Android devices may be protected by a lock screen which requires some form of authentication before access to most phone features, its settings and the data stored on it is granted.
Users may protect the phone by password, pin or pattern for example, and there are other means of protection available as well, for instance by using Bluetooth device authentication or unlocking it based on locations you are in.
If you have set a password on your Android device and you are running Android 5.x, your phone is vulnerableto a lockscreen bypass attack.
The attack itself is surprisingly easy to carry out:
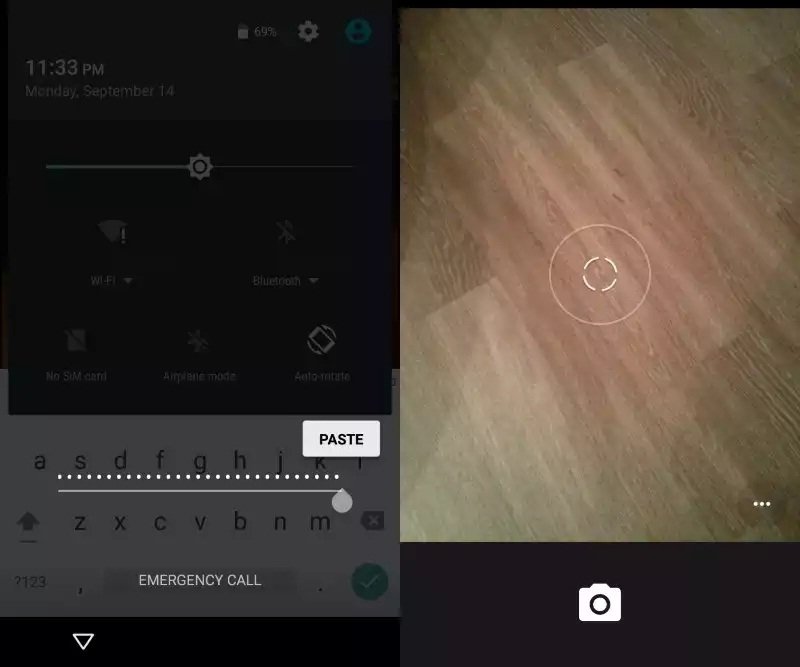
- Open the Emergency Call screen on the phone.
- You need to enter a long number there with lots of chars. The researchers suggested to start with 10 asterisks and then doubling these characters using copy and paste until this is no longer possible (the field is not highlighted anymore).
- Go back to the homescreen afterwards and open the camera application on the device.
- Swipe down to display the notifications drawer and tap on settings. This opens a password prompt automatically.
- Paste the same characters that you used in the Emergency Dialer into the password field. Repeat this process until the UI crashes (the buttons at the bottom of the screen disappear and the camera is displayed fullscreen.
- The camera will crash eventually as well and the homescreen is displayed. The phone is unlocked and you have full access to all apps and data on it.
This attack works only if a password is used to protect the Android device. It won’t work with pattern or pin locks. If you are using a password-based lock currently you may want to switch to pin or pattern-based instead for the meantime to protect your device from this attack.
The following video demonstrates the attack.
The Android developers have fixed the issue already but it takes time before the fix lands on affected devices.
Attackers need to have physical access to the device to carry out the attack. While that is a limitation, it is still recommended to not use password-based locks on Android 5.x devices until the vulnerability has been patched on affected devices.
Source:https://www.ghacks.net/

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.