VBA stands for Visual Basic for Applications and is a programming language developed by Microsoft to help programmers create Windows applications using an easy-to-understand coding syntax.
According to a research carried out by Graham Chantry from Sophos, more and more hackers are turning to Visual Basic as a way to deliver their malware using Microsoft Word documents.
By hiding VBA code inside Word files, attackers are taking advantage of the working habits of millions of employees around the world, who regularly receive and open Word documents without ever thinking twice about it.
New VBA malware is detected on a regular basis
According to the Sophos research, there are hundreds of VBA malware templates on the Dark Web which attackers can download, bottle up inside .doc or .docx files, and then send them to victims via spam or spear-phishing campaigns.
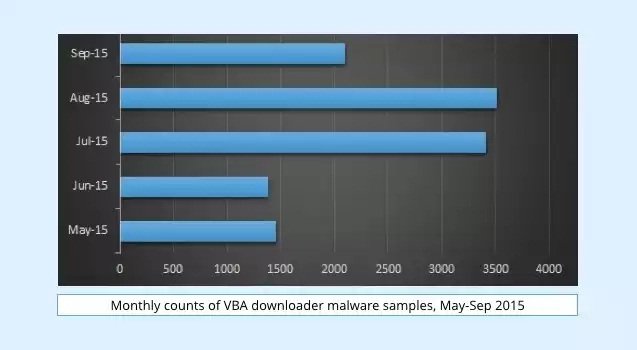
In fact, the number of new VBA malware samples Sophos discovers each month is around 50 to 100, which is quite impressive for such an ancient technology.
As the Sophos team reports, in most cases, the malware only acts as a downloader for more potential threats, mainly because it is much easier to bundle it inside Word documents than using other more complex exploits like the Word macro vulnerability.
Most of the times, VBA malware was used to download the Dridex malware, the CryptoWall ransomware, and even lesser-known malware like Dyreza and Zbot.
But Word files are not the only places where this adversary hangs out, researchers also claiming that they’ve seen trends for small time periods during which the attackers also tried to bundle VBA malware with other file formats. Sophos reports on the Office 2003 XML format, MHTML, RTF, and even PDF.
Additionally, as more and more VBA malware strands started appearing, the code also increased in complexity, and even started to come obfuscated out of the box.
VBA malware sends antivirus engines on a carousel ride
Besides coming hidden to make reverse engineering even harder and more time-consuming, researchers also started seeing the VBA malware code making unusual calls to lesser used system functions, calls which were also made to run in very long and time-wasting loops.
The purpose of this operation was to make the malware code execute in a much longer timeframe, which would make it very hard for antivirus engines to detect it as malicious.
By taking more time to scan, some antivirus solutions would drop the scanning operation due to limited resources or because of built-in procedures that would deem the scan as inconclusive. An antivirus vendor would like to avoid situations where their product scans a file for a few minutes or hours, but an attacker has everything to gain, even if their malware executes now, in 5 minutes, 2 hours, or the next day.
Source:https://news.softpedia.com/

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.










