Highly privileged account could be used to hack customers’ networks, researchers warn.
A company that supplies audio-visual and building control equipment to the US Army, the White House, and other security-conscious organizations built a deliberately concealed backdoor into dozens of its products that could possibly be used to hack or spy on users, security researchers said.
Members of Austria-based security firm SEC Consult said they discovered the backdoor after analyzing the AMX NX-1200, a programmable device used to control AV and building systems. The researchers first became suspicious after encountering a function called “setUpSubtleUserAccount” that added an highly privileged account with a hard-coded password to the list of users authorized to log in. Unlike most other accounts, this one had the ability to capture data packets flowing between the device and the network it’s connected to.
“Someone with knowledge of the backdoor could completely reconfigure and take over the device and due to the highest privileges also start sniffing attacks within the network segment,” SEC Consult researcher Johannes Greil told Ars. “We did not see any personal data on the device itself, besides other user accounts which could be cracked for further attacks.”
The tell-tale function not only equips the account with packet-sniffing capabilities, it also contains code that prevents it from displaying when a list of valid usernames is enumerated. To log in to the account, an attacker would likely need access to the local network the device was connected to, although queries using the Shodan search engine showed some vulnerable devices are accessible from the Internet. SEC Consult researchers eventually found the same SetUpSubtleUserAccount function in more than two-dozen other AMX devices. The equipment is used by a long list of security-conscious organizations, according to this page on the AMX website.
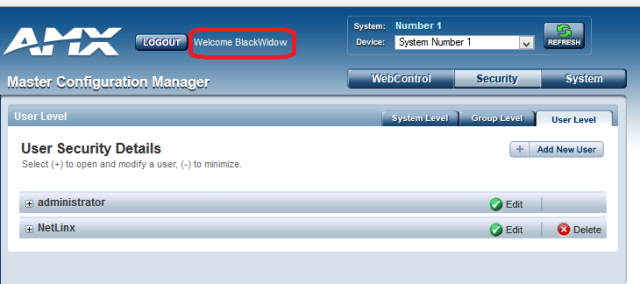
BlackWidow and Batman
When SEC Consult informed AMX officials of the backdoor last March, the equipment maker responded seven months later with an update that it claimed fixed the problem. In fact, according to SEC Consult, the update merely changed the username assigned to the backdoor from BlackWidow to 1MB@tMaN. The backdoor account and the capabilities built into it remained. SEC Consult informed AMX of the continued threat and after receiving no response, the organization eventually decided to schedule disclosure of the finding for this week.
Last week, AMX released a new update without notifying SEC Consult of it. SEC Consult researchers have yet to confirm that it closes the backdoor. AMX officials didn’t respond to questions and a request for comment Ars sent as this post was being prepared.
As problematic as the existence of the backdoor account is, the reported response from AMX is even more concerning. It’s unclear why the initial update swapped one comics character for another as a username rather than removing the account altogether. Until researchers have time to confirm that the new update fully resolves the problem, SEC Consult recommends that people stop using vulnerable devices.
Update Jan 21, 2016 4:29 PST: An AMX representative has issued the following statement:
First, “Black widow” was an internal name for a legacy diagnostic and maintenance login for customer support of technical issues. Commonly used in legacy systems, it was not “hidden” as suggested, nor did it provide access to customer information. While such a login is useful for diagnostics and maintenance, during our routine security review in the summer of 2015, we determined that it would be prudent to eliminate this feature as part of a comprehensive software update. We informed our customers and the update was deployed in December 2015.
“1MB@tMaN” was an entirely different internal feature that allowed internal system devices to communicate. It was not an external login nor was it accessible from outside of the product. The “1MB@tMaN” internal system device capability also was not related to nor a replacement for the “Black Widow” diagnostic login. The only connection was the fact that our software update that eliminated “Black Widow” also provided an update to the “1MB@tMaN” internal capability that eliminated this name.
In terms of the names, these were light hearted internal project names that our programmers used with no intended meaning.
We take security very seriously and are continuously testing our own systems and capabilities and developing more sophisticated updates.
Source:https://arstechnica.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











