Attackers exploit eBay’s lackluster security policy. The JSF*** XSS bug that cyber-security firm Check Point discovered two weeks ago is being used in real world attacks on the eBay platform, in spite of eBay’s best efforts at having it neutralized.
JSF*** is an educational project started a few years back by Martin Kleppe, who managed to narrow down most of the JavaScript syntax to a combination of six characters: [, ], (, ), ! and +.
Check Point security researchers discovered that when creating an eBay store, an attacker could hide his malicious code by converting the regular JavaScript syntax into the one used by JSF***, and then insert it in the product description field.
JSF*** XSS bugs are hard to detect and block
Because of JSF***’s non-standard character set, this cloaked code passed through eBay’s XSS filters and got stored in the product’s description. Whenever users would access a product page that had the malicious code hidden in its description, the code would execute in his browser, right on the eBay store.
Since the attack was launched on eBay’s main domain, and most users would have probably arrived there from search results or by clicking on actual eBay.com links, most of them would have had their guard down, and would be susceptible to phishing attacks.
eBay’s patch was insufficient
While in the beginning eBay refused to fix the issue, a few days later the company caved in to pressure from the infosec community and implemented a partial fix.
According to security and monitoring firm Netcraft, this partial fix was not effective, and they’ve observed real world instances where the JSF*** attack was used against eBay store visitors.
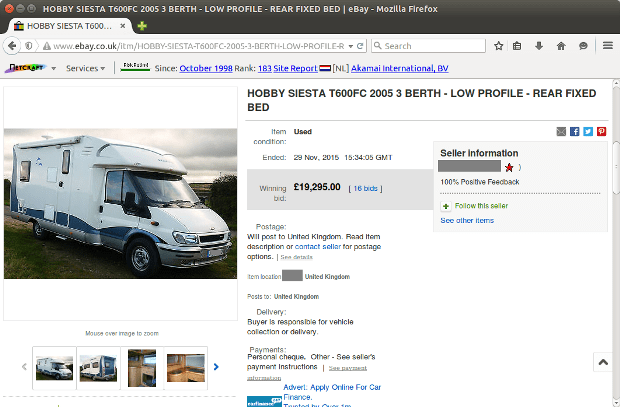
Netcraft says that most of the hackers are using compromised users accounts to create malicious product listing, mostly for vehicles. All these accounts belong to old eBay users, making the attack even harder to detect since these users have legitimate activities associated with their profile.
Curiously, the crooks employing JSF*** aren’t stealing eBay passwords
“Not only is it rather cleverly launched from the legitimate eBay site, and uses randomly-named files that are deleted to evade detection, but it also tries to avoid leaving any evidence in eBay’s server logs,” Netcraft researchers noted about this most recent campaign that employs JSF***.
Additionally, this phishing campaign only steals the user’s email address, and not his password. This is because the crooks are using the user’s interest in the eBay product (usually a car) and his address to send the user an email containing a payment link through an escrow service.
The service is an obvious sham, and if the customer falls for the message and initiates a payment, the crooks will keep all the money, defrauding the eBay user.
Source:https://news.softpedia.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.