For a little over a month, researchers and previous victims have been quietly helping TeslaCrypt victims get their files back using a flaw in the TeslaCrypt’s encryption key storage algorithm. The information that the ransomware could be decrypted was being kept quiet so that that the malware developer would not learn about it and fix the flaw. Since the recently released TeslaCrypt 3.0 has fixed this flaw, we have decided to publish the information on how a victim could generate the decryption key for encrypted TeslaCrypt files that have the extensions .ECC, .EZZ, .EXX, .XYZ,.ZZZ, .AAA, .ABC, .CCC, and .VVV. Unfortunately, it is currently not possible to decrypt the newer versions of TeslaCrypt that utilize the .TTT, .XXX, and .MICRO extensions.
The Flaw in TeslaCrypt
TeslaCrypt’s flaw was not in the encryption algorithm itself, but rather how the encryption keys were being stored on a victim’s computer. When TeslaCrypt encrypts a victim’s files it uses the AES encryption algorithm, which uses the same key to encrypt and decrypt a file. Each time TeslaCrypt was restarted, a new AES key was generated and stored in the files that were encrypted during this session. This means that some files on a victim’s machine could be encrypted with a different key than other files. Since the developers wanted to store these encryption keys in every encrypted file, they needed a way to secure it so a victim wouldn’t simply extract their key and decrypt their files. To protect this key, the developers first used another algorithm to encrypt this key and then stored information about this encrypted key in each encrypted file. The information stored in each encrypted file is shown in the image below.
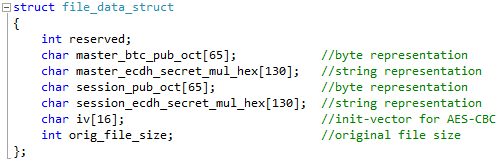
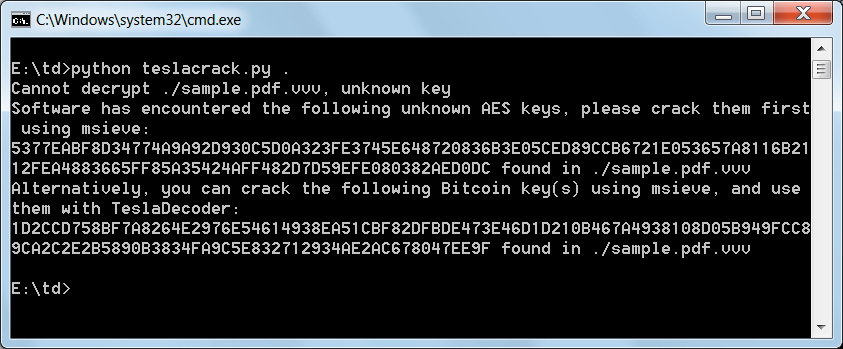
Unfortunately, for the malware developer, the size of this stored key were not sufficiently strong enough to withstand the computing power of today’s modern computers. Thus it was possible to use specialized programs to factorize these large numbers in order to retrieve their prime numbers. Once the prime numbers were retrieved, specialized tools are then able to use them to reconstruct the decryption key. For some victim’s this process could take as a little as 5 minutes to complete, while others that had stronger numbers could take days. For more information on prime numbers and how they relate to cryptography, this video provides a good summary.
Volunteers to the Rescue
It all started when reports were coming in that Kaspersky was able to decrypt encrypted files without a user paying the ransom. It was decided that it was better to keep this ability private as we didn’t want to alert the developer of the flaw in his program. Soon after a member named Googulator created a post in the TeslaDecoder topic stating that he came up with a method to generate a victim’s encryption key by factoring the prime numbers of the data stored in an encrypted file. He published this method as Python scripts in a Github project calledTeslaCrack for everyone to use. This method was fantastic and though we hid it so the developer wouldn’t be notified, we allowed the method to be used in our forums and news articles. This method took off and we had volunteers, many of whom were prior TeslaCrypt victims, offering their computer’s computing power and services to help other victims retrieve their decryption keys. To assist with this we create a dedicated TeslaCrypt (.VVV, .CCC, etc Files) Decryption Support Requests topic in our forums.
Googulator’s TeslaCrack scripts was a lifesaver, but it’s ability to only decrypt certain TeslaCrypt variants and the fact that you needed to work from the command-line had made it more complicated to use. As the scripts are developed in Python, a user would need to install Python and then issue the commands via the command line. This method also required the victim to use encrypted files that had a known file header (PDF, JPG, etc) and modify the TeslaCrack scripts if you were not using the a encrypted PDF file. Last, but not least, TeslaCrack was attacking the AES key of the file, and since this key is changed each time TeslaCrypt was restarted, a user would potentially have to crack multiple keys in order to completely decrypt all of their files. Unfortunately, for many users this was a confusing process and was difficult for them to do on their own.
At the same time BloodDolly, the creator of TeslaDecoder, was updating his tools to be able to recover the encryption key as well for all variants of TeslaCrypt. His tools were designed a bit differently, though, as instead of going after the AES key of the file, it was attacking the master private key that TeslaCrypt used on the victim’s computer. This meant that once you recovered the key, you would be able to decrypt all of the files on the computer regardless of whether TeslaCrypt has been restarted. Furthermore, as his tools were developed to run in Windows and did not require specific encrypted file types, they were much easier for a general user to use. Using these tools and specialized factorization tools such as Msieve and Yafu, victims were now easily able to recover their files for free.
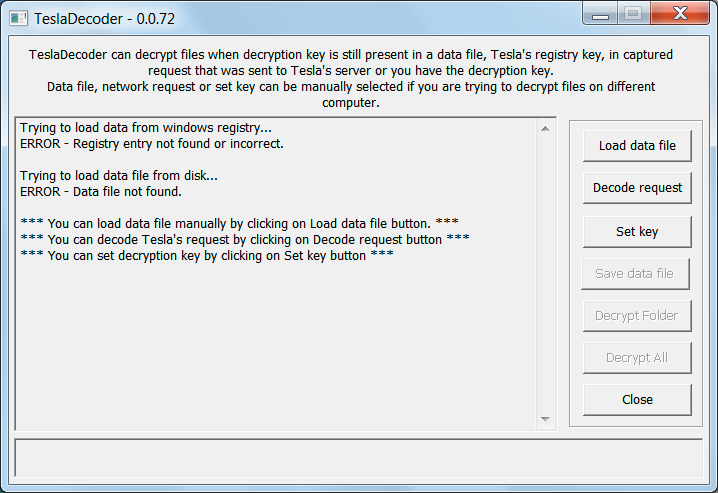
How to use TeslaDecoder to decrypt TeslaCrypt Encrypted Files that have the ECC, .EZZ, .EXX, .XYZ, .ZZZ, .AAA, .ABC,.CCC, and .VVV Extensions
If you are a victim of TeslaCrypt and your files have the ECC, .EZZ, .EXX, .XYZ, .ZZZ, .AAA, .ABC, .CCC, or .VVV extensions, you can use BloodDolly or Googulator’s scripts to retrieve your decryption key. Personally, for most users, I suggest that you use BloodDolly’s TeslaDecoder tool because it will be easier to use for those who are more comfortable in a Windows environment and makes it easier to recover the key that can decrypt all of your files..
To decrypt your files simply download TeslaDecoder and read the included instructions. I created these instructions to be very detailed and to provide all the information and tools that you will need to recover your encryption key. If you find the information confusing, please feel free to ask for help in the TeslaDecoder Support Topic.
If you do not feel comfortable performing this process on your own, you are also welcome to ask a volunteer to retrieve the key for you. To do this simply follow the instructions in the first post of the TeslaCrypt (.VVV, .CCC, etc Files) Decryption Support Requests topic and someone will get back to you with your key. Please note that the volunteers get many requests a day, so it may take some time to receive help.
Once you have recovered your key, you can then use TeslaDecoder to decrypt all of the files on your drives.
A Special Thanks to our Helpers and Volunteers
I would like to send a special thanks to those volunteers who sacrificed their precious time to help victim’s of TeslaCrypt. A very special thanks go to BloodDolly, Googulator, VirusD,Demonslay335, NightbirD, vilhavekktesla, al1963Goosea, the encryption gurus at Kaspersky, Quietman7, and the numerous other volunteers who have spent huge amounts of time helping the TeslaCrypt victims at BleepingComputer.com. Without your help there would be many people who would have lost their data.
Source:https://www.bleepingcomputer.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.










