What’s driving the surge in hidden services—is it government tampering? In recent weeks, the number of “hidden services”—usually Web servers and other Internet services accessible by a “.onion” address on the Tor anonymizing network—has risen dramatically. After experiencing an earlier spike in February, the number of hidden services tracked by Tor spiked to 114,000 onion addresses on March 1. They then dropped just as quickly, falling to just below 70,000 hidden services seen by Tor on Thursday—still twice the number that Tor had held steady at for most of 2015.
“We don’t know what’s causing this,” said Kate Krauss, the director of communications and public policy for the Tor Project. “But it’s not difficult for even one person—a researcher, for instance—to create a lot of new onion addresses—which is not the same as actual websites or services. In fact, we want the process of creating onion addresses to be as easy as possible to encourage the creation of more onion services. These spikes are typically temporary—and as you see from the chart, this one is already going away.”
Still, there has never been this sort of wild gyration in the number of addresses in recent times—or at least as far back as the Tor Project has kept metric data. So what caused the sudden near-tripling of the size of Tor’s hidden Web and its rapid contraction? Based on a deeper look at Tor’s metrics and discussions with both Tor developers and security experts, the huge spike in the “size” of the hidden Web within Tor was likely caused by a perfect storm of coincidences: major Internet censorship events in at least two countries, the relatively rapid adoption of a new messaging tool, a malware explosion, and ongoing attempts to undermine the privacy of the network.
Tor’s hidden Web
Hidden service addresses are 16-character “names” that are generated automatically when the service is created based on cryptographic key pairs. It’s possible to create “vanity” onion addresses by basically throwing computing power at the key creation process until it hashes an address that is human-readable. For example, Facebook’s Tor-facing hidden service address is https://facebookcorewwwi.onion/. Multiple onion addresses can be hosted on the same server, so there isn’t a one-to-one relationship between the number of onion addresses and the number of servers connected to Tor.
Most Tor users never create a hidden service of their own. They generally use Tor for anonymous access to sites on the open Internet or to access hidden sites provided by others. However, the fluctuation in the number of onion addresses may partially be due to the adoption of Ricochet, a Tor-based messaging application. The latest version of Ricochet posted on February 15, just as the first bump in hidden services began.
To function, Ricochet creates a hidden service on the user’s computer. It doesn’t create an onion address, but it does create its own hidden service identifier to allow clients to find each other across Tor. The service periodically connects to those of the user’s contacts to determine if the user is online and to send messages.
“Ricochet users are included in the ‘onions seen’ metric,” Ricochet maintainer John Brooks told Ars in an e-mail. Because of the distributed nature of Ricochet—it uses no centralized server—Brooks said he had no real figures on how many users the software had. “I would be surprised if these changes were related to Ricochet,” he added, “but it certainly could be a contributor.”
While it may have added to the growth, it’s unlikely that Ricochet was responsible on its own for the massive spike in hidden services from February 26 to March 1; the amount of hidden services traffic over that period doesn’t reflect a surge in Ricochet use or in any hidden services, for that matter.
Censorship events and other things
Elections in Uganda and Iran, and accompanying Internet censorship by the governments of both countries, roughly matched the period of growth in hidden services. Tor traffic out of Uganda spiked in mid-February as a result of the government blocking social media sites, and Tor traffic using bridges from Iran rose dramaticallyduring elections there last week—though it had been on the rise for much of the last three months.
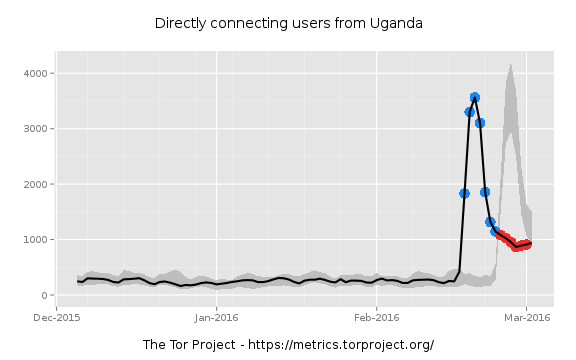
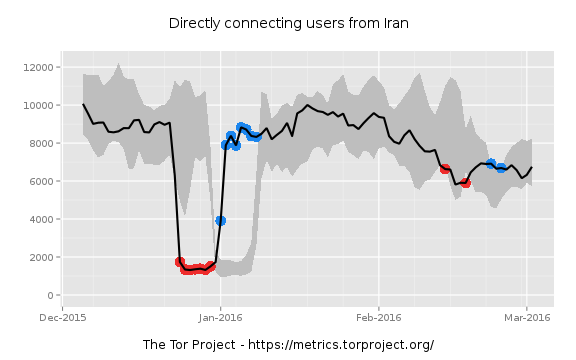
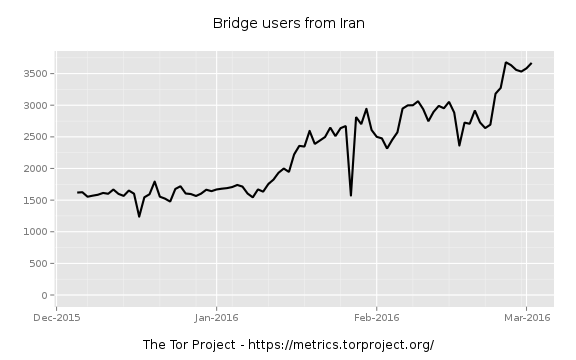
However, the rise in bridge traffic in Iran corresponds to a drop in direct traffic to Tor from that country, as Iran apparently moved to block direct Tor connections. And even if all of those users—3,000 at the peak in Uganda, and 3,500 at the peak a week later in Iran—created hidden services, that wouldn’t alone account for the surge.
Also, the Tor network’s statistics show no accompanying spike in traffic to hidden services. So it seems there was something creating a massive number of new services with little traffic associated with the results.
That suggests some likely reasons for the weeklong surge in new onion sites spotted by Tor’s directory: some sort of bot or “darknet” service creating new sites or an effort to break Tor’s relays by overwhelming them with new directory data.
Remember that a single server can have multiple onion addresses associated with it, pointing to different webpages or other applications. And there are a number of underground services used by criminals that generate onion pages. Tor has been a favorite command-and-control platform for cryptographic ransomware such as CryptoWall.
Many ransomware variants have used Tor sites to transfer the private keys used to encrypt the files of victims and to collect payments, and some ransomware tools are offered as a subscription service to would-be criminals, automatically generating onion addresses associated with each “customer.” And there have been other episodes of malware generating spikes in hidden services—but not to this degree.
Of course, the spike also drove rampant speculation that it was an attempt by a government agency to somehow compromise Tor’s hidden services or to knock Tor relays (the servers that route Tor traffic through the anonymizing network) offline. A spike in hidden services might have been intended to fill the memory allocated for tracking them on Tor relays, causing them to crash.
One Tor relay operator reported on Reddit, “I run a Tor relay, which has the HSDir flag, and my relay crashed a few times while someone was publishing a large amount of hidden service descriptors. Has anyone else had problems like this? If someone found a vulnerability in how published hidden service descriptors are handled, someone might be trying to mass exploit every Tor relay with the HSDir [hidden services directory] flag.”
Some other relay operators reported similar issues, and there was a drop in the number of relays running the hidden services directory. “It’s not a botnet,” another poster on the “onions” subreddit posted. “I think we’ll be reading about more hidden server raids in a few months.”
Source:https://arstechnica.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











