Symantec’s researchers have discovered a new version of the Kovter trojan, which now mimics the Poweliks malware and is able to live on your computer’s registry, without needing to be stored on your hard drive.
Kovter, first spotted in 2013, has been one of the most updated malware families around, constantly changing its MO, adapting to new hacking campaigns and to the security measures put in place to stop it.
According to Symantec, starting with version 2.0.3 of the Kovter malware, first spotted in the wild in May 2015, the trojan borrowed survival methods from Poweliks and can hide itself in the PC’s registry.
The registry is a Windows-specific feature, a database of data about user profiles, settings, software, and hardware, which the Windows OS is using on a regular basis.
By storing its code in the registry, Kovter lasts longer on infected machines and serves as an entry point for other more serious infections.
Despite its powerful stealth features, Kovter is misused for click-fraud
While in the past Kovter has been known to go hand in hand with ransomware, Symantec says that now, in its deadlier form, Kovter is only focused on click-fraud.
As for the way it initially infects users, Symantec says that attackers are distributing this new version of Kovter mainly via malvertising campaigns and file attachments in spam email.
In the past, the Angler, Fiesta, Nuclear, Neutrino, and the Sweet Orange exploit kits have been used to spread the malware, so don’t rule them out either.
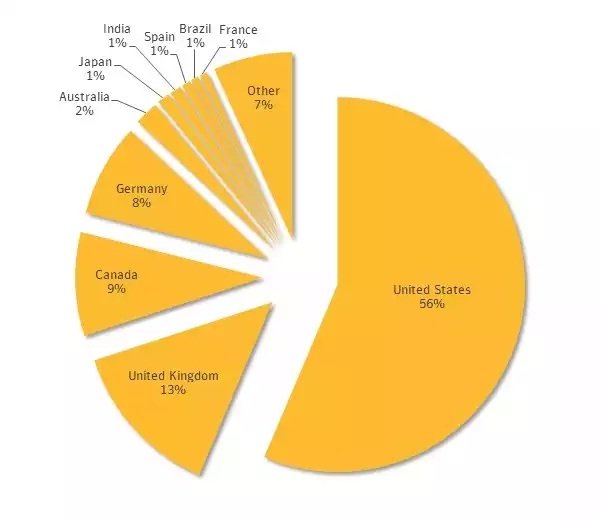
In its most recent outbreak, Symantec reports that the malware has been predominantly infecting users in the US (56%), UK (13%), Canda (9%), Germany (8%), and Australia (2%).
“The Kovter malware family has continually evolved since it was first discovered and shows no signs of leaving the threat landscape anytime soon,” Symantec researchers predict.
To help users infected with the Kovter malware, Symantec is providing the Trojan.Kotver Removal Tool as a free download.
Source:https://news.softpedia.com/

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.