Infected owners must choose between paying $500 and performing factory reset.
Malicious apps that disable Android phones until owners pay a hefty ransom are growing increasingly malevolent and sophisticated as evidenced by a newly discovered sample that resets device PIN locks, an advance that requires a factory reset.
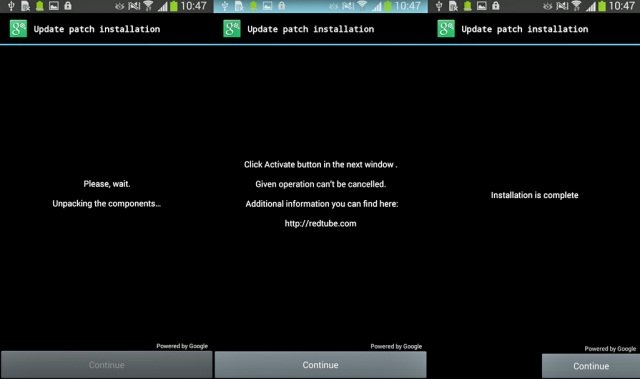
Dubbed Android/Lockerpin.A, the app first tricks inexperienced users into granting it device administrator privileges. To achieve this, it overlays a bogus patch installation window on top of an activation notice. When targets click on the continue button, they really grant the malicious app elevated rights that allow it to make changes to the Android settings. From there, Lockerpin sets or resets the PIN that unlocks the screen lock, effectively requiring users to perform a factory reset to regain control over the device. By contrast, earlier forms of Android ransomware generally were thwarted, usually by deactivating administrator privileges and then uninstalling the app after the infected device is booted into safe mode.
“After clicking on the button, the user’s device is doomed,” Lukas Stefanko, a researcher with antivirus provider Eset, wrote in a blog post published Thursday. “The trojan app has obtained administrator rights silently and now can lock [the] device—and even worse, it set[s] a new PIN for the lock screen. Not long after, the user will be prompted to pay a $US500 ransom for allegedly viewing and harboring forbidden pornographic material.”
Experienced Android users would likely be suspicious of the fake update windows at the top of this post, but it’s entirely plausible newer users would fall for them. Once the continue button is pressed, the app will acquire administrator rights. From there it will change the PIN and periodically continue to overlay a fake window in an attempt to hold on to the elevated privileges. It’s the first known Android lock-screen ransomware to set a phone’s PIN lock. Because it requires non-paying victims to factory reset their phones, it causes them to lose all of their data.
At the moment, the app is notable mostly for the innovation it shows rather than the real-world threat it poses. That’s because it’s distributed in third-party app stores and masquerades as an app for serving pornography. Still, it wouldn’t be surprising to see this type of app evolve further. If it were to find its way into the official Google Play market—as happens regularly with malicious Android apps—it could represent a real threat for a much larger number of people.
Source:https://arstechnica.com/

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.