A group of hackers that goes under the name of DD4BC, first spotted in September 2014, has recently intensified its activity, launching over 141 DDOS attacks in the past year.
The group, identified and analyzed by Akamai’s Prolexic Security Engineering and Response Team (PLXsert), has been very busy in the past few months, launching numerous DDOS attacks against several Akamai clients, and requiring payments in Bitcoin to stop their operation.
Most of their attacks targetted Akamai clients operating in the financial sector, where there are higher chances of extracting a Bitcoin payment when compared to other industries.
This is because companies with a financial scope tend to have bigger losses for every minute of downtime, when compared to other entities operating in healthcare, tourism, telecom, or various other domains.
According to Akamai’s report, most of the attacks employed packet floods via protocols like NTP (Network Time Protocol), SSDP (Simple Service Discovery Protocol), UDP (User Datagram Protocol), TCP (Transmission Control Protocol, via SYN and/or GET floods), ICMP (Internet Control Message Protocol), DNS (Domain Name System), and SNMP (Simple Network Management Protocol).
Additionally, researchers also observed DD4BC use a vulnerability in the WordPress pingback function, to trigger DDOS attacks from various WP sites around the Web.
Attacks were small in size, averaged around 13 Gbps
DDOS attacks did not reach extremely high values, but generally averaged 13.34 Gbps, with the largest one being recorded at 56 Gbps.
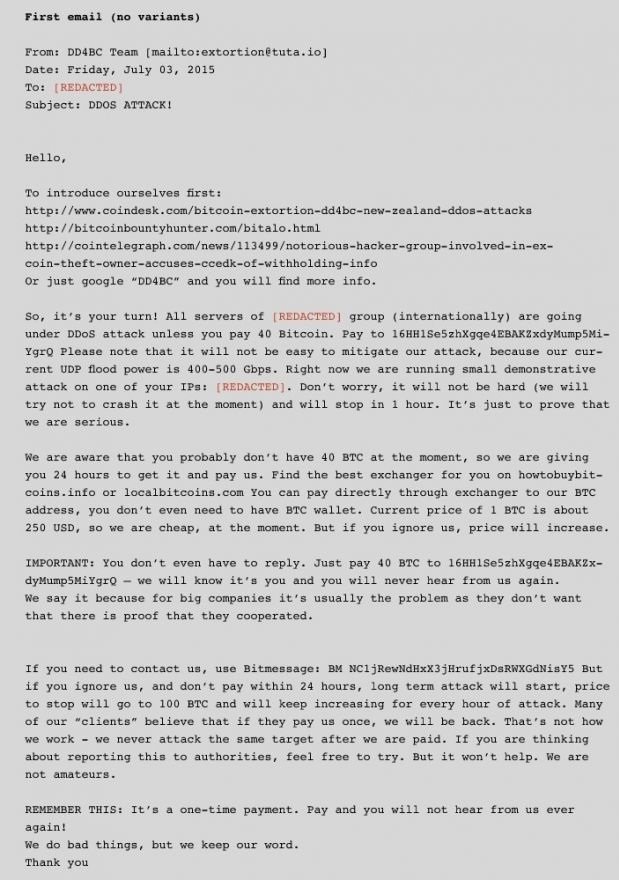
The normal method of operation during a DD4BC attack was to first send a ransom email, the group introducing itself using one of Akamai’s own previous blog posts about their activities, and then to ask the company for a Bitcoin payment.
These usually ranged from 25 to 100 Bitcoin, which is about $6,000 – $24,000 (€5,350 – €21,400).
Social media shaming was also part of their blackmail routine
If payments were not sent, besides triggering the DDOS attack, DD4BC also threatened the company with public disclosure, usually on social media, which had the potential to damage their reputation.
Since DDOS attacks are so common these days, there’s a general train of thaught saying that if you’re a professional company, you should have powerful mitigation solutions already in place.
Akamai did not report if any companies ended up paying the blackmail, but they said they blocked at least 75 out of all the 141 DDOS attacks recorded via its servers.
Since the report only includes data from Akamai’s own servers, chances are that the true number of DDOS attacks is many times higher.
Source:https://news.softpedia.com/

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











