The internet’s root servers came under a concerted distributed denial of service (DDoS) attack last week that effectively knocked three of the 13 critical pillars of the internet offline for several hours.
The attack came just days before the Janet academic network received a similar DDoS attack.
According to a first analysis of the root server attack, published by the root server operators on Tuesday, the attack occurred on November 30, 2015 between 06:50 and 09:30 UTC and then again the next day for an hour.
Many, but not all, of the root servers received roughly five million queries per second, which was enough to flood network connections and cause timeouts on the B, C, G, and H root servers. The queries were valid DNS messages for a single domain name; the second day’s attack used a different domain name than the first.
Ultimately, the operators affected by the attack used counter-measures, with some degree of success, but a proper analysis is now underway to discover exactly what form the attack took and where it originated.
Of perhaps most concern is the fact that even with the implementation of Anycast technology designed to help deal with such an attack, a number of the servers were still swamped.
The root servers themselves make up the pillars on which the internet’s domain name system sits. They act as a sort of global directory for all the other parts of the internet.
Due to the internet’s design, the servers themselves see a comparatively low amount of traffic, especially if you compare it to what companies like Google deal with. If they were all to be taken offline, it would not cause immediate problems for the wider internet, since the information they store and share is held by many thousands of other servers.
That said, any attack on the DNS’ infrastructure is taken very seriously and if the root servers went down for longer than a day, it would start causing significant problems globally.
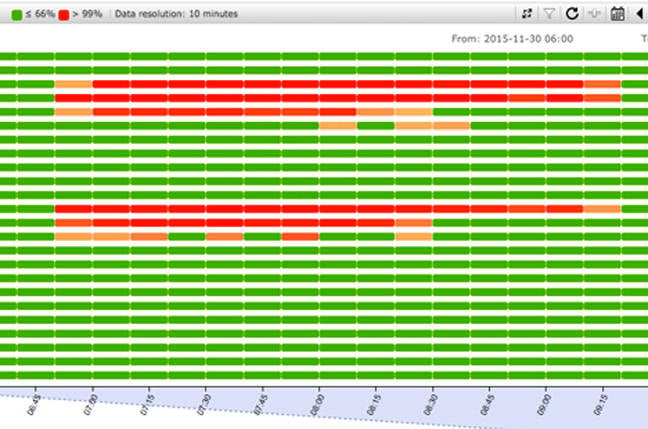 A graph by RIPE’s Atlas monitoring system shows the impact of the attack
A graph by RIPE’s Atlas monitoring system shows the impact of the attack
What’s the solution?
Root server operators have already highlighted one problem that makes such attacks possible: the failure of large numbers of ISPs to implement network ingress filtering, which limits the ability to spoof internet traffic and so carry out DDoS attacks. That said, one analysis shows that 82 per cent of the internet’s traffic is now not spoofable thanks to the broad implementation of the BCP 38 standard.
Another solution put forward by the operator of the F-root server, Paul Vixie, is to develop a liability model that would penalize network operators that allow attack traffic to flow across their networks.
“In the world of credit cards, ATM cards, and wire transfers, state and federal law explicitly points the finger of liability for fraudulent transactions toward specific actors,” Vixie wrote in a post last month.
“And in that world, those actors make whatever investments they have to make in order to protect themselves from that liability, even if they might feel that the real responsibility for preventing fraud ought to lay elsewhere.”
“We have nothing like that for DDoS. The makers of devices that become part of botnets, the operators of open servers used to reflect and amplify DDoS attacks, and the owners and operators of networks who permit source address forgery, bear none of the costs of inevitable storms of DDoS traffic that result from their malfeasance.”
Rare event
This is only the third time that the root servers have been targeted in a significant sustained attack. The most significant, back in 2007, saw a botnet containing roughly 5,000 computers swamp four root servers with traffic, taking down two of them for several hours in two waves of attacks.
In that case, although the majority of the traffic was found to have come from South Korea, it is believed the attack was controlled from the United States. The details of last week’s attack have not yet been developed.
The operators themselves in the first analysis of the attack said it was “notable for the fact that source addresses were widely and evenly distributed, while the query name was not. This incident, therefore, is different from typical DNS amplification attacks whereby DNS name servers (including the DNS root name servers) have been used as reflection points to overwhelm some third party.”
Nonetheless, they concluded that the system had stood up pretty well: “The DNS root name server system functioned as designed, demonstrating overall robustness in the face of large-scale traffic floods observed at numerous DNS root name servers.”
What’s going on?
No motives for the 2007 attack or this most recent attack have been identified.
Usually, DDoS attacks are carried out in order to extract money from companies, or to make a political point. But there is no obvious political point to be made in attacking the very foundations that the global internet relies upon. Although it is worth noting that all but two of the root servers are run by US entities and three are run by the US government.
It is also notable that the duration and timing of these most recent attacks are very similar to the one in 2007, possibly suggesting the same modus operanda, or possibly just highlighting the window of time it takes for network operators to understand and mitigate an ongoing attack.
The fact that another unlikely target in the form of the Janet network has been attacked by a similar method just days later is also suspicious, and something researchers will be digging into.
It has long been feared that nation states will start engaging in cyber warfare – the most famous example being Russia’s attack on Estonia, also back in 2007, when it effectively knocked the country offline.
Likely by some coincidence, the world’s governments will be meeting next week at the United Nations in New York to discuss the issue of internet governance. The document that will form the foundation of those talks has a whole section dedicated to security.
Part of that document notes: “Building confidence and security in ICT [information and communication technology] use should also be a priority, especially given growing abuse of ICTs for harmful activities from harassment to crime to terrorism.”
Source:https://www.theregister.co.uk/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











