Flat, firewall-free network was a walk in the park, boffins say.
Cyber Defence Summit An un-named Casino with next-to-no security has lost 150,000 credit cards after being raided by a new hacking group.
Researchers Emmanuel Jean-Georges and Barry Vengerik of Mandiant and FireEye say the “Fin5” hacking group had last year skipped through the organisation’s “flat” IT architecture to raid its open payment systems.
They say the casino lacked even basic firewalls around its payment platforms and did not have logging.
“It was a very flat network, single domain, with very limited access controls for access to payment systems,” Emmanuel Jean-Georges told the Cyber Defence Summit (formerly Mircon) in Washington DC today.
“Had this casino hotel operator had even minimal or basic protections in place like a firewall with default deny systems to limit access to PCI (payment) systems … it would have slowed down the attackers and hopefully set off red flags.”
He told The Reg his company has investigated a dozen firms hit by the credit card -pillaging attackers, and thinks there may be a further six which have been hacked.
Vengerik says the attackers have hosed at least two payment systems providers and are targeting their customers, including the casino.
The incident should serve as a warning to businesses to secure any access that third party organisations have to corporate networks, he says.
The attack group targets organisations using stolen credentials which ensures no flags are tripped on initial penetration. From there, attackers target Active Directory in a bid to unlock more credentials and gain lateral movement.
“It is classic lateral compromise,” Vengerik says.
The consultant says Fin5 uses a rare backdoor codenamed Tornhull and a VPN dubbed Flipside to maintain persistence.
The VPN was missed in an initial attempt at detection by a rival incident response company which was called in before Mandiant. The attackers noticed the VPN’s survival and came back in the dying months of last year to drain more credit cards.
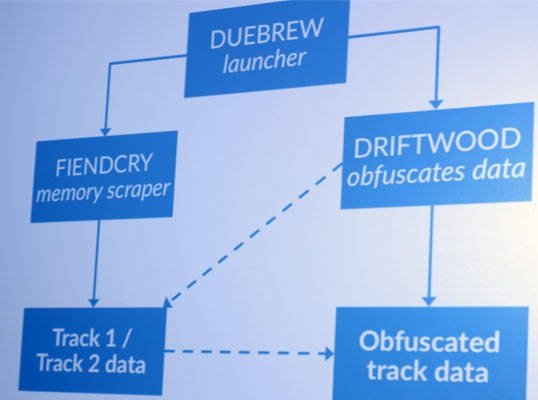
Another Fin5 custom tool codenamed “Driftwood” parses designated locations for credit card data dumps created by tools FiendCry and XOR, and encodes it for later collection.
That tool is unique in that it is “incredibly well commented”, Vengerik says, akin to the level of commentary seen in commercial software.

Fin5, no relation to other designated FIN attack groups, would mop up any residual malware and tools, then wipe logs if it suspected it had been rumbled.
Mandiant relied on the AppCompatCache to gain insight into how systems were targeted.
The casino has now implemented two factor authentication, application whitelisting, and increased logging as part of a laundry list of changes
Source:https://regmedia.co.uk/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











