HDRoot is the work of the Winnti APT group. Hackers activating mainly in South-East Asia have developed a new bootkit trojan, which disguises as Microsoft’s built-in Net command to avoid detection.
The threat was discovered by Russian-based Kaspersky Labs security vendor, which goes on to say that the bootkit seems to be an evolution from the HDD Rootkit, a similar tool that was first detected way back in 2006.
This new version was dubbed HDRoot due to its close similarities with the original rootkit and is deployed by an advanced persistent threat (APT) known under the name ofWinnti Group, active since 2009.
HDRoot is used primarily against targets in South Korea
Kaspersky says that the bootkit is actively exploited in the wild, and after it was first detected and blocked, Winnti hackers quickly made modifications to HDRoot’s codebase as a response.
Security researchers report that most attacks with HDRoot have been observed in South Korea, but that targets in the UK and Russia have also been hit.
“The development of the HDD Rootkit is likely to be the work of someone who went on to join the Winnti group when it was set up,” Kaspersky Lab researchers say, hinting at the fact that HDRoot may be the job of someone who previously worked on the original bootkit.
HDRoot is hiding in plain sight
How this particular bootkit works is by hiding inside a modified version of the Net Command utility, net.exe. Functionality is not altered, so users running net.exe won’t notice anything wrong.
This file is suspicious nevertheless, mainly because it’s signed using a certificate issued to Chinese firm Guangzhou YuanLuo Technology, which reported it as compromised a while back.
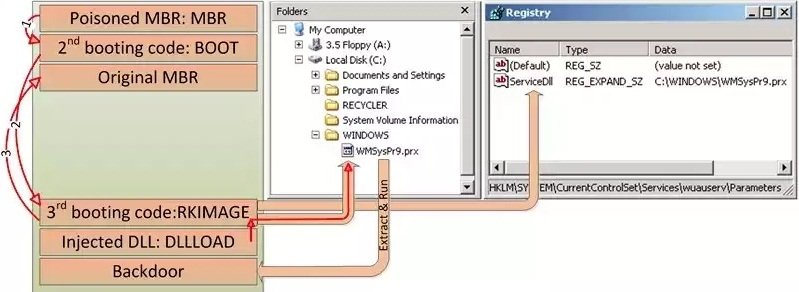
This is the entry point to infected systems, allowing it to compromise the target’s hard-drive MBR (Master Boot Record), and from there, download and launch any other malicious malware.
HDRoot is used to launch backdoors into the computers of infected users
In the HDRoot samples it could analyze, Kaspersky observed that the bootkit launched two backdoors. To do this, it used two methods.
The first consisted in loading the backdoors using a compromised svchost.exe process, which was visible to AV products, while the second worked as a memory-hosted exploit, much more difficult to detect.
Besides the precautionary measures, HDRoot’s creator took to hide the bootkit in its initial stages of infection, and most specifically not to block or delay the OS from booting, Kaspersky’s researchers say that the bootkit cripples some other Windows services, like Windows Update or Task Scheduler, which cease to work altogether.
Additionally, antivirus engines could also detect the presence of HDRoot on a system using some other clues left behind by the bootkit, like wrong registry path and value names, and mistakenly overwritten some registry data.
Kaspersky said its antivirus product is able to detect HDRoot.

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.