalize on the reputation they may enjoy as a legitimate address.
The campaign underscores the vital role that smart browsing plays in staying secure online. One of the most important things users can do is to decrease what researchers refer to as their “attack surface.” That means uninstalling things like Adobe Flash, Oracle Java, Microsoft Silverlight, and other third-party browser extensions unless absolutely required. The other crucial ingredient in safe browsing is installing updates as soon as they become available and using the 64-bit version of Chrome for browsing when possible. Windows users would also do well to install Windows 10 and use Microsoft’s Enhanced Mitigation Experience Toolkit.
The posts didn’t elaborate on the crypto ransomware being spread in the campaigns, except for the mention by SpiderLabs that it included TeslaCrypt, which so far is known to infect only Windows computers. With last week’s discovery of Mac-based ransomware, users of all computing platforms should take the threat seriously.
Source:https://arstechnica.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











