Lenovo Security Advisory: LEN-4058
Potential Impact: Remote browsing of file system, unauthorized access of transferred files and denial of service attack that could crash the Windows SHAREit client
Severity: Medium
Summary:
A second vulnerability on both Windows and Android versions could allow an attacker who is actively intercepting traffic between two users transferring a file to copy or modify content being transferred when the file transfer is occurring.
Windows SHAREit version 3.2.0 and later and Android SHAREit version 3.5.38_ww and later include a new “secure mode” option that resolves the first vulnerability by allowing users to configure a unique password to share files between users, which will prevent unauthorized users from connecting to the SHAREit hotspot. This mode also fixes the second vulnerability by encrypting the file transfer using AES-256 (using the unique password as a pre-shared key) on a PC to PC LAN transfer and through a hotspot WPA connection on transfers involving the Android version
Third and fourth vulnerabilities were identified only on SHAREit for Windows. The third vulnerability could allow an attacker who is within physical Wi-Fi range or connected on the same local LAN to remotely view names of files in the file system that are accessible to the user running SHAREit, subject to normal Windows file access permission restrictions. The fourth vulnerability could cause a denial of service attack and crash the Windows SHAREit client. These vulnerabilities do not allow an attacker to download or otherwise access the visible files. These vulnerabilities are fixed in all modes of SHAREit for Windows version 3.2.0 and later.
Mitigation Strategy for Customers (what you should do to protect yourself):
The following two steps will address all disclosed vulnerabilities.
2. Ensure you are using “secure mode” by following the instructions below.
There are three ways to update to the latest Windows version, as described here:
1. Updating through the SHAREit app
Users should open SHAREit on their PCs and they will be presented with a prompt to automatically update SHAREit to the latest version.
2. Updating via the Lenovo System Update utility or the Lenovo OneKey Optimizer Utility
In Lenovo System Update, click on “Get new updates” and follow the prompts to update your system with the latest version of SHAREit.
In Lenovo OneKey Optimizer, click on “Update” and follow the prompts to update your system with the latest version of SHAREit.
3. Updating via direct download
Identify the version of SHAREit installed on your system and click on the download link from the following website. Click on the “Free Download” link at the top and then click on “Download for Windows” and open the executable:https://shareit.lenovo.com
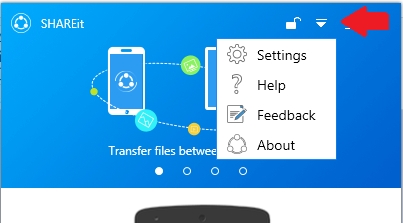
1. Click on the down arrow on the SHAREit screen and select “Settings”
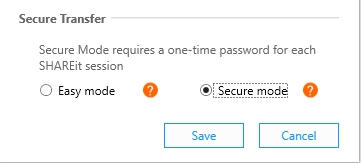
2. Click on the “Secure mode” option and then click on “Save”.
There are two ways to update to the latest Android version as described here:
1. Updating via the SHAREit app
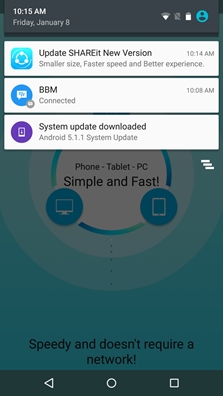
When the SHAREit app is opened, the user will see a SHAREit notification in the notification bar.
Drag down the notification bar and tap on the “Update SHAREit” notification. The user will be redirected to the Google Play store to update the application to the latest version.
The link redirects you to open Google Play store to update the application.
2. Updating via the Google Play store
Go to the Google Play store and download the latest version of SHAREit available here: https://play.google.com/store/apps/details?id=com.lenovo.anyshare.gps&hl=en
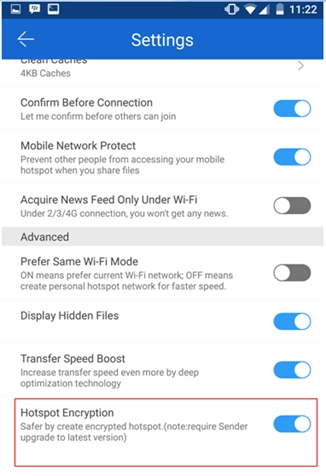
To enable “secure mode” on SHAREit for Android running version 3.5.38_ww and above – PLEASE NOTE, “secure mode” on SHAREit for Android only allows connection through a Wi-Fi hotspot and does not function through a LAN
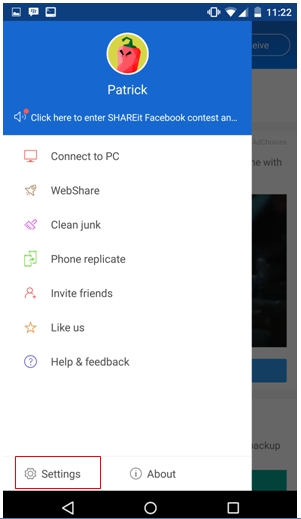
1. Tap on the user icon in the upper left corner
2. Tap on the “Settings” button toward the bottom of the screen
3. Scroll down and select “Hotspot Encryption”
Acknowledgements:
This vulnerability was discovered and researched by Ivan Huertas from Core Security Consulting Team.
(CVE-2016-1492, CVE-2016-1491, CVE-2016-1490, CVE-2016-1489).
Also thanks to Peter Nelson, independent security researcher.
Other information and references:
CVE ID: CVE-2016-1492, CVE-2016-1491, CVE-2016-1490, CVE-2016-1489

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.